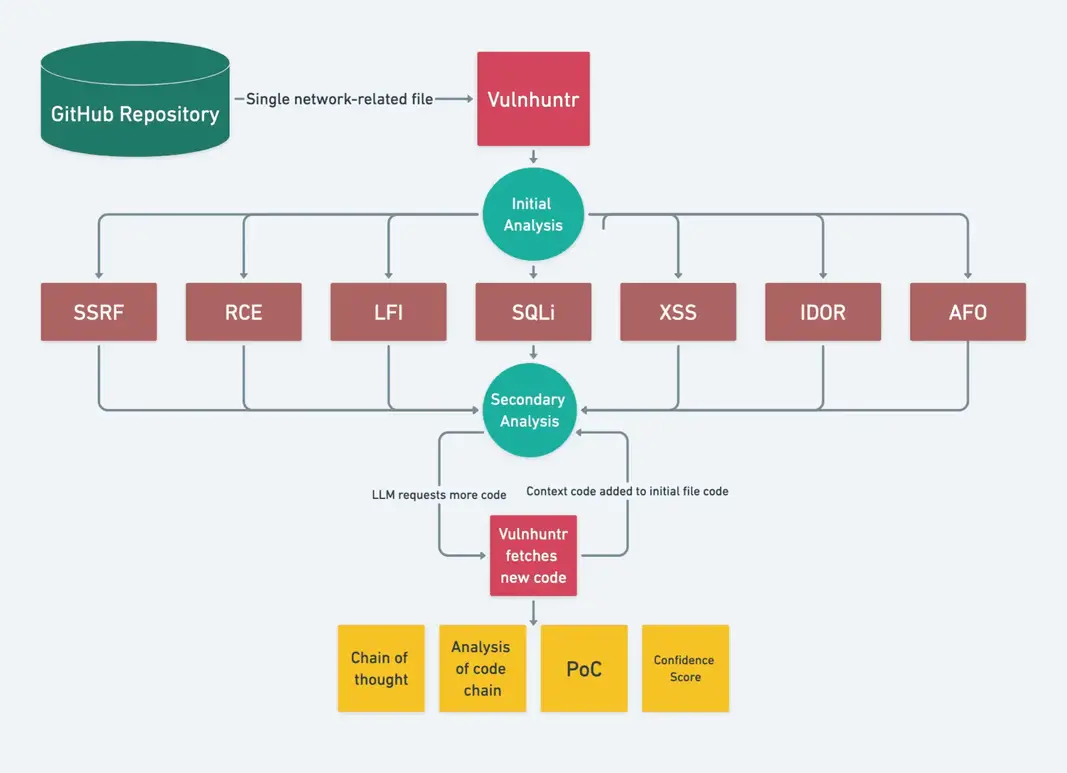
CVE-2024-9537 (CVSS 9.8): Critical Zero-Day in ScienceLogic EM7 Leads to Rackspace Security Incident
Rackspace, a leading provider of managed cloud services, announced a security incident related to a zero-day vulnerability discovered in a third-party utility bundled with the ScienceLogic EM7 (SL1) monitoring platform....