Auditor v76 releases: Hardware-based attestation/intrusion detection app for Android devices
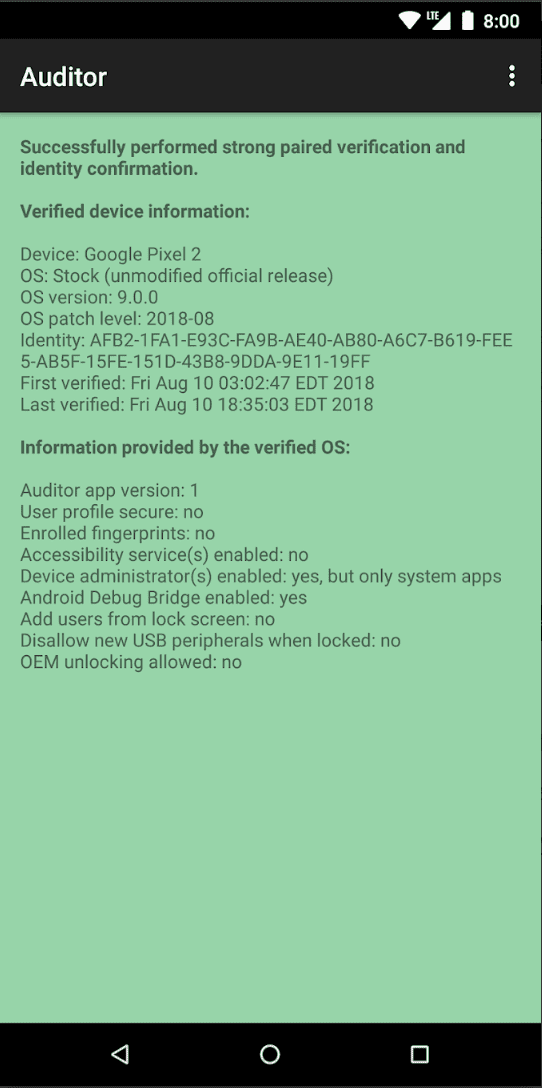
The Auditor app uses hardware-based security features to validate the identity of a device along with the authenticity and integrity of the operating system. It will verify that the device is running the stock operating system with the bootloader locked and that no tampering with the operating system has occurred. A downgrade to a previous version will also be detected. It builds upon the hardware-based verification of the operating system by chaining verification to the app to perform software-based sanity checks and gather additional information about device state and configuration beyond what the hardware can attest to directly.
The foundation of the Auditor app is generating a persistent key in the hardware-backed keystore for verifying the identity of the device and providing assurance that the operating system hasn’t been tampered with or downgraded via the verified boot. It performs a pairing process between the device performing verification (Auditor) and the device being verified (Auditee) to implement a Trust On First Use (TOFU) model. The device performing verification can either be another Android device running the app in the Auditor mode or the https://attestation.app/ service for automated verification on a regular schedule with support for email alerts.
Changelog v76
Notable changes in version 76:
- add support for Pixel 8 and Pixel 8 Pro
- update Guava library to 32.1.3
Install & Use
Copyright (c) 2019 Daniel Micay