Image Credit: @privacyis1st
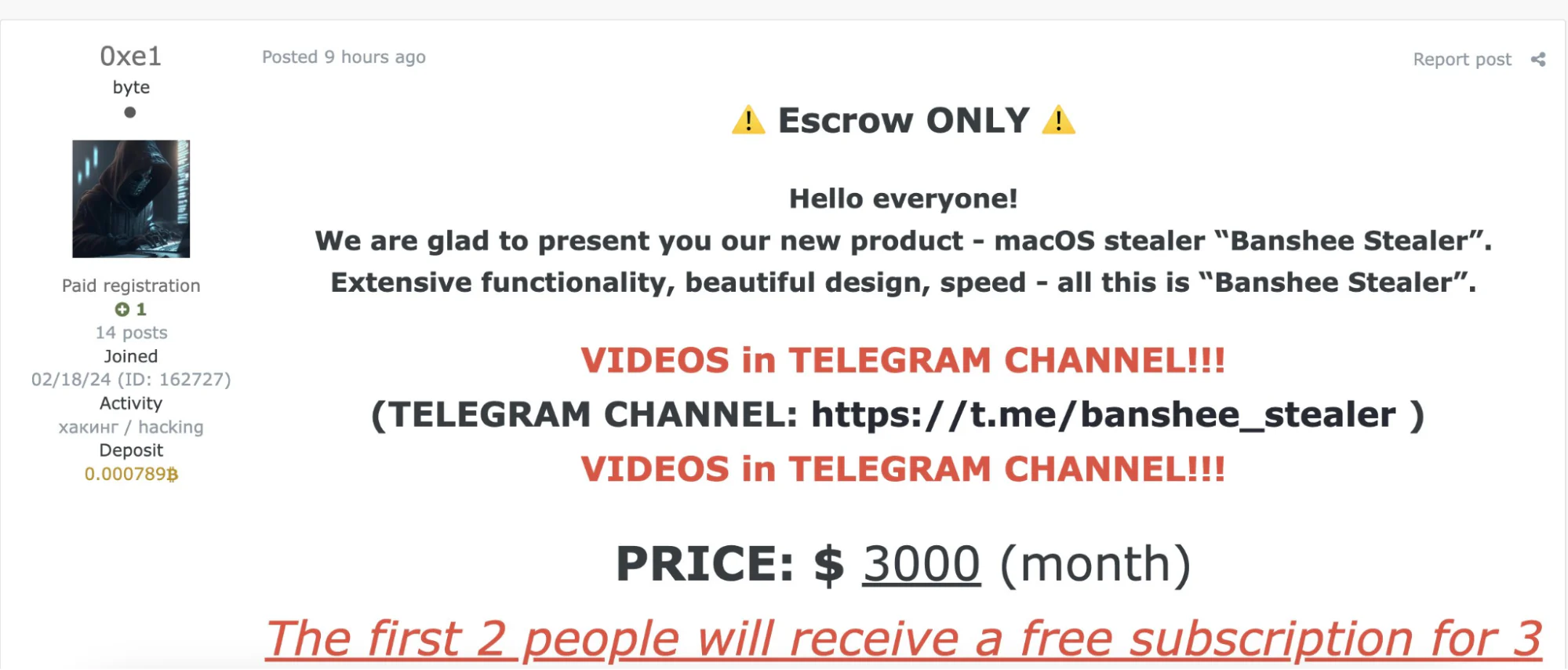
Security researchers warn of a new macOS malware, BANSHEE Stealer, which has recently emerged in underground forums. Developed by Russian threat actors and introduced on an underground forum, this malware is making waves due to its sophisticated targeting of macOS users and its steep subscription price of $3,000 per month. As macOS becomes an increasingly attractive target for cybercriminals, BANSHEE Stealer underscores the growing threat to users of Apple’s operating system.
BANSHEE Stealer is not your average piece of malware. Unlike many Windows-based stealers that have long dominated the market, BANSHEE is specifically designed to infiltrate macOS systems, whether they run on x86_64 or ARM64 architectures. This cross-architecture capability makes it a versatile and potent tool in the hands of cybercriminals.
The malware targets critical system information, browser data, and cryptocurrency wallets, putting macOS users at significant risk. With the ability to collect data from a wide range of browsers and around 100 browser extensions, BANSHEE Stealer is a formidable adversary for even the most security-conscious users.
Upon examining BANSHEE Stealer, analysts were intrigued to find that the malware contained all its C++ symbols, providing insights into the project’s code structure. This level of transparency, while unusual, allowed researchers to identify key details, such as the remote IP addresses, encryption keys, and build IDs used during the malware’s development.
BANSHEE Stealer employs several basic yet effective techniques to evade detection. It uses the sysctl API to detect debugging attempts and checks for virtual machine environments by analyzing the system’s hardware identifiers. Additionally, the malware avoids infecting systems where Russian is the primary language, a common tactic used by threat actors to steer clear of their own country’s users.
Once BANSHEE Stealer has gathered the desired information, it compresses the collected data into a ZIP file using the ditto command. This file is then XOR encrypted, base64 encoded, and sent to a remote server via a POST request. The server, hosted at http://45.142.122[.]92/send/, receives the stolen data, completing the malware’s attack cycle.
As the macOS ecosystem expands, cybercriminals are increasingly targeting its users. The discovery of BANSHEE Stealer serves as a reminder that robust security measures and proactive defenses are essential in safeguarding macOS environments.