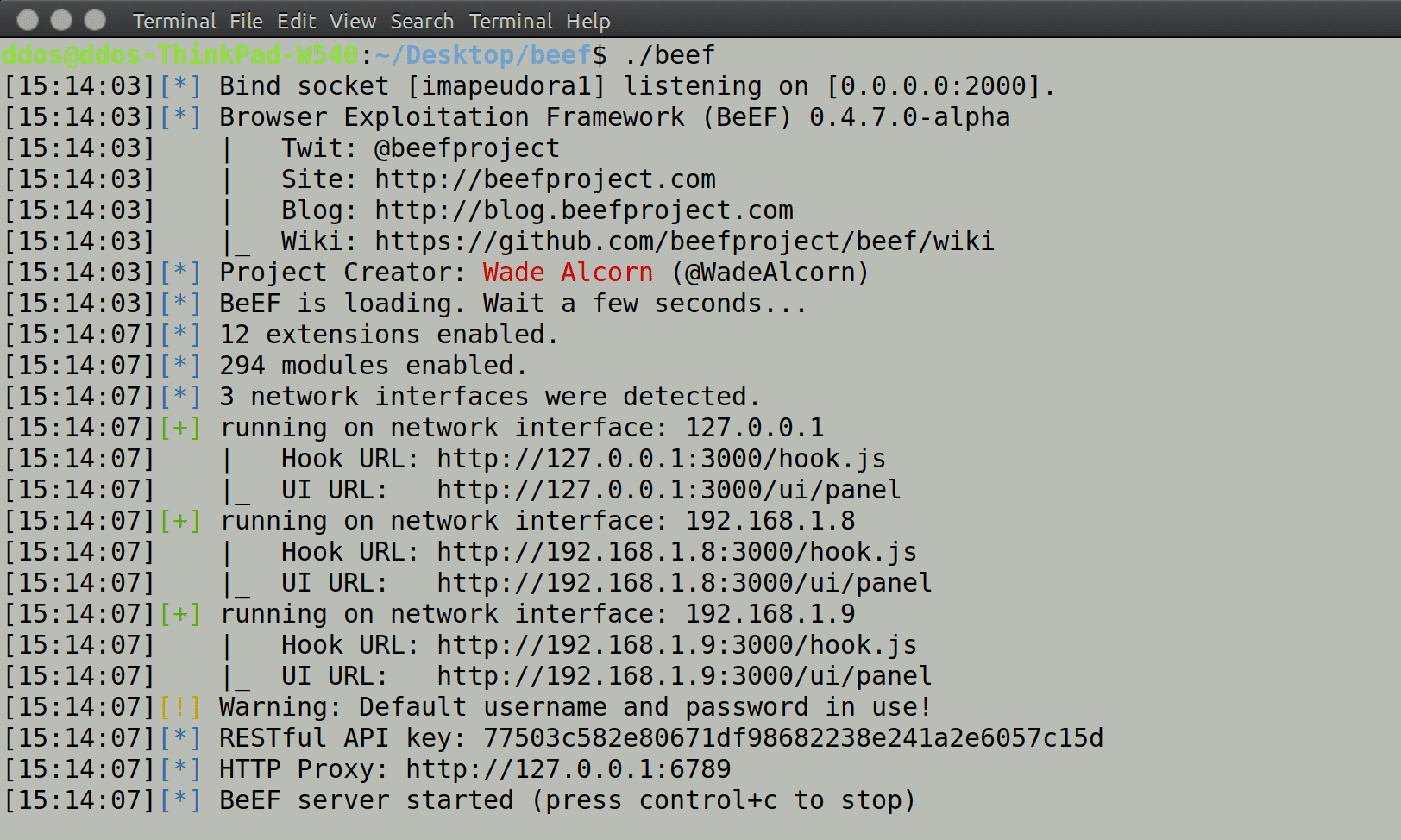
beef v0.5.4 releases: The Browser Exploitation Framework
BeEF is short for The Browser Exploitation Framework. It is a penetration testing tool that focuses on the web browser.
Amid growing concerns about web-borne attacks against clients, including mobile clients, BeEF allows the professional penetration tester to assess the actual security posture of a target environment by using client-side attack vectors.
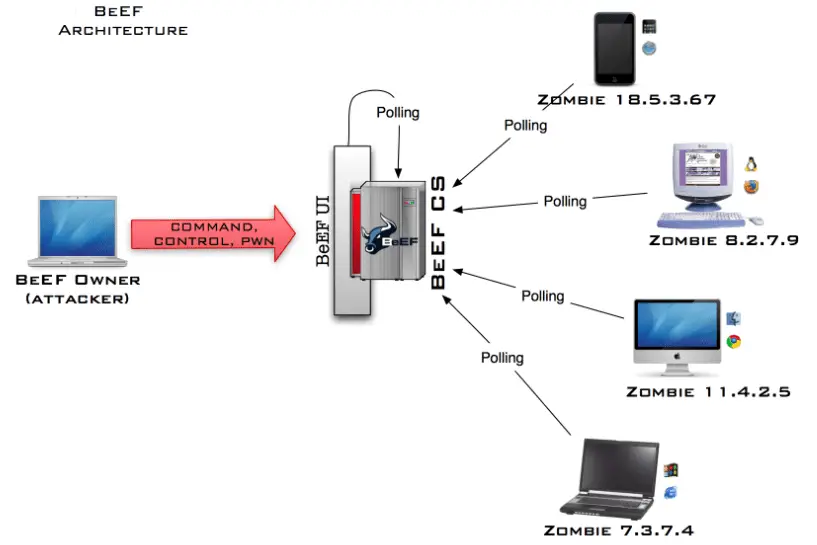
Browser Exploitation Framework (BeEF) hooks one or more web browsers as beachheads for the launching of directed command modules. Each browser is likely to be within a different security context, and each context may provide a set of unique attack vectors. The framework allows the penetration tester to select specific modules (in real-time) to target each browser, and therefore each context.
The framework contains numerous command modules that employ BeEF’s simple and powerful API. This API is at the heart of the framework’s effectiveness and efficiency. It abstracts complexity and facilitates quick development of custom modules.
The following diagrams and explanations should explain how BeEF works and the different ways you can use it. This page will be updated as new functionality is introduced in each release.
High Level
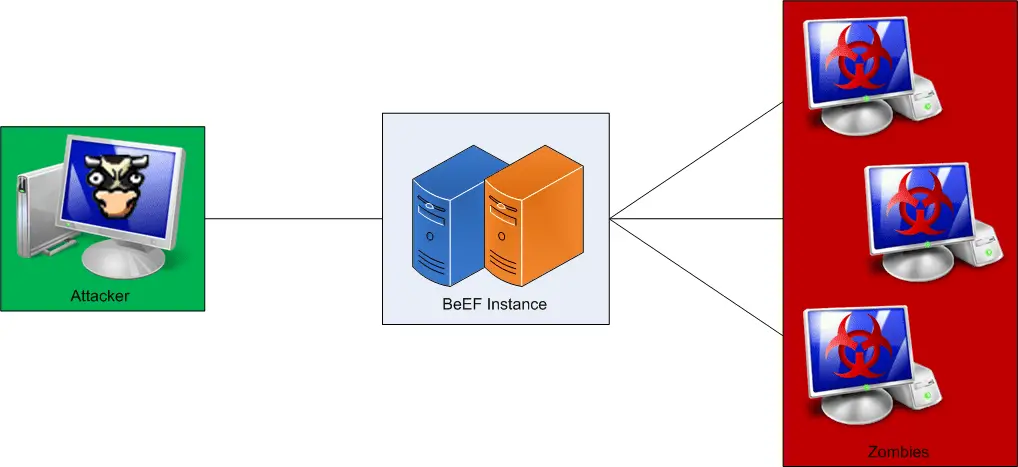
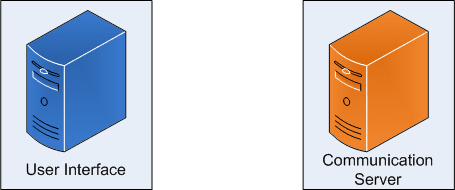
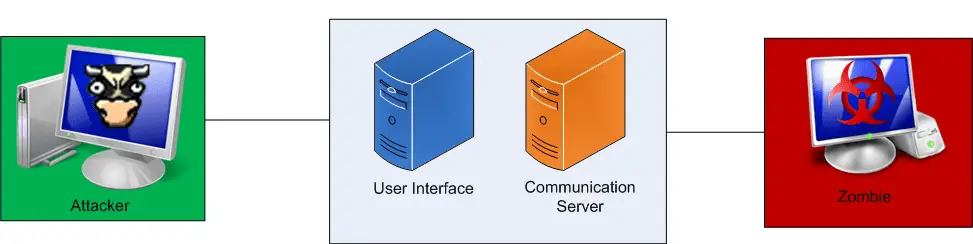
When a user runs up BeEF currently, there are two components started: the User Interface and the Communication Server. These two components are the base components of BeEF and are discussed in detail below.
Components
User Interface
This is the control interface for using BeEF. From here a user can see all online and offline browsers, run exploits against them and see the results (Pattern 1).
Communication Server
This guy is essential to how BeEF works. The Communication Server (CS) is the component that communicates via HTTP with the hooked browsers.
Usage Pattern 1
This is the most basic usage pattern for BeEF. An attacker simply needs to run up BeEF (beef.rb) and login directly to the UI. From here the attacker can see which hooked browsers are online and which are offline, all information collected about/from a particular hooked browser, and run exploits against online hooked browsers.
Changelog v0.5.4
Bug Fixes
Enchanciements
- #2205 – Modules – Apache Tomcat Examples Default Install Exploit
- #2157 – Maintainability – Implement GitHub Actions and added confirmation step to PRs
- #2190 – Maintainability – Improved CI workflow:
- Refactor Rakefile to accommodate Browserstack implementation
- Installer improvements
- Test suite performance improvements
- #2199 – Enhancement – Check for update on launch works with beef-xss kali package install
Install & Use
Copyright (c) 2006-2021 Wade Alcorn – wade@bindshell.net