theo v0.8.2 releases: Ethereum recon and exploitation tool
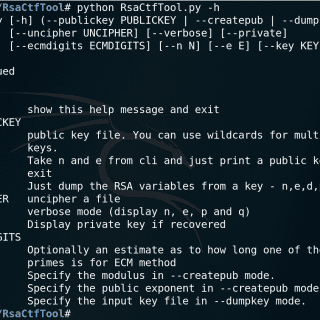
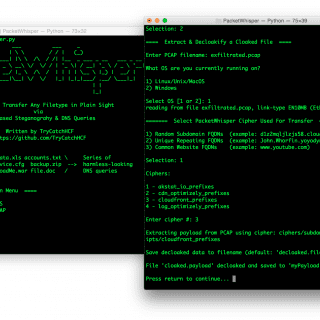
Theo Theo aims to be an exploitation framework and a blockchain recon and interaction tool. Features: automatic smart contract scanning which generates a list of possible exploits. generating and sending transactions to exploit a...