slsa v1.0 releases: Supply-chain Levels for Software Artifacts
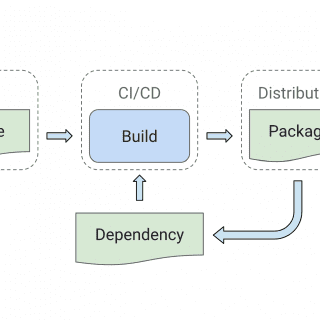
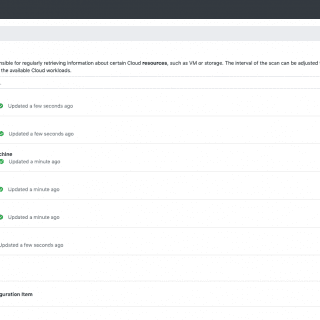
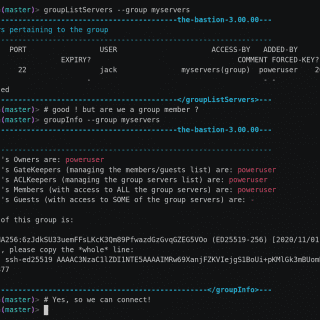
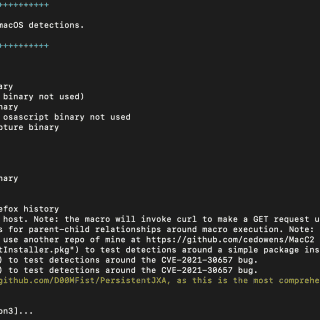
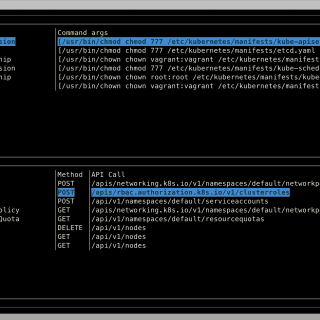
SLSA: Supply-chain Levels for Software Artifacts Supply-chain Levels for Software Artifacts (SLSA, pronounced salsa) is an end-to-end framework for ensuring the integrity of software artifacts throughout the software supply chain. The requirements are inspired by...