modDetective: investigate recent system activity tool
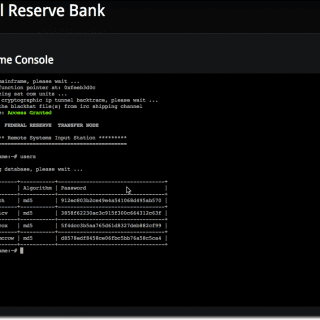
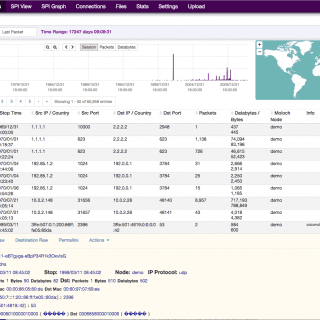
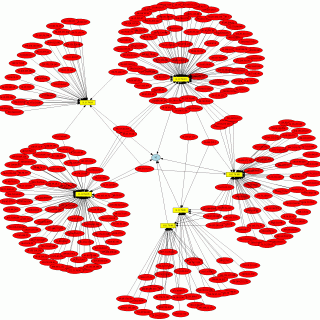
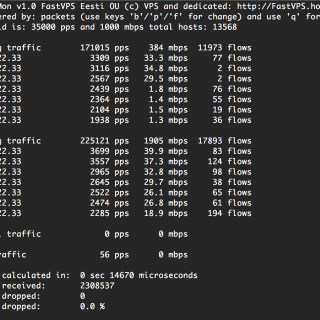
modDetective modDetective is a small Python tool that chronologizes files based on modification time in order to investigate recent system activity. This can be used in red team engagements and CTF‘s in order to...