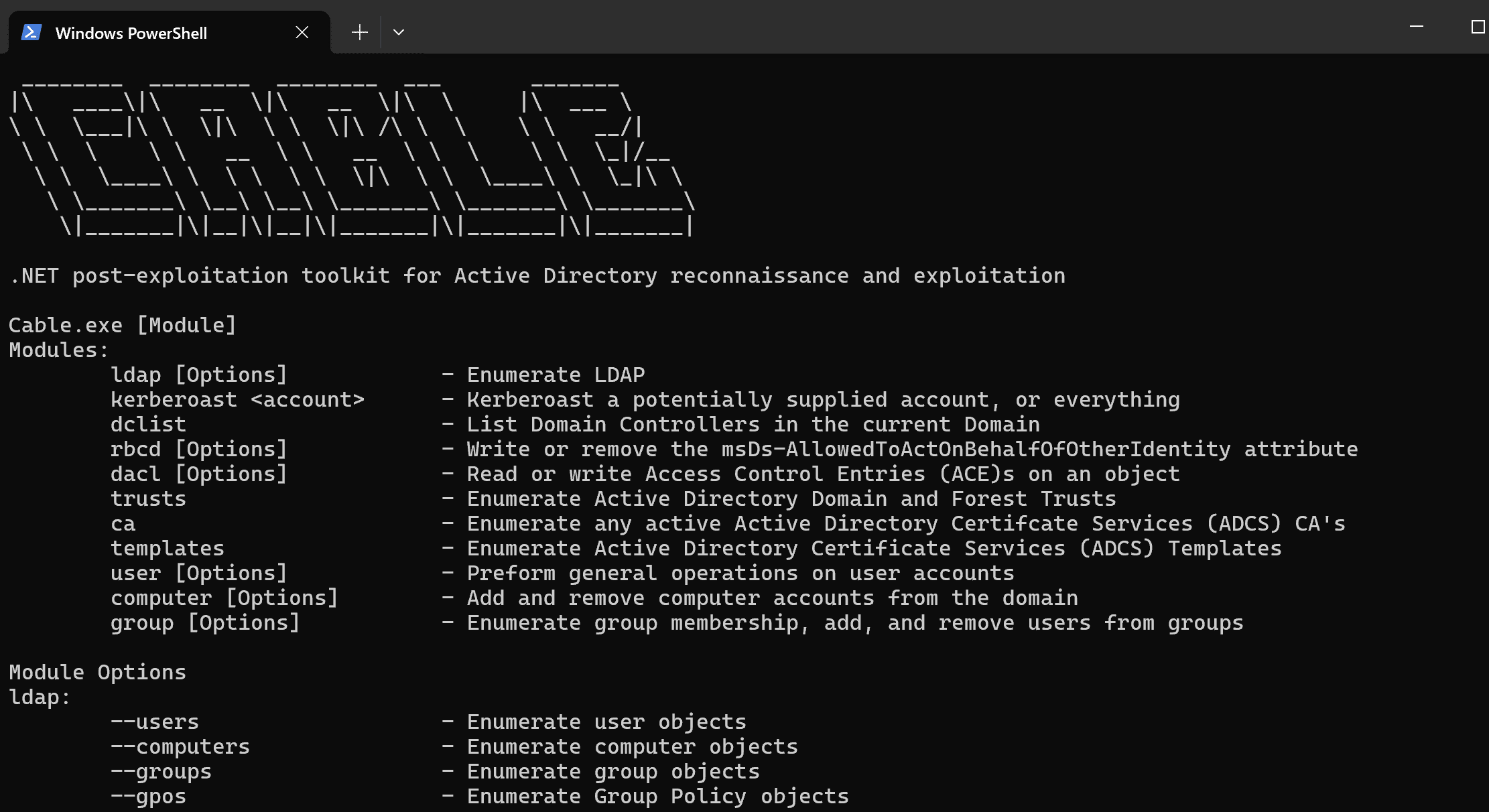
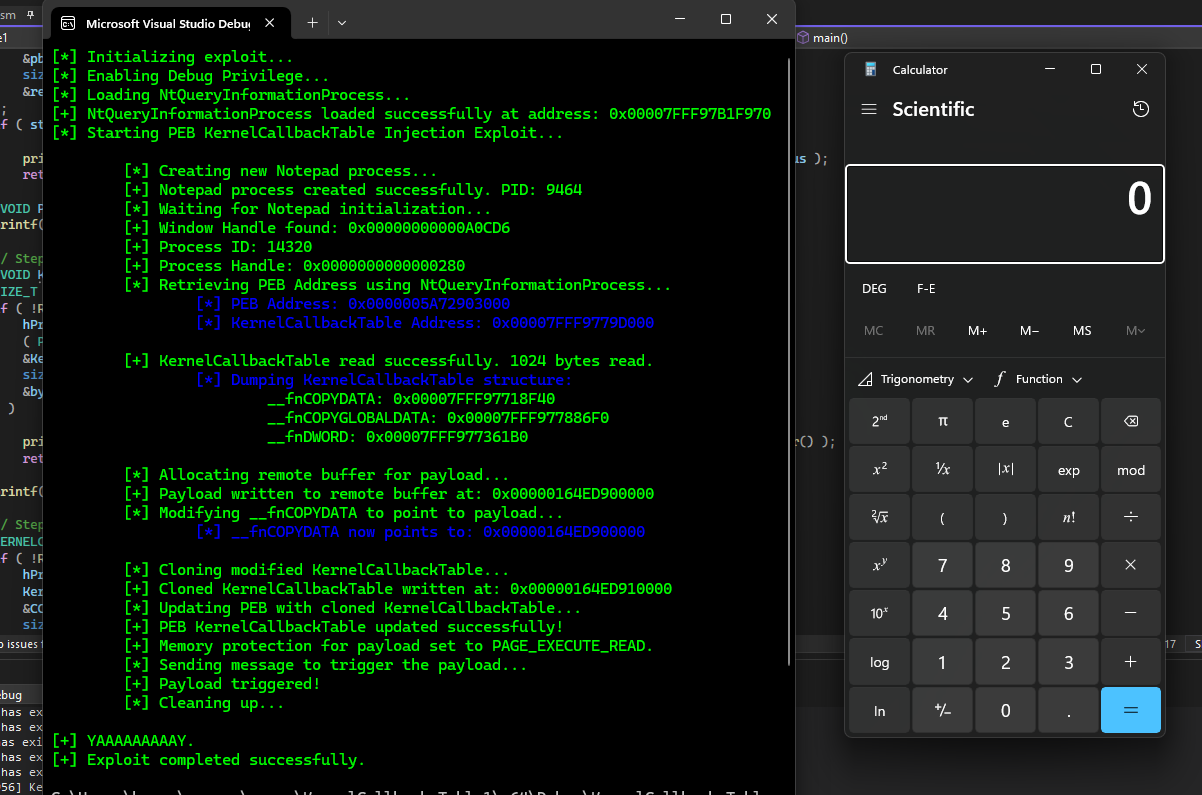
Activation Context Hijacking: “Eclipse” PoC Weaponizes Trusted Processes
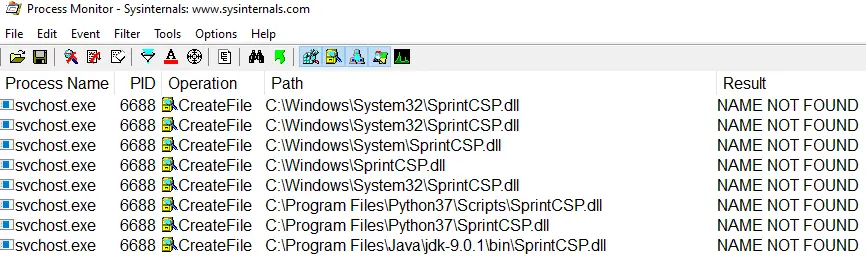
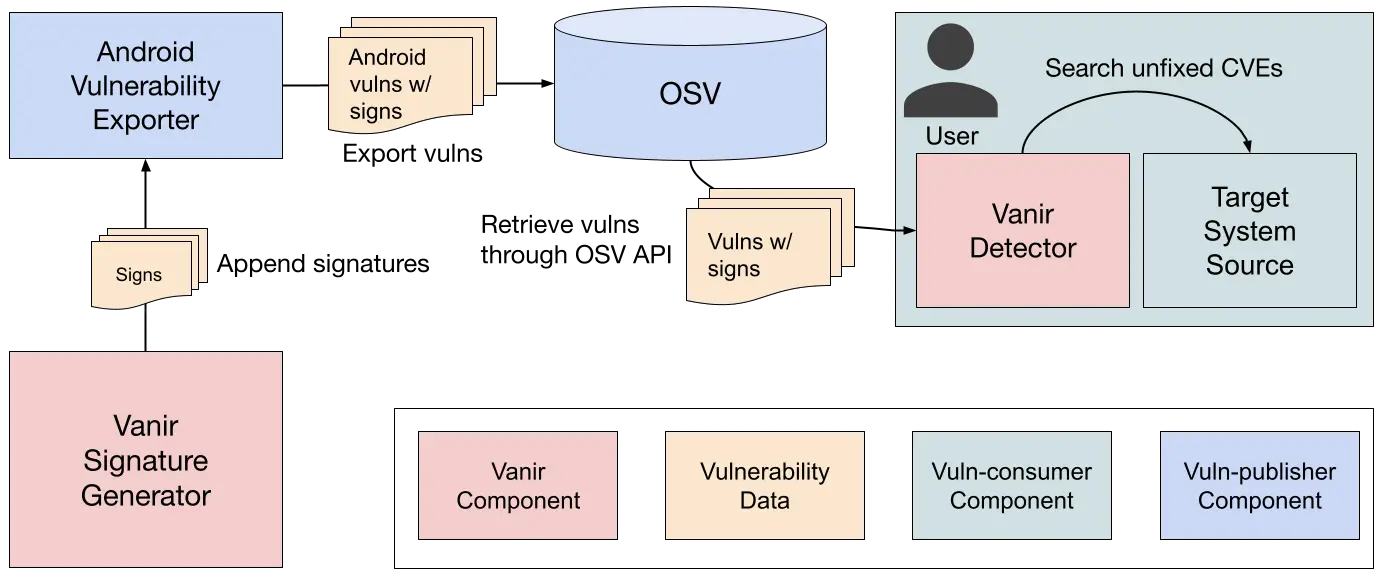
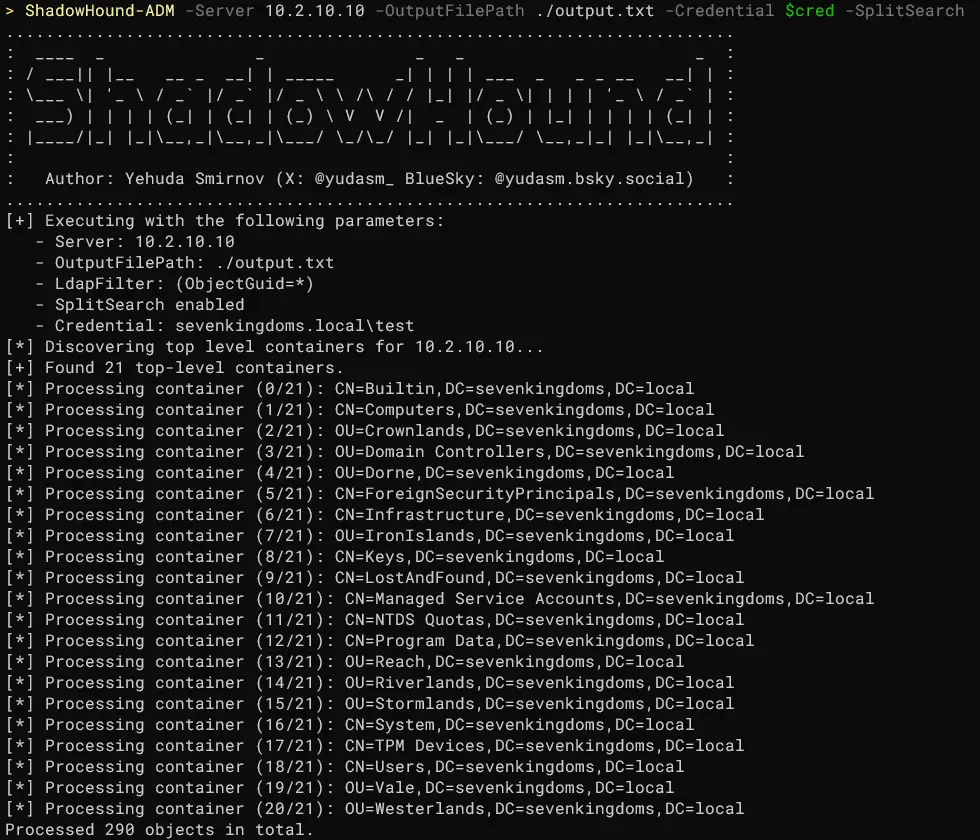
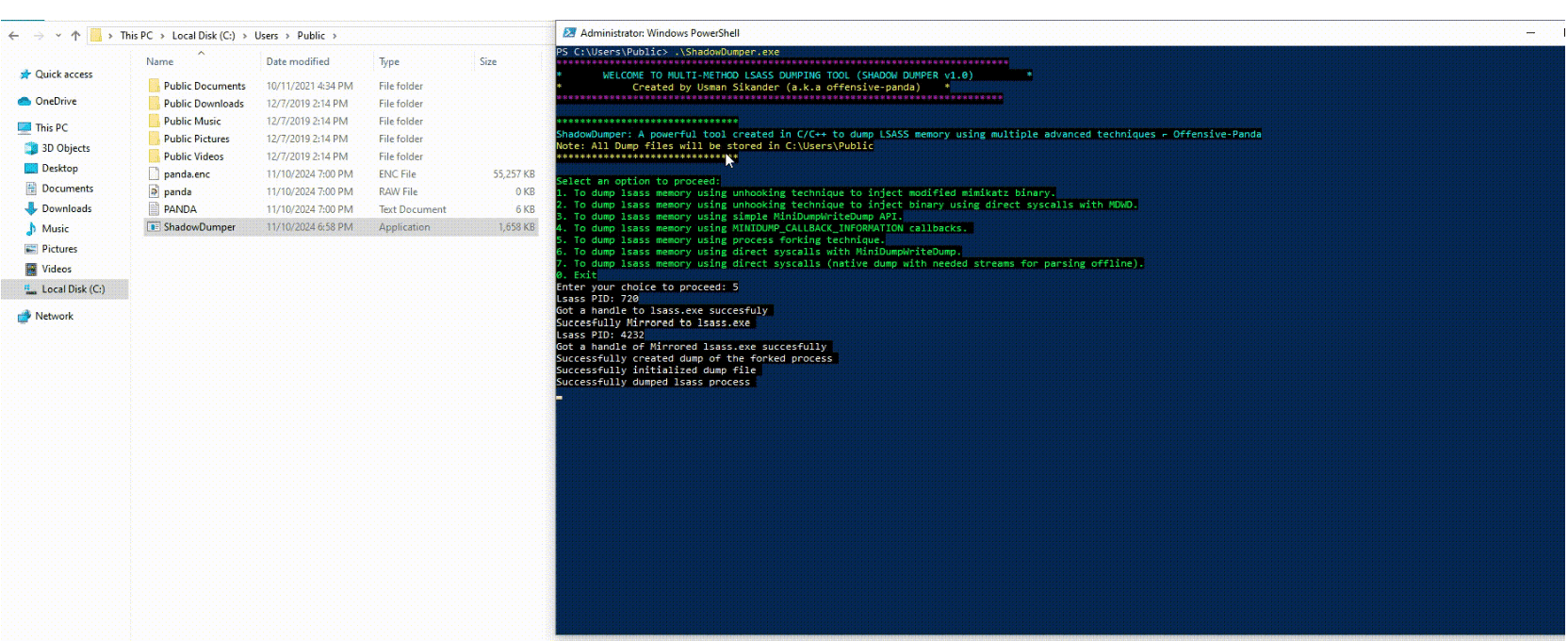
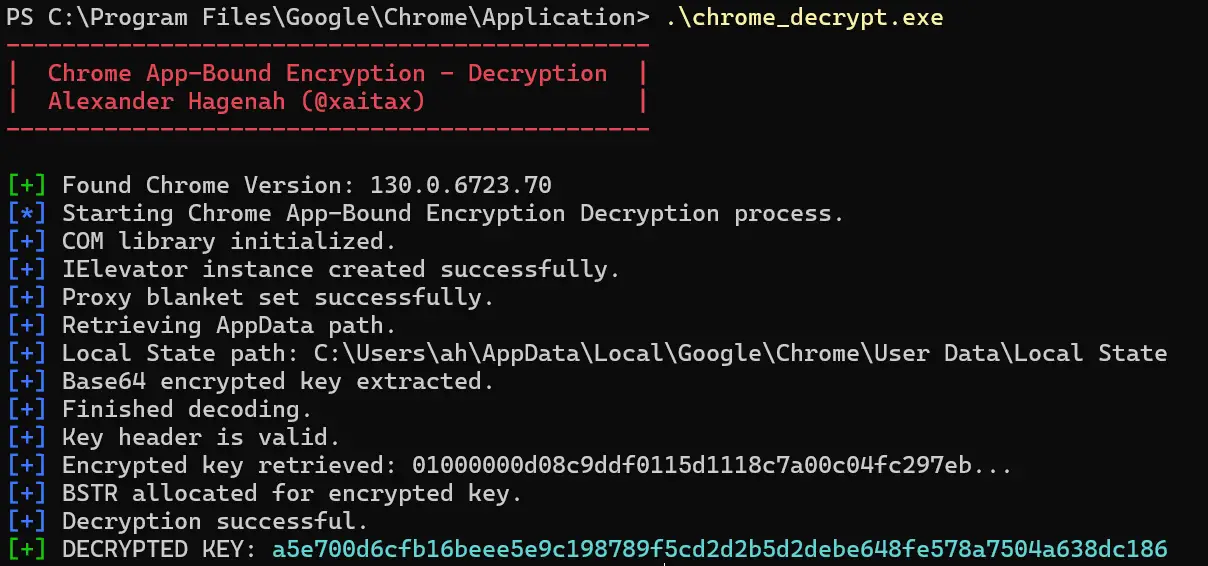
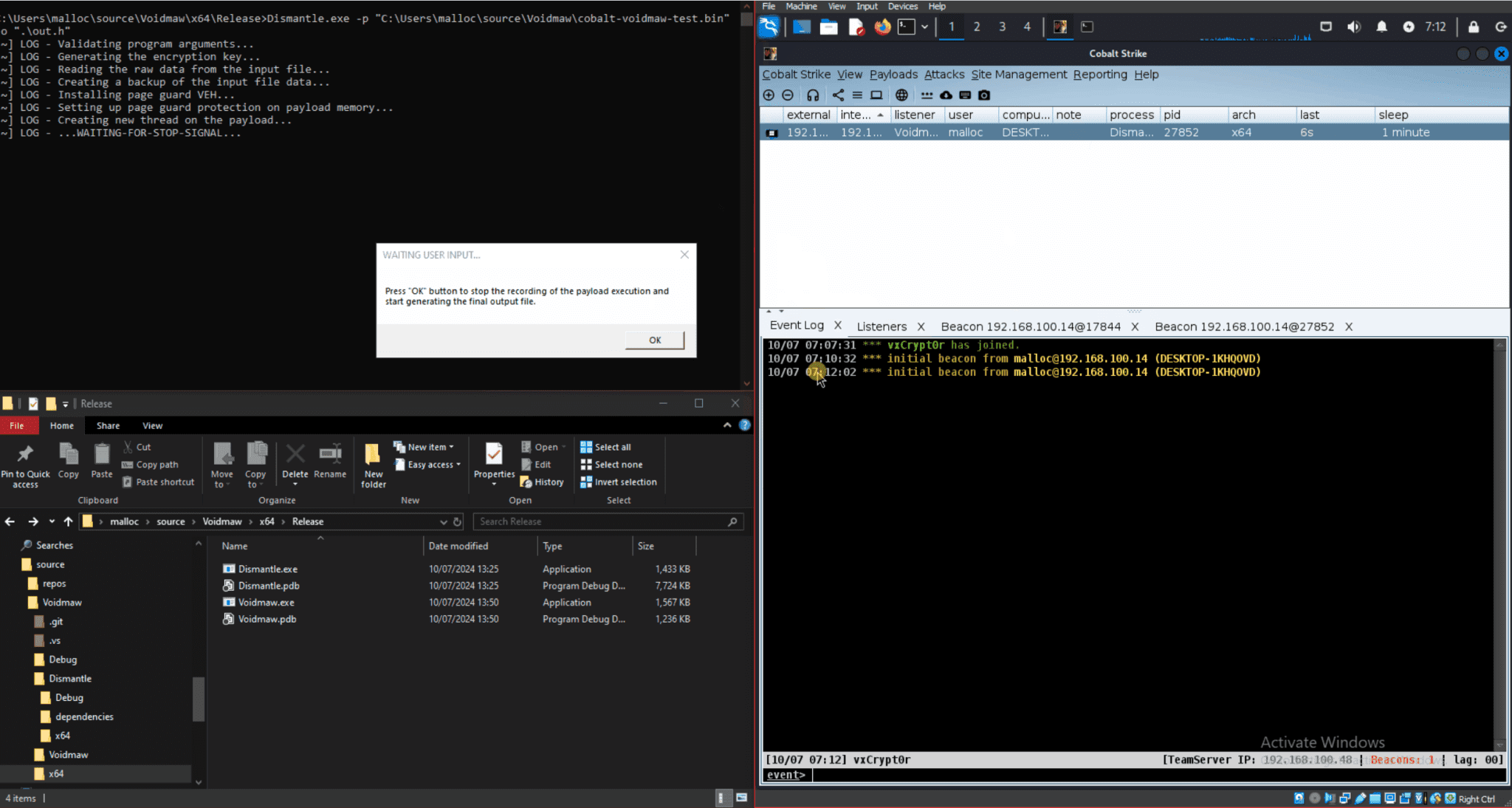
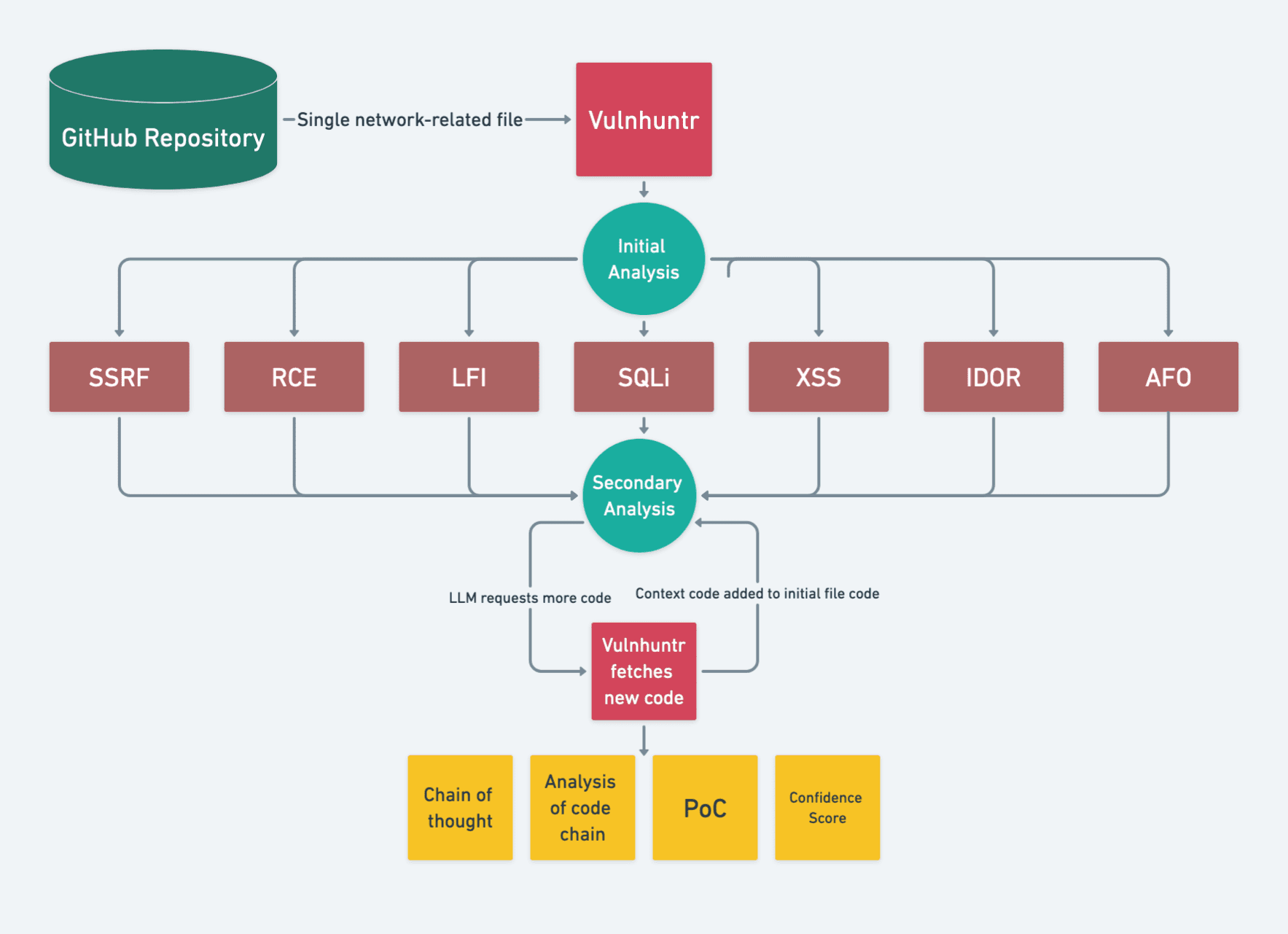
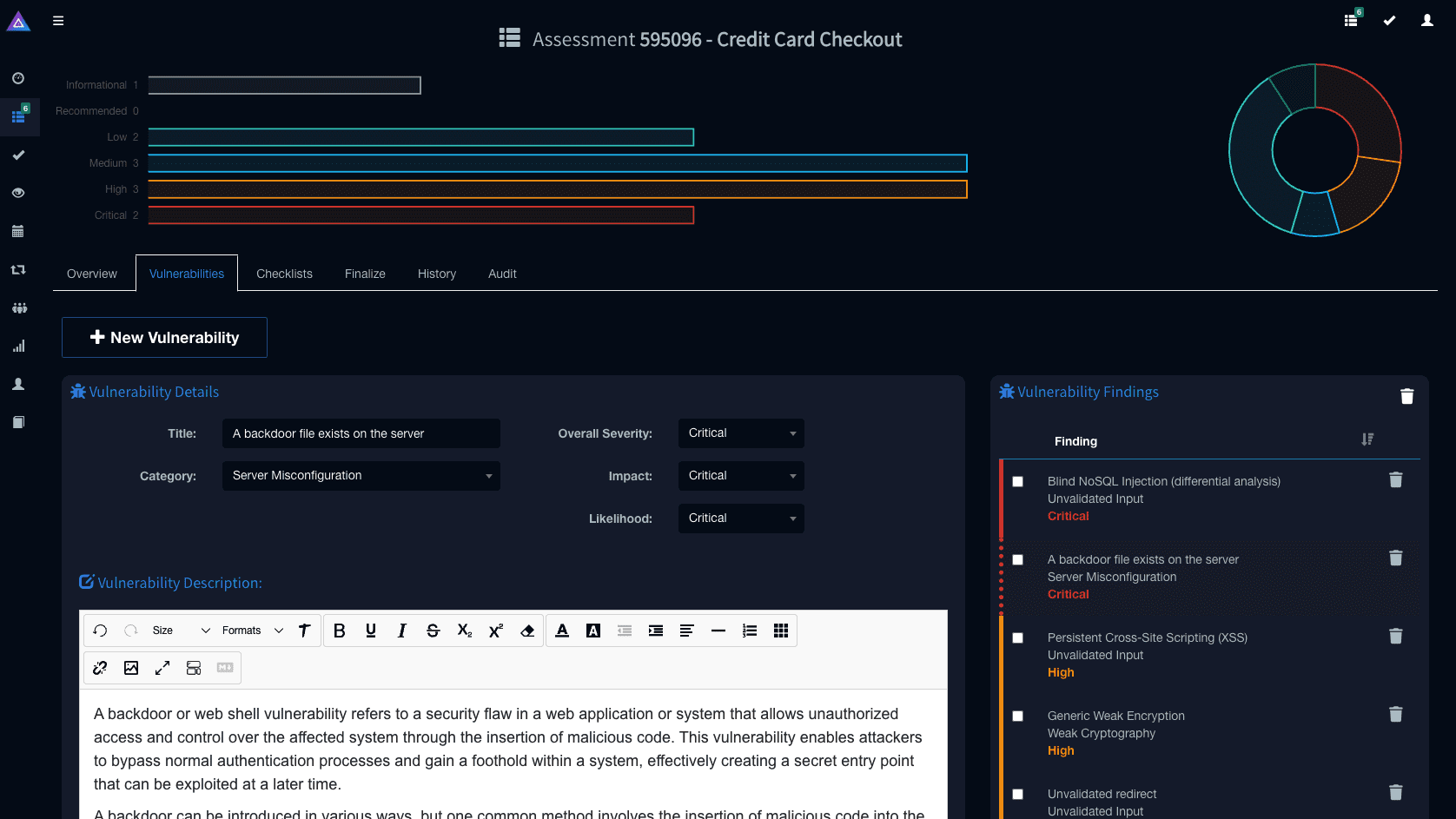
Kurosh Dabbagh Escalante, a Red Team Operator at BlackArrow, has introduced Eclipse, a proof-of-concept (PoC) tool designed to exploit Activation Context hijacking. By leveraging a technique known as Activation Context...