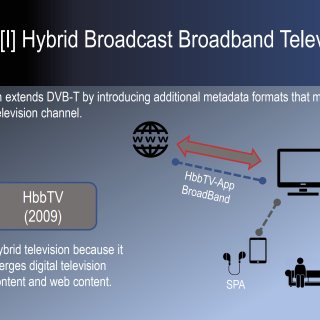
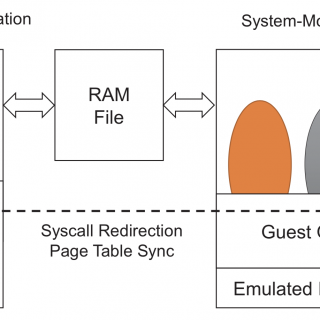
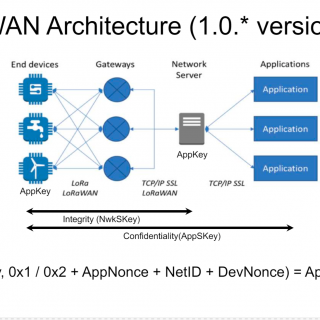
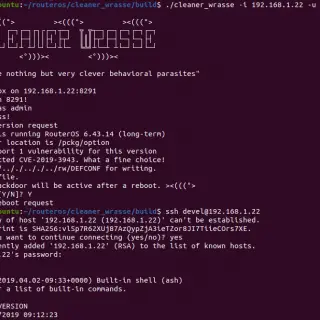
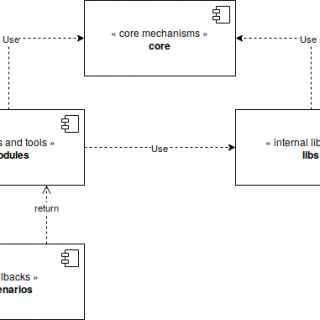
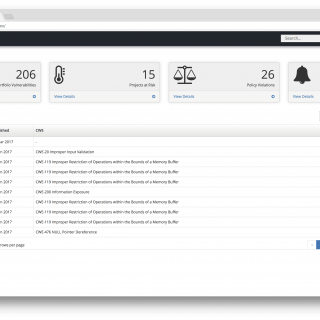
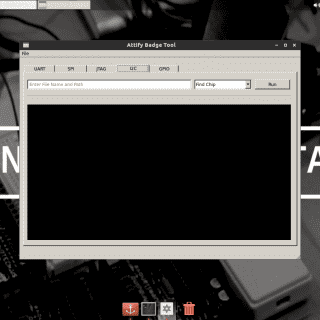
[Defcon Tool] SDR Against Smart TVs: URL and channel injection attacks
dtv-utils This project is a collection of utilities and scripts for digital television projects using bladeRF and GNU Radio dvbt-blade.py This Python script transmits a DVB-T digital television signal using the bladeRF and gr-dvbt...