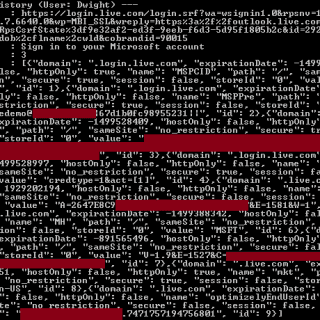
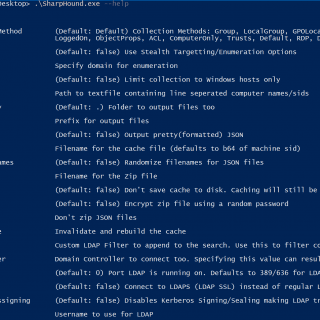
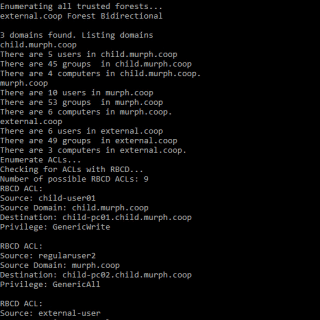
SharpChromium: retrieve Chromium data, such as cookies, history and saved logins
SharpChromium SharpChromium is a .NET 4.0+ CLR project to retrieve data from Google Chrome, Microsoft Edge, and Microsoft Edge Beta. Currently, it can extract: Cookies (in JSON format) History (with associated cookies for each...