Category: Post Exploitation
FakeLogonScreen FakeLogonScreen is a utility to fake the Windows logon screen in order to obtain the user’s password. The password entered is validated against the Active Directory or local machine to make sure it...
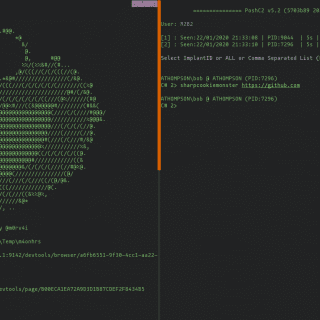
SharpCookieMonster This is a Sharp port of @defaultnamehere’s cookie-crimes module – full credit for their awesome work! This C# project will dump cookies for all sites, even those with httpOnly/secure/session flags. Usage Simply run the binary....
EDR-Checker Invoke-EDRChecker will check running processes, process metadata, Dlls loaded into your current process and each DLLs metadata, common install directories, installed services, the registry and running drivers for the presence of known defensive...
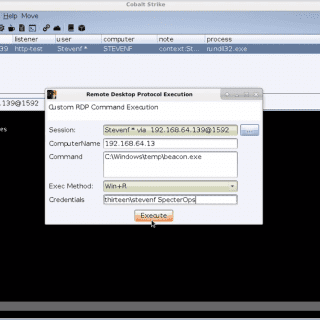
SharpRDP – Remote Desktop Protocol Console Application for Authenticated Command Execution How it works The terminal services library (mstscax.dll) has two different forms that can leveraged, the scriptable control that can be used by...
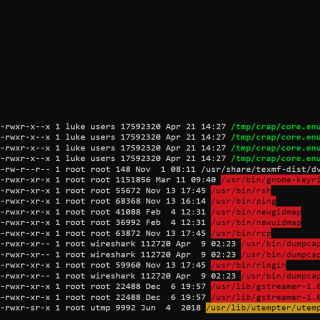
enumy Enumy is an ultra-fast portable executable that you drop on target Linux machine during a pentest or CTF in the post-exploitation phase. Running enumy will enumerate the box for common security vulnerabilities. Who Should Use...
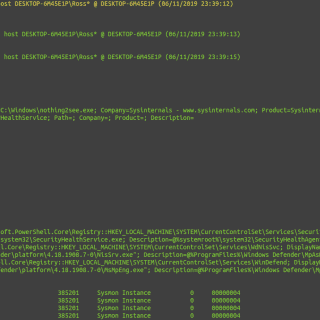
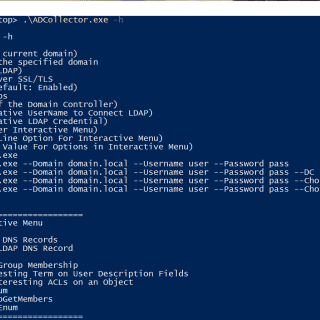
ADCollector ADCollector is a lightweight tool that enumerates the Active Directory environment to identify possible attack vectors. It will give you a basic understanding of the configuration/deployment of the environment as a starting point....
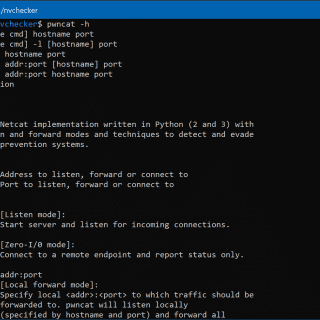
pwncat Netcat with Firewall and IPS evasion, bind and reverse shell, local and remote port-forward. Motivation Ever accidentally hit Ctrl+c on your reverse shell and it was gone for good? Ever waited forever for your client...
SharpDPAPI SharpDPAPI is a C# port of some DPAPI functionality from @gentilkiwi‘s Mimikatz project. The SharpChrome subproject is an adaptation of work from @gentilkiwi and @djhohnstein, specifically his SharpChrome project. However, this version of SharpChrome uses a different version of the C# SQL library that...
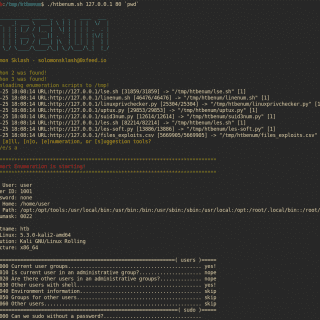
htbenum A Linux enumeration script for Hack The Box This script is designed for use in situations where you do not have internet access on a Linux host and would like to run enumeration...
Chromepass – Hacking Chrome Saved Passwords Chromepass is a python-based console application that generates a windows executable with the following features: Decrypt Chrome saved passwords Send a file with the login/password combinations remotely (email...
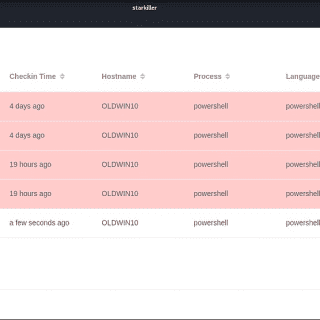
Starkiller Starkiller is a Frontend for Powershell Empire. It is an Electron application written in VueJS. Multi-user GUI application for interfacing with the Empire C2 server from any computer. Starkiller represents a huge step forward...
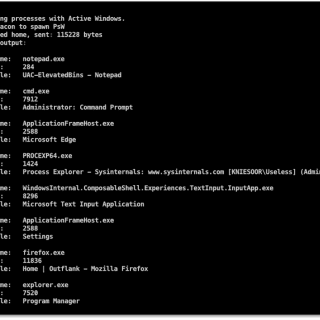
Ps-Tools, an advanced process monitoring toolkit for offensive operations. Having a good technical understanding of the systems we land on during an engagement is a key condition for deciding what is going to be...
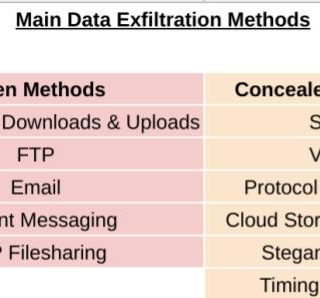
lollipopz Data exfiltration utility used for testing the detection capabilities of security products. Obviously for legal purposes only. Download git clone https://github.com/tasooshi/lollipopz.git Use /etc/shadow -> HTTP GET requests Server # ./lollipopz-cli.py -m lollipopz.methods.http.param_cipher.GETServer -lp...
Pulsar Pulsar is a tool for data exfiltration and covert communication that enables you to create a secure data transfer, a bizarre chat or a network tunnel through different protocols, for example, you can...
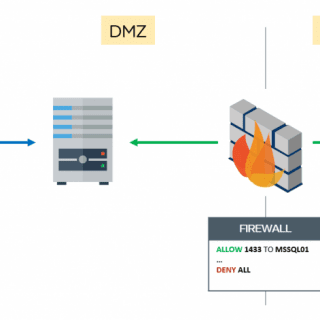
mssqlproxy mssqlproxy is a toolkit aimed to perform a lateral movement in restricted environments through a compromised Microsoft SQL Server via socket reuse. The client requires impacket and sysadmin privileges on the SQL server. Please read this article carefully before...