Category: Post Exploitation
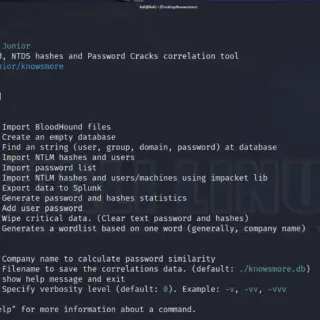
KnowsMore KnowsMore is a Swiss army knife tool for pentesting Microsoft Active Directory (NTLM Hashes, BloodHound, NTDS, and DCSync). Main features Import NTLM Hashes from .ntds output txt file (generated by CrackMapExec or secretsdump.py)...
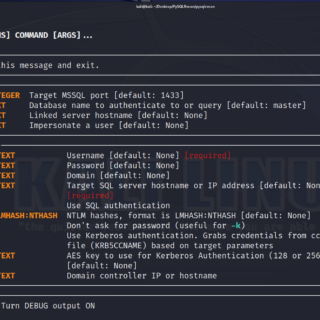
MSSqlPwner MSSqlPwner is an advanced and versatile pentesting tool designed to seamlessly interact and pwn MSSQL servers. That tool is based on impacket, which allows attackers to authenticate to databases using clear-text passwords NTLM...
PySQLRecon PySQLRecon is a Python port of the awesome SQLRecon project by @sanjivkawa. See the commands section for a list of capabilities. Commands All of the main modules from SQLRecon have equivalent commands. Commands noted with [PRIV] require elevated...
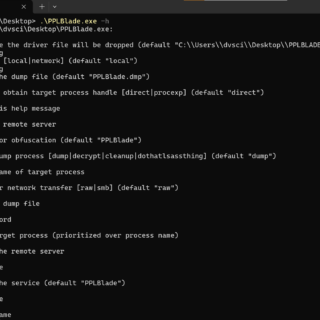
PPLBlade Protected Process Dumper Tool that supports obfuscating memory dump and transferring it on remote workstations without dropping it onto the disk. Key functionalities: Bypassing PPL protection Obfuscating memory dump files to evade Defender...
nysm: A stealth post-exploitation container With the rise in popularity of offensive tools based on eBPF, going from credential stealers to rootkits hiding their own PID, a question came to our mind: Would it...
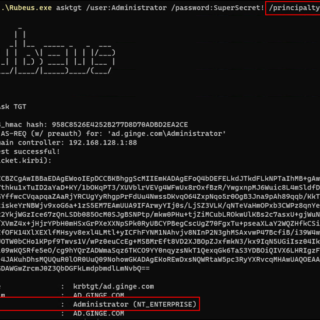
gssapi-abuse gssapi-abuse was released as part of my DEF CON 31 talk. A full write-up on the abuse vector can be found here: A Broken Marriage: Abusing Mixed Vendor Kerberos Stacks The tool has...
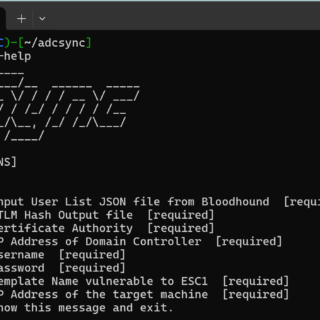
ADCSync ADCSync uses the ESC1 exploit to dump NTLM hashes from user accounts in an Active Directory environment. The tool will first grab every user and domain in the Bloodhound dump file passed in....
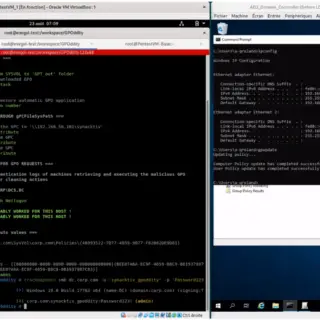
GPOddity The GPOddity project aims at automating GPO attack vectors through NTLM relaying (and more). For more details regarding the attack and a demonstration of how to use the tool, see the associated article...
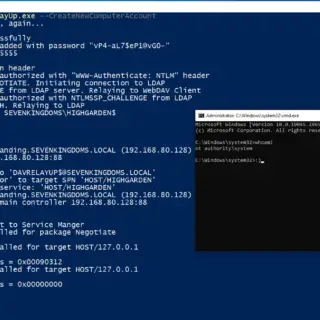
DavRelayUp A quick and dirty port of KrbRelayUp with modifications to allow for NTLM relay from webdav to LDAP in order to streamline the abuse of the following attack primitive: (Optional) New machine account creation (New-MachineAccount)...
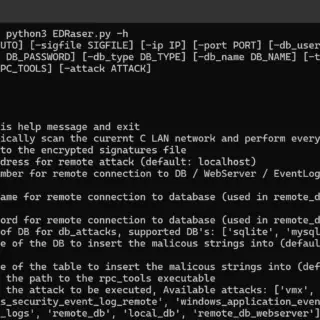
EDRaser EDRaser is a powerful tool for remotely deleting access logs, Windows event logs, databases, and other files on remote machines. It offers two modes of operation: automated and manual. Automated Mode In automated...
CVE-2023-36874 Windows Error Reporting LPE BOF This is a mature and operational CobaltStrike BOF implementation of Filip Dragovic’s (@filip_dragovic) CVE-2023-36874 Windows Error Reporting LPE exploit. He did the heavy lifting in terms of creating a...
WMIexec Set of Python scripts which perform different ways of command execution via WMI protocol. Blog Post https://whiteknightlabs.com/2023/06/26/navigating-stealthy-wmi-lateral-movement/ Download git clone https://github.com/WKL-Sec/WMIExec.git Use wmiexec_scheduledjob.py Is a Python script which authenticates to a remote WMI...
S4UTomato Escalate Service Account To LocalSystem via Kerberos. Traditional Potatoes Friends familiar with the “Potato” series of privilege escalation should know that it can elevate service account privileges to local system privileges. The early...
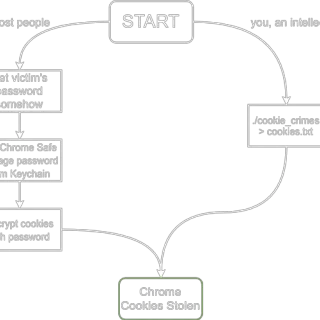
Chrome Cookie Stealer (and injector) Attaches to Chrome using its Remote DevTools protocol and steals/injects/clears/deletes cookies. Heavily inspired by WhiteChocolateMacademiaNut. Cookies are dumped as JSON objects using Chrome’s own format. The same format is used for...
KRBUACBypass UAC Bypass By Abusing Kerberos Tickets This POC is inspired by James Forshaw (@tiraniddo) shared at BlackHat USA 2022 titled “Taking Kerberos To The Next Level ” topic, he shared a Demo of abusing...