Category: Social Engineering
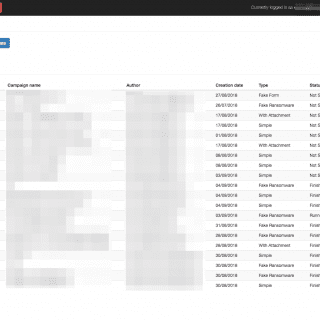
What is Swordfish? Swordphish is a platform allowing to create and manage fake phishing campaigns. The goal of Swordphish is to raise your users’ awareness regarding phishing in a secure way. We believe that...
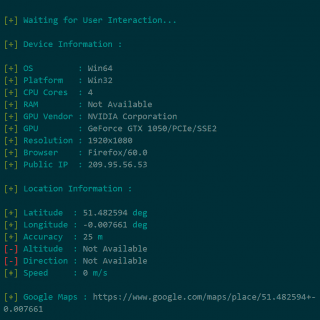
Seeker Introduction Seeker utilizes HTML5, Javascript, JQuery and PHP to grab Device Information and GeoLocation with High Accuracy. Seeker Hosts a fake website on Apache Server and uses Ngrok to generate an SSL link which asks for Location Permission and if the user allows...
REBEL-FRAMEWORK Advanced and easy to use penetration testing framework Module├ ├ net/iface ➤ Interface info. ├ net/map ➤ Hosts live Scan in LAN. ├ net/scan ➤ Scan [Ports, OS, Etc] IP. ├ net/vuln ➤...
King Phisher is a tool for testing and promoting user awareness by simulating real-world phishing attacks. It features an easy to use, yet very flexible architecture allowing full control over both emails and server...
Miteru Miteru is an experimental phishing kit detection tool. How it works It collects phishing suspicious URLs from the following feeds: urlscan.io certstream-suspicious feed OpenPhish feed via urlscan.io PhishTank feed via urlscan.io It checks...
The Social-Engineer Toolkit (SET) is specifically designed to perform advanced attacks against the human element. SET has quickly become a standard tool in a penetration testers arsenal. SET is written by David Kennedy (ReL1K)...
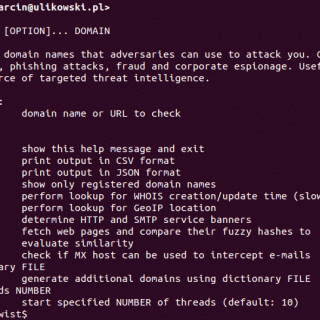
dnstwit See what sort of trouble users can get in trying to type your domain name. Find similar-looking domains that adversaries can use to attack you. Can detect typosquatters, phishing attacks, fraud, and corporate...
DNSMORPH is a domain name permutation engine, inspired by dnstwist. It is written in Go making for a compact and very fast tool. It robustly handles any domain or subdomain supplied and provides a number of configuration options...
Muraena is an almost-transparent reverse proxy aimed at automating phishing and post-phishing activities. The tool re-implements the 15-years old idea of using a custom reverse proxy to dynamically interact with the origin to be targeted,...
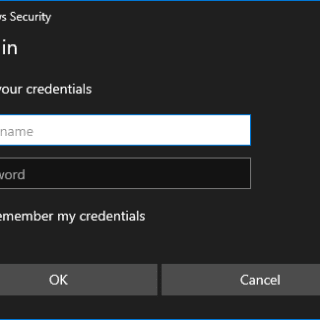
CredsLeaker Credsleaker allows an attacker to craft a highly convincing credentials prompt using Windows Security, validate it against the DC and in turn leak it via an HTTP request. However, That was highly noticeable....
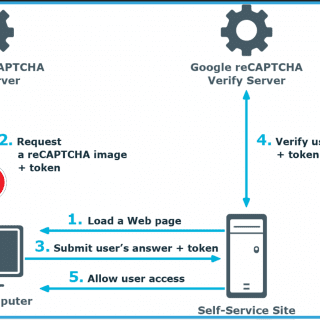
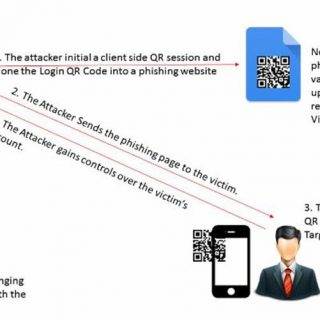
What is QRLJacking? QRLJacking or Quick Response Code Login Jacking is a simple social engineering attack vector capable of session hijacking affecting all applications that rely on the “Login with QR code” feature as...
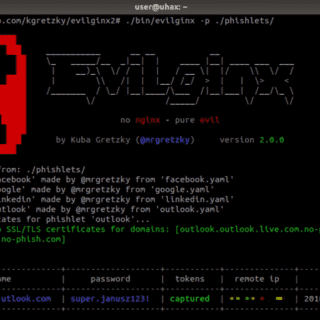
evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. This tool is a successor to Evilginx, released in 2017, which used...
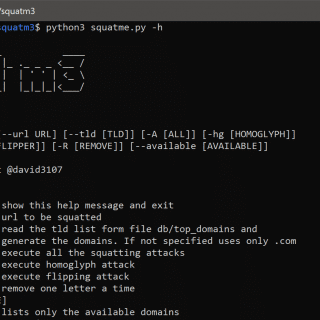
Squatm3 Squatm3 is a python tool designed to enumerate available domains generated modifying the original domain name through different techniques: Substitution attacks Flipping attack Homoglyph attack Squatm3 will help penetration testers to identify domains...
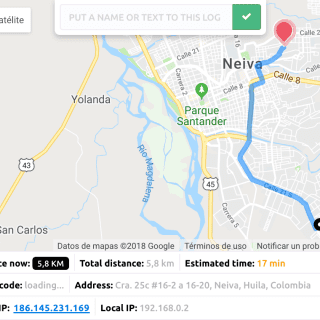
trape (open source) People tracker on the Internet: Learn to track the world, to avoid being traced. Trape is an OSINT analysis and research tool, which allows people to track and execute intelligent social engineering attacks in real...
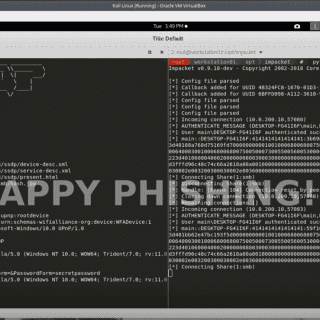
evil-ssdp This tool responds to SSDP multicast discovery requests, posing as a generic UPNP device. Your spoofed device will magically appear in Windows Explorer on machines in your local network. Users who are tempted...