Category: Reverse Engineering
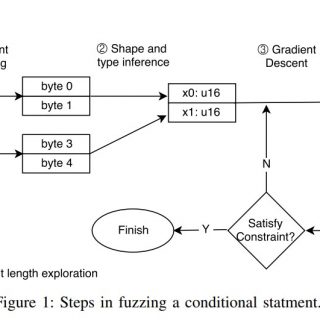
Angora Angora is a mutation-based coverage guided fuzzer. The main goal of Angora is to increase branch coverage by solving path constraints without symbolic execution. Angora consists of a fuzzer, instrumenting compilers and runtime...
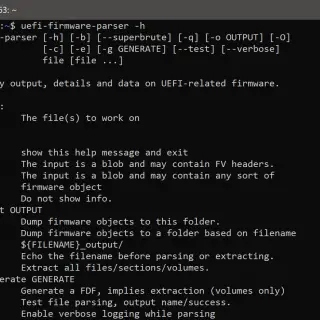
UEFI Firmware Parser The UEFI firmware parser is a simple module and set of scripts for parsing, extracting, and recreating UEFI firmware volumes. This includes parsing modules for BIOS, OptionROM, Intel ME and other...
The Hex-Rays Decompiler plugin for better code navigation in RE process. CodeXplorer automates code REconstruction of C++ applications or modern malware like Stuxnet, Flame, Equation, Animal Farm. The CodeXplorer plugin is one of the first...
r2kit Overview r2kit is a set of scripts to help with a workflow for malware code analysis using radare. sessionstarter.py – Run from inside an r2 session to auto rename imports, thunks, wrapper functions,...
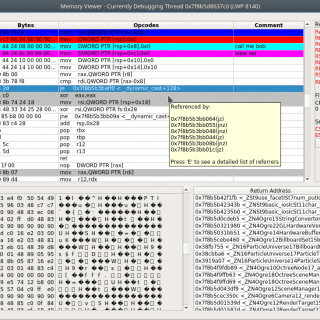
labeless Labeless is a plugin system for dynamic, seamless and real-time synchronization between IDA Database and debugs backend. It consists of two parts: IDA plugin and debugs backend’s plugin. Labeless significantly reduces the time that...
exploit_me Very vulnerable ARM/ARM64 application (CTF style exploitation tutorial for ARM/ARM64, but portable to other platforms). Why: Some of my friends asked me if I could do some examples of exploitable stuff I’ve seen...
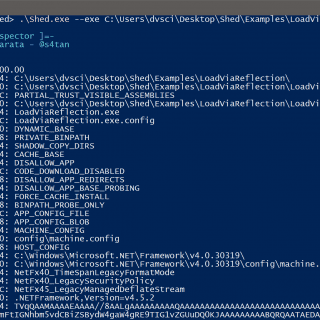
Shed is an application that allows inspecting the .NET runtime of a program in order to extract useful information. It can be used to inspect malicious applications in order to have a first general overview...
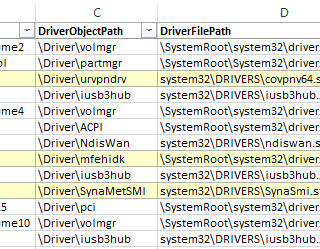
DIRT: Driver Initial Reconnaissance Tool get an initial assessment of drivers installed on a Windows system (e.g. master images developed by OEMs or enterprises). It’s supposed to help with target selection, finding low-hanging fruit,...
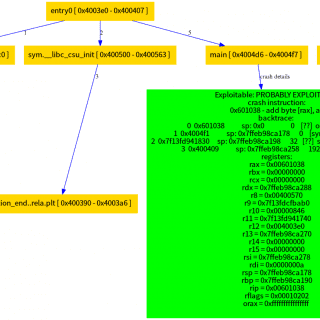
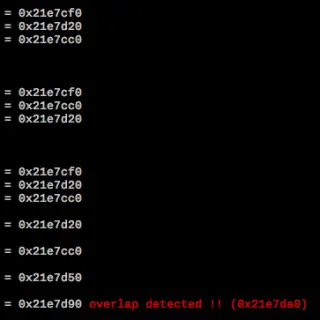
beebug beebug is a tool that can be used to verify if a program crash could be exploitable. This tool was presented at r2con 2018 in Barcelona. Some implemented functionality are: Stack overflow on libc Crash on...
PINCE PINCE is a front-end/reverse engineering tool for the GNU Project Debugger (GDB), focused on games. However, it can be used for any reverse-engineering related stuff. PINCE is an abbreviation for “PINCE is not...
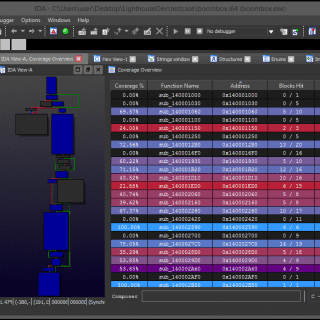
Lighthouse – Code Coverage Explorer for IDA Pro Overview Lighthouse is a code coverage plugin for IDA Pro. The plugin leverages IDA as a platform to map, explore, and visualize externally collected code coverage data...
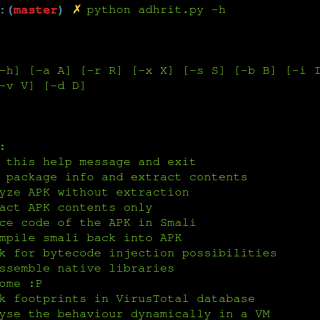
Adhrit is an open source Android APK reversing and analysis tool that can help security researchers and CTF enthusiasts alike. The tool is an effort to cut down on the amount of time spent...
HITCON-Training For Linux binary Exploitation Outline Basic Knowledge Introduction Reverse Engineering Static Analysis Dynamic Analysis Exploitation Useful Tool IDA PRO GDB Pwntool lab 1 – sysmagic Section Compile, linking, assembler Execution how program get...
IDArling is a collaborative reverse engineering plugin for IDA Pro and Hex-Rays. It allows synchronizing in real-time the changes made to a database by multiple users, by connecting together different instances of IDA Pro. The main features...
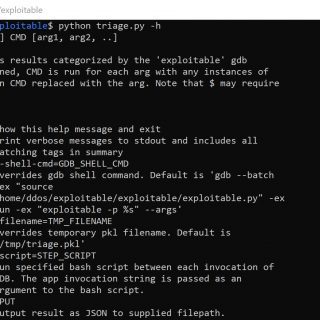
GDB ‘exploitable’ plugin The ‘exploitable’ plugin (exploitable/exploitable.py) ‘exploitable’ is a GDB extension that classifies Linux application bugs by severity. The extension inspects the state of a Linux application that has crashed and outputs a...