ccat v1.01 releases: Cisco Config Analysis Tool
CCAT
Cisco Config Analysis Tool
This tool is designed to analyze the configuration files of the Cisco devices. The list of checks is based on the Cisco Guide to Harden Cisco IOS Devices.
List of the checks
Firmware version
Older versions of IOS may contain vulnerabilities.
Unused services
Some of these services can be used by attackers.
Tool check if service is disabled and if is not is warning generated.
List of potentially dangerous services:
- Http service
- Smart install
- Finger service
- Bootstrap protocol
- Maintenance Operation Protocol (MOP) (L3 switches)
Privilege separation
Cisco devices have 16 privilege levels from 0 to 15. The «1» level is user’s privilege and «15» level is highest administrator’s rights.
The number of users with privilege level 15 must be kept to a minimum.
- User2 have 2 level’s privilege:
user2 privilege 2 secret cisco - Assign a match between commands and the privilege level:
privilege exec level 2 configure
privilege exec level 2 configure t
privilege configure level 2 interface
privilege interface level 2 shutdown
privilege interface level 2 ip address - Setting the password for entering in the privileged mode of the 2 level:
enable secret level 2 ciscocisco
More…
Changelog v1.01
The release with the current set of checks and network map of VLANs in the EXE extension.
Install
git clone https://github.com/cisco-config-analysis-tool/ccat.git
pip3 install -r requirements.txt
Use
The simplest way to use: python3 ccat.py configuration_file
Windows: ccat.exe configuration_file
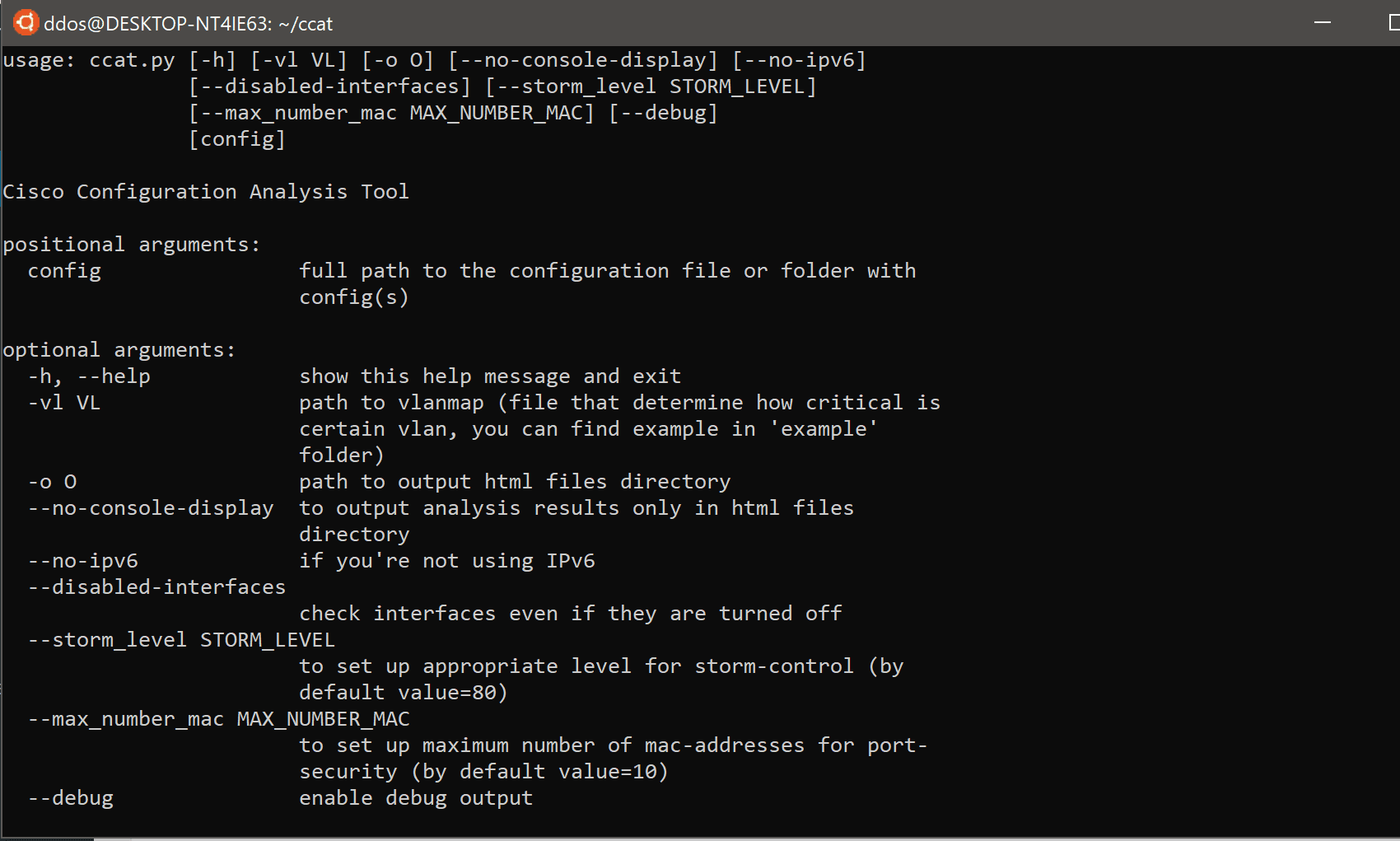
Extended options:
python3 ccat.py config_directory -vl vlmap.txt -o result_html_files_directory –storm_level 40.0 –max_number_mac 100 –disabled-interfaces –no-console-display






