credential digger v4.13 releases: identifies hardcoded credentials
Credential Digger
Credential Digger is a GitHub scanning tool that identifies hardcoded credentials (Passwords, API Keys, Secret Keys, Tokens, personal information, etc), filtering the false positive data through machine learning models. It supports Python 3.6 and works only with LINUX systems.
Architecture
Credential Digger finds credentials hardcoded in a repository. The tool is composed of:
- Postgres database
- Python client
- User interface
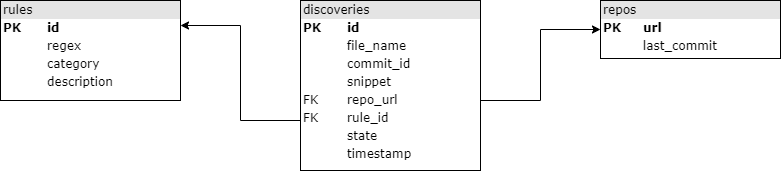
Database
The database is structured in the following way (arrows point to foreign keys).
Project structure
The project includes 3 components: a db (sql folder), a client (credentialdigger folder), and a user interface (ui folder).
sql
create_table.sql defines the db schema.
Note that, given the file_name and commit_hash of discovery, both the commit and the file can be accessible at addresses:
REPO_URL/commit/COMMIT_HASH
REPO_URL/blob/COMMIT_HASH/file_name
credentialdigger
This client can be used to easily interact with the db. It offers a scanner for git repositories, based on Hyperscan (others can be implemented). Please note that the database must be up and running.
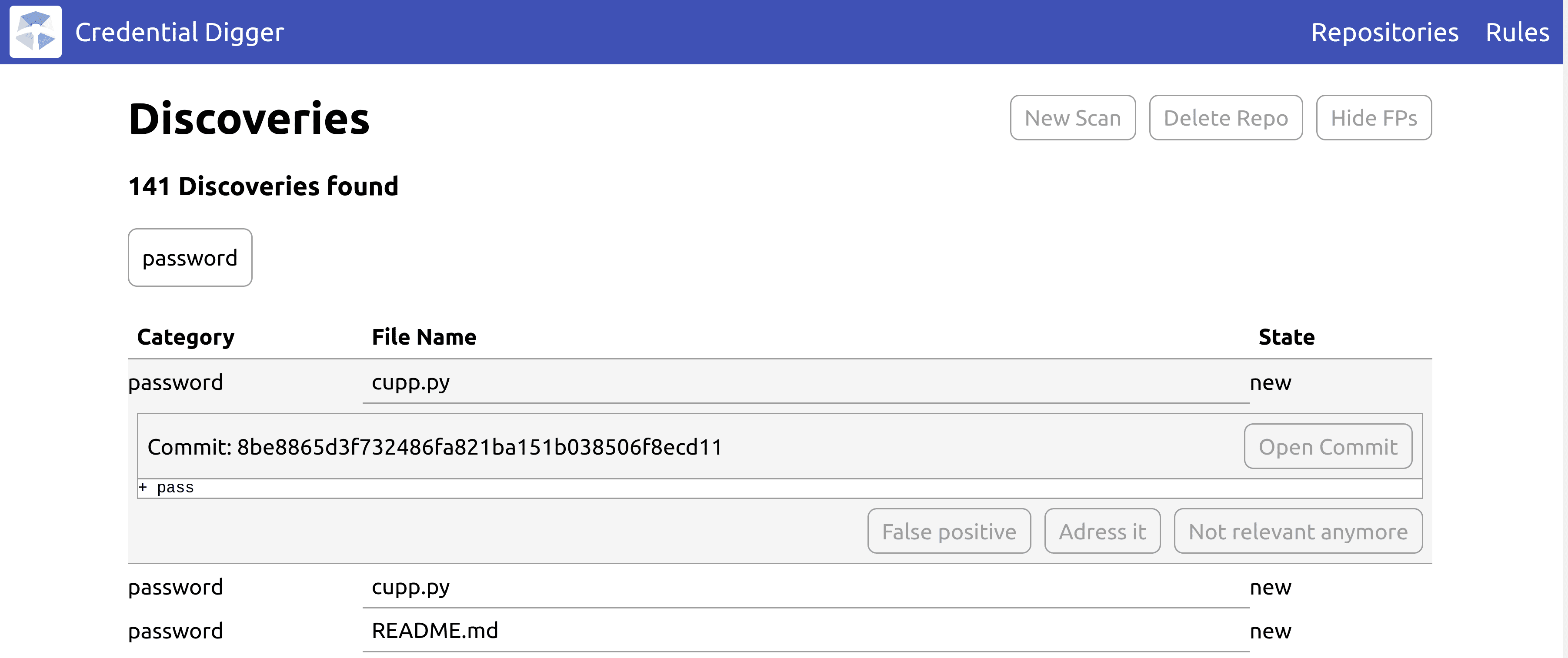
ui
The user interface can be used to easily perform scans and flag the discoveries.
Changelog v4.13
Restructure the project and repackage the tool in a more modern way.
Introduce src layout and a pyproject.toml while deprecating setup.py.
Version tracking is now delegated to a dynamic file and old package data (old folders for BoW models deprecated in v4.4) have been deleted.
A new badge has been introduced to show what python versions are currently supported by Credential Digger (this point is often source of confusion as we have to rely on external libraries not necessarily supporting the latest available python versions). This badge will be updated only after the release of pypi package (it relies on metadata published there).
Minor version has been increased to better distinguish from the old package structure, even if it could also not be strongly needed in such a case.
Install & Use
Copyright (C) 2020 SAP