CVE-2024-55884 (CVSS 9.0): Critical Vulnerability Found in Mullvad VPN

X41 D-Sec GmbH, a leading cybersecurity firm, has completed a white-box penetration test of the Mullvad VPN application, revealing several vulnerabilities, including one rated as “critical” and two rated as “high” severity.
The audit uncovered three high-severity vulnerabilities, including issues with signal handlers and sideloading risks during installation processes. One notable vulnerability, MLLVD-CR-24-01 (CVE-2024-55884, CVSS 9.0), involves insufficient alternate stack sizes for signal handlers, potentially leading to memory corruption. As the report explains, “While exploitation for code execution is expected to be non-trivial, the fact that the alt stack collides with the heap of concurrently running processes makes exploitation a possibility if an attacker is able to trigger a signal in the right context.”
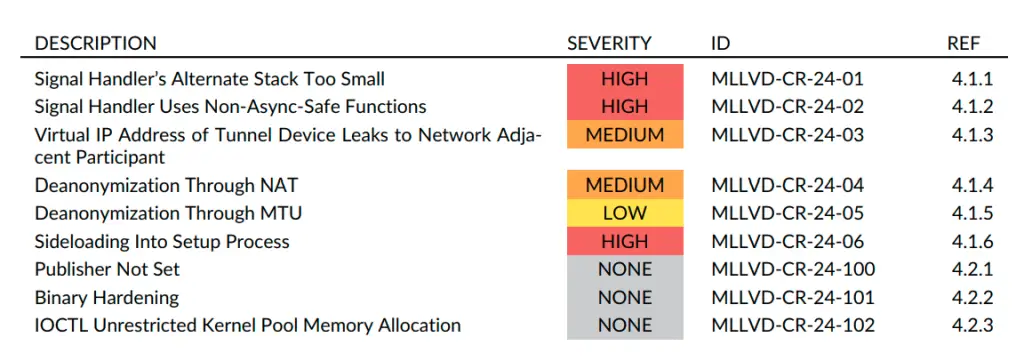
Security-Relevant Findings | Source: X41
Despite these findings, X41 D-Sec GmbH acknowledged the high-security level of the Mullvad VPN application, stating that “Overall, the Mullvad VPN Application appear to have a high-security level and are well positioned to protect from the threat model proposed in this report.” The report also highlighted Mullvad’s commitment to security, noting their “use of safe coding and design patterns in combination with regular audits and penetration tests” which has “led to a very hardened environment.”
Mullvad VPN AB has responded swiftly to the findings, addressing the vulnerabilities and undergoing a fix audit to ensure effectiveness. X41 D-Sec GmbH recommends continued regular security reviews and mitigation of the identified issues, stating that doing so “will strengthen the security of the system and is recommended for defense in depth.”





