Dr0p1t-Framework: advanced stealthy dropper that bypass most AVs and have a lot of tricks
Dr0p1t-Framework
Have you ever heard about trojan droppers ? In short dropper is type of trojans that downloads other malwares and Dr0p1t gives you the chance to create a stealthy dropper that bypass most AVs and have a lot of tricks ( Trust me 😀 ) 😉
Features
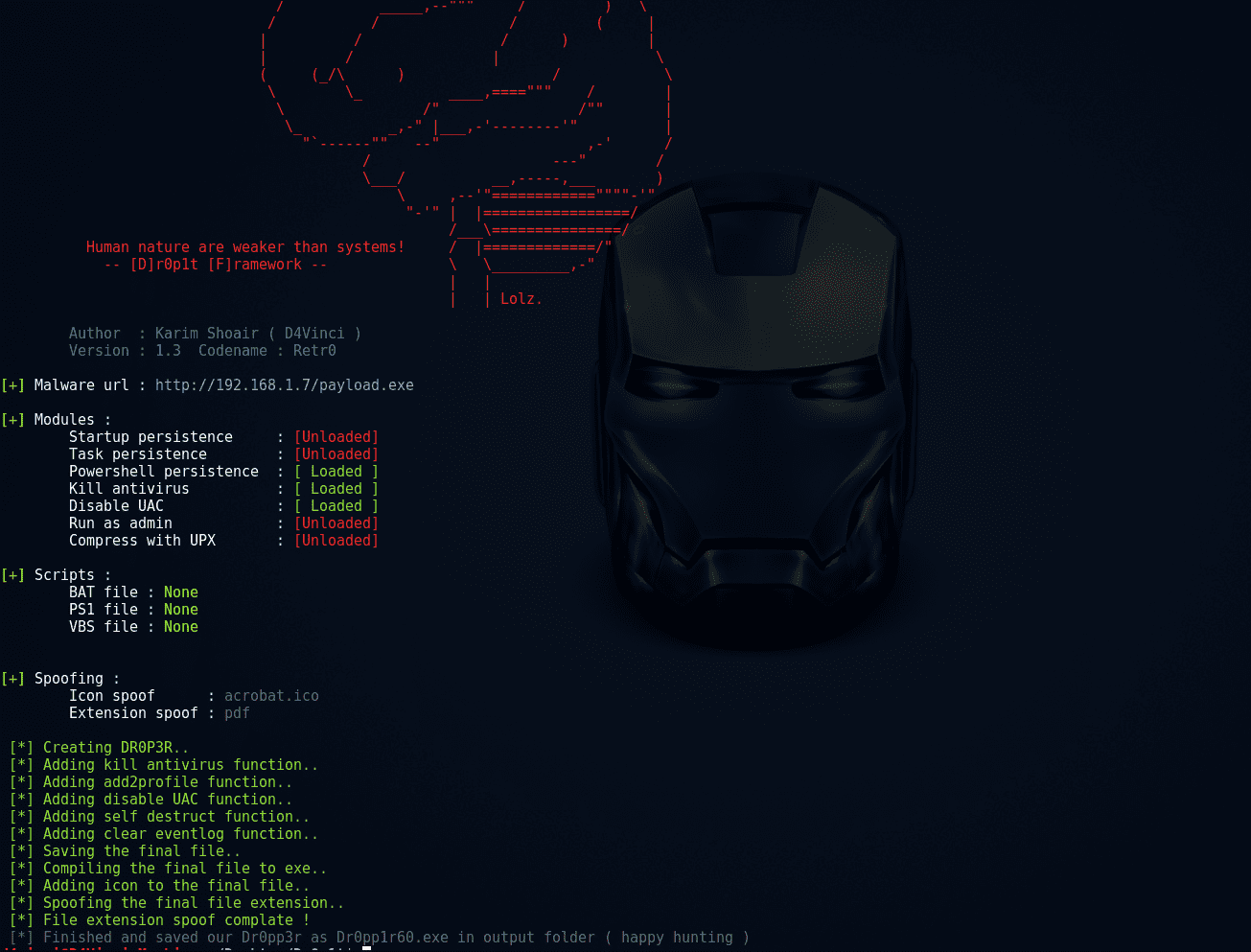
+ Generated executable properties:
- The executable size is smaller compared to other droppers generated the same way.
- Download executable on target system and execute it silently..
- Self destruct function so that the dropper will kill and delete itself after finishing it work
- Escape disk forensics by making all the files dropper create and dropper also cleans its content before deletion
- Clear event log after finishing.
+ Framework properties:
- Works with Windows, Linux and now have OSX support ( Thanks to @sm4sh3r )
- Dr0p1t-Server feature (beta) so now you can work from browser See how to work with Dr0p1t-Server
- Dr0p1t-Server have a scam option (beta) See how to work with Dr0p1t-Server
+ Modules:
- Find and kill antivirus before running the malware.
- The ability to disable UAC.
- The ability to run your malware as admin.
- Full spoof by spoofing the file icon and extension to any thing you want.
- ZIP files support so now you can compress your executable to zip file before uploading.
- Running a custom ( batch|powershell|vbs ) file you have chosen before running the executable
- In running powershell scripts it can bypass execution policy
- Using UPX to compress the dropper after creating it
+Persistence modules:
- Adding executable after downloading it to startup.
- Adding executable after downloading it to task scheduler ( UAC not matters ).
- Adding your file to powershell user profile so your file will be downloaded and ran every time powershell.exe run if it doesn’t exist.
Change log
Version 1.3
+## A huge update to fix and make improvements like :
+- [Feature] Adding spoof extension feature so now you can change the file extension and icon to make it full spoof 🙂
+- [Improve] Added OSX support ( Thanks to @sm4sh3r )
+- [Improve] Now there will be debug file when happen error in compiling with Pyinstaller.
+- [BUG fix] Full rewriting the framework to improve the executions methods and fix all the errors
+- [BUG fix] Bypassed the error in the Pyinstaller **”FATAL ERROR”** with replacing subprocess Pipes with files 🙂
+- [Stealth] Escaping disk forensics by making all the files dropper create and dropper also cleans its content before deletion.
+- [Feature] Adds ZIP files support so now you can compress your executable to zip file before uploading
+- [Feature] Added Dr0p1t-Server feature (beta) so now you can work from browser [See how to work with Dr0p1t-Server](https://github.com/D4Vinci/Dr0p1t-Framework#Work-with-Dr0p1t-Server)
+- [Feature] Added Scamming feature (beta) to Dr0p1t-Server [See how to edit Dr0p1t-Server scam ](https://github.com/D4Vinci/Dr0p1t-Framework#Work-with-Dr0p1t-Server)
+- [Stealth] Clear event log after finishing
+- [Improve] Added install.sh to make installing on Linux more easy
+- [Improve] Persistence modules are now improved and recoded to work much better.
+- [Feature] Added new a new-hard-to-detect persistence module ( Adding your file to powershell user profile so your file will be downloaded and ran every time powershell.exe run if it doesn’t exist).
+- [Feature] Added a new module to bypass UAC and run your malware as admin