Evasive Malware Campaign Leverages CleverSoar Installer & Nidhogg Rootkit
Rapid7 Labs has uncovered a sophisticated malware campaign employing the newly identified CleverSoar installer, a highly evasive threat targeting Chinese and Vietnamese-speaking users. With advanced evasion techniques and layered malicious components like the Winos4.0 framework and Nidhogg rootkit, the CleverSoar campaign signifies a targeted espionage effort with serious implications.
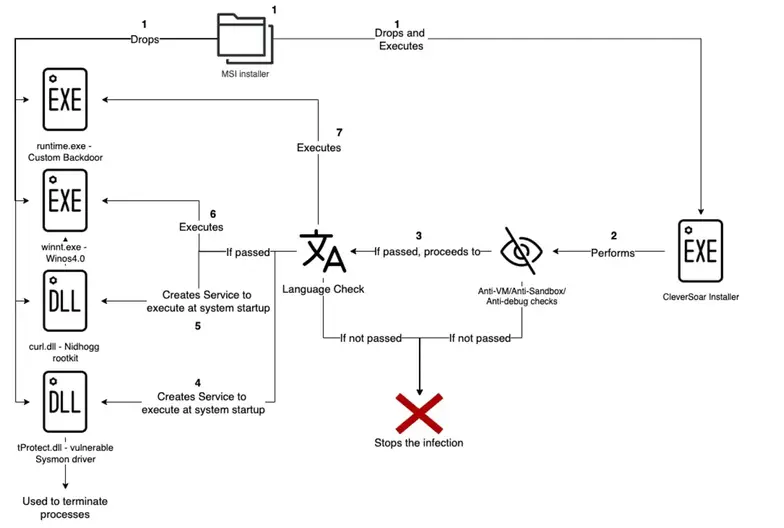
The CleverSoar installer is designed with a clear focus: it checks system language settings to infect only devices with Chinese or Vietnamese configurations. Rapid7 Labs highlights, “The CleverSoar installer… verifies the language identifier for the user interface language… If the language ID does not match any of these identifiers, the malware terminates its execution”.
This selective targeting and its deployment of multiple malware components suggest the campaign is aimed at espionage. CleverSoar’s capabilities include keystroke logging, data exfiltration, security bypasses, and covert system control.
The campaign begins with a .msi installer package that appears as fake gaming-related software. Once executed, the installer employs advanced anti-detection methods:
- Anti-Virtual Machine (VM) Techniques: CleverSoar retrieves raw SMBIOS firmware tables to detect VM environments, similar to techniques used by Raspberry Robin malware
- Anti-Debugging Measures: The installer uses functions like
IsDebuggerPresentand timing checks withGetTickCount64to evade analysis - Windows Defender Bypass: It cleverly manipulates Defender’s emulator checks to proceed undetected
- Persistence Mechanisms: CleverSoar installs scheduled tasks, modifies the Windows registry, and disables the Windows firewall to maintain control
CleverSoar’s arsenal includes:
- Winos4.0 Framework: A command-and-control implant for remote operations.
- Nidhogg Rootkit: Used to disable security software and achieve stealthy persistence.
- Custom Backdoor: Facilitates communication with a command-and-control server using proprietary protocols.
Rapid7’s investigation revealed that the malware uses a file-drop mechanism, creating services to execute malicious drivers and binaries. For example, the Nidhogg rootkit is initiated by creating a kernel-based service to run at system startup, ensuring its persistence.
While attribution remains uncertain, Rapid7 Labs noted similarities with the ValleyRAT campaign, suggesting a connection to advanced threat actors. “The techniques employed in the CleverSoar installer suggest that the threat actor possesses advanced skills and a comprehensive understanding of Windows protocols and security products”.
Related Posts:
- Kimsuky APT: New TTPs Revealed in Rapid7 Cybersecurity Report
- Cybercriminals Evolve Social Engineering Tactics, Exploit CVE-2022-26923 in Sophisticated Campaign
- CVE-2024-38094 Exploited: Attackers Gain Domain Access via Microsoft SharePoint Server
- Mozilla releases emergency update to fix two exploited zero-day vulnerabilities in Firefox
- Sophisticated Social Engineering Campaign Linked to Black Basta Ransomware