evilginx2 v3.2 releases: MITM attack framework that allow to bypass 2-factor authentication
evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection.
This tool is a successor to Evilginx, released in 2017, which used a custom version of the nginx HTTP server to provide man-in-the-middle functionality to act as a proxy between a browser and phished website. The present version is fully written in GO as a standalone application, which implements its own HTTP and DNS server, making it extremely easy to set up and use.
Disclaimer
I am very much aware that Evilginx can be used for nefarious purposes. This work is merely a demonstration of what adept attackers can do. It is the defender’s responsibility to take such attacks into consideration and find ways to protect their users against this type of phishing attack. Evilginx should be used only in legitimate penetration testing assignments with written permission from to-be-phished parties.
Changelog v3.2
- Feature: URL redirects on successful token capture now work dynamically on every phishing page. Pages do not need to reload or redirect first for the redirects to happen.
- Feature: Lures can now be paused for a fixed time duration with
lures pause <id>. Useful when you want to briefly redirect your lure URL when you know sandboxes will try to scan them. - Feature: Added phishlet ability to intercept HTTP requests and return custom responses via a new
interceptsection. - Feature: Added a new optional
redirect_urlvalue for phishlet config, which can hold a default redirect URL, to redirect to, once tokens are successfully captured.redirect_urlset for the specific lure will override this value. - Feature: You can now override globally set unauthorized redirect URL per phishlet with
phishlet unauth_url <phishlet> <url>. - Fixed: Disabled caching for HTML and Javascript content to make on-the-fly proxied content replacements and injections more reliable.
- Fixed: Improved JS injection by adding
<script src"...">references into HTML pages, instead of dumping the whole script there. - Fixed: Blocked requests will now redirect using javascript, instead of HTTP location header.
- Fixed: Changed
redirect_urltounauth_urlin global config to avoid confusion. - Fixed: Fixed HTTP status code response for Javascript redirects.
- Fixed: Javascript redirects now happen on
text/htmlpages with valid HTML content. - Fixed: Removed
ua_filtercolumn from the lures list view. It is still viewable in lure detailed view.
Installation
Usage
IMPORTANT! Make sure that there is no service listening on ports TCP 443, TCP 80 and UDP 53. You may need to shutdown apache or nginx and any service used for resolving DNS that may be running. evilginx2 will tell you on launch if it fails to open a listening socket on any of these ports.
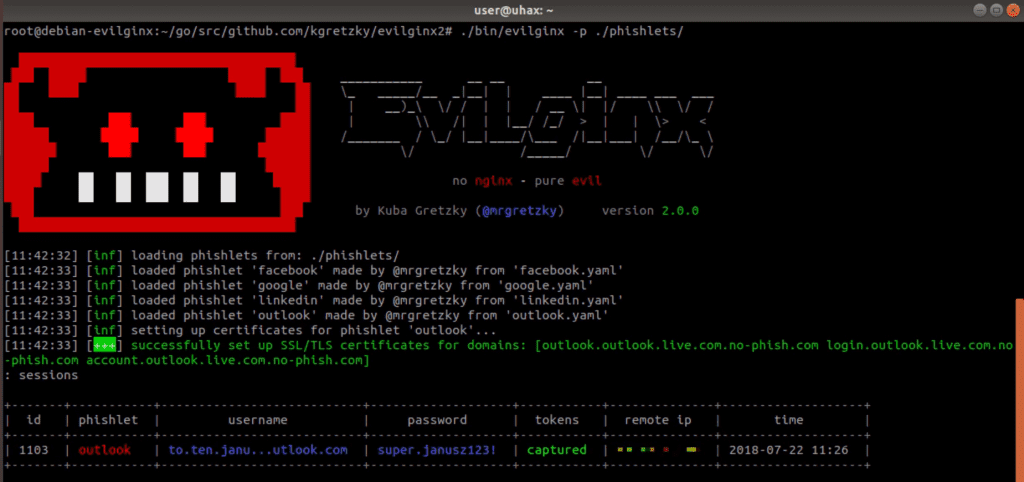
By default, evilginx2 will look for phishlets in ./phishlets/ directory and later in /usr/share/evilginx/phishlets/. If you want to specify a custom path to load phishlets from, use the -p <phishlets_dir_path> parameter when launching the tool.
Usage of ./evilginx: -debug Enable debug output -p string Phishlets directory path
You should see evilginx2 logo with a prompt to enter commands. Type help or help <command> if you want to see available commands or more detailed information on them.
Copyright (C) 2023 Kuba Gretzky (@mrgretzky)
Source: https://github.com/kgretzky/