File Upload Vulnerability Scenarios
File Upload Vulnerability Scenarios (Challenges)
This repository is a dockerized PHP application containing some file upload vulnerability challenges (scenarios).
OWASP References:
- Classification: Web Application Security Testing > 10-Business Logic Testing
- WSTG: WSTG-BUSL-09
Bypass Techniques
The ideas behind the challenges are:
- Bypassing client-side file extension validations.
- Bypassing client-side file size validations.
- Injecting PHP code into a gif file
- Run any extensions with the PHP engine (using .htaccess file)
- Black-list extension validation bypass
- White-list extension validation bypass
- Double extension bypass
- Server-side file size validation bypass
- Server-side file extension validation bypass
- Content-type validation bypass file upload
- Finding renamed file names and locations after the upload process
- Removing force download (using “Content-Disposition” header) to run the php file by use of htaccess
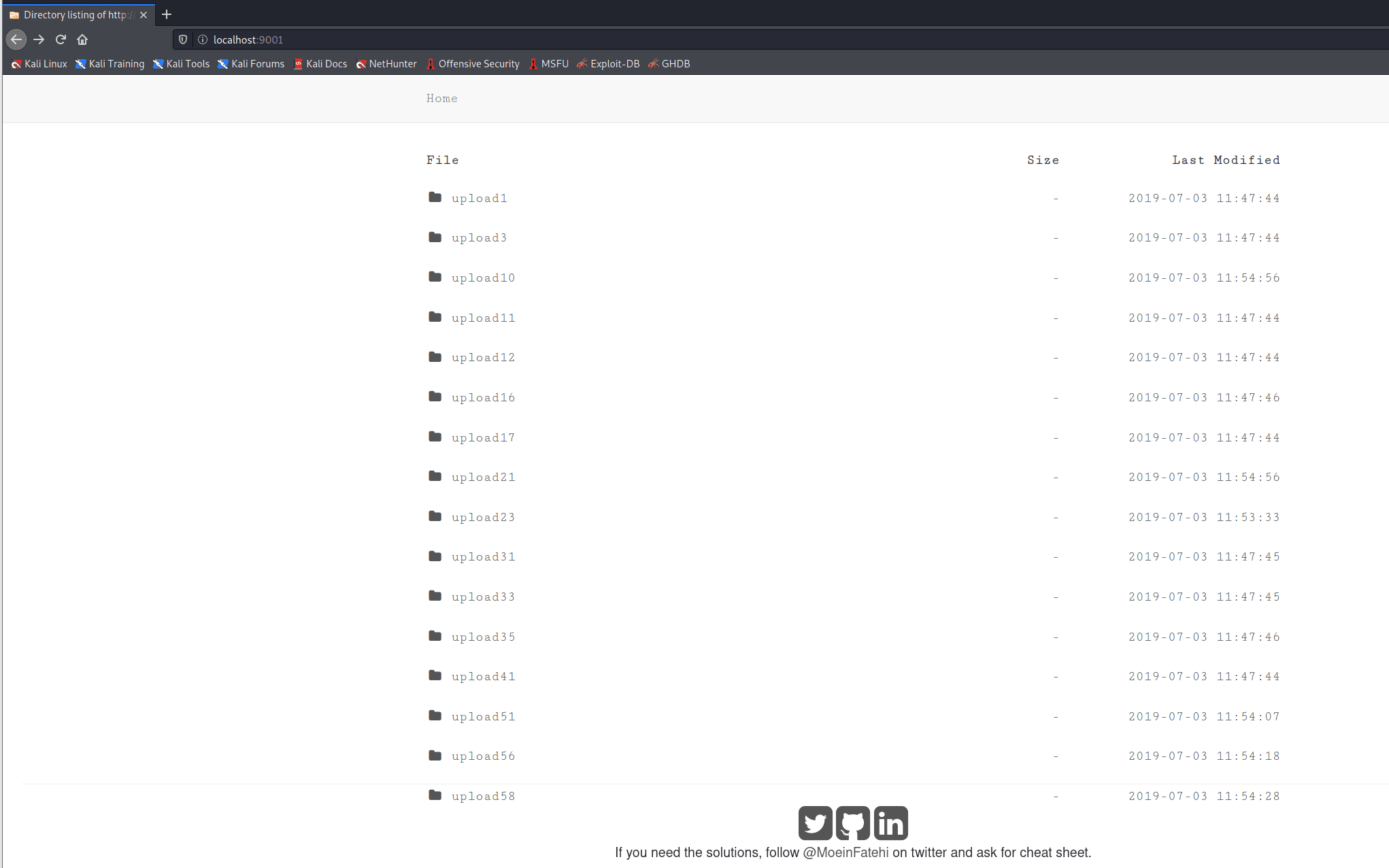
Install
Using docker hub (Quickest):
- To access the challenges, you need docker installed.
- Run this command to pull and run the image from docker hub:
sudo docker run -d -p 9001:80 moeinfatehi/file_upload_vulnerabilities - Access the challenges with this URL: http://localhost:9001
Using docker-compose:
- To access the challenges, you need docker and docker-compose installed.
- Clone the repository
git clone https://github.com/moeinfatehi/file_upload_vulnerability_scenarios.git - Open the main directory of the project (where the docker-compose.yml file exists) and run: docker-compose up
- Access the challenges with this URL: http://localhost:9001
Attention
- Do not host these challenges without docker on your main operating system and web server, because any of these challenges are critically dangerous ones, if any hacker can access these challenges on your host web server, your main OS can be attacked in different ways.
- Using docker-compose which is described above will not have these types of impacts.
Source: https://github.com/moeinfatehi/






