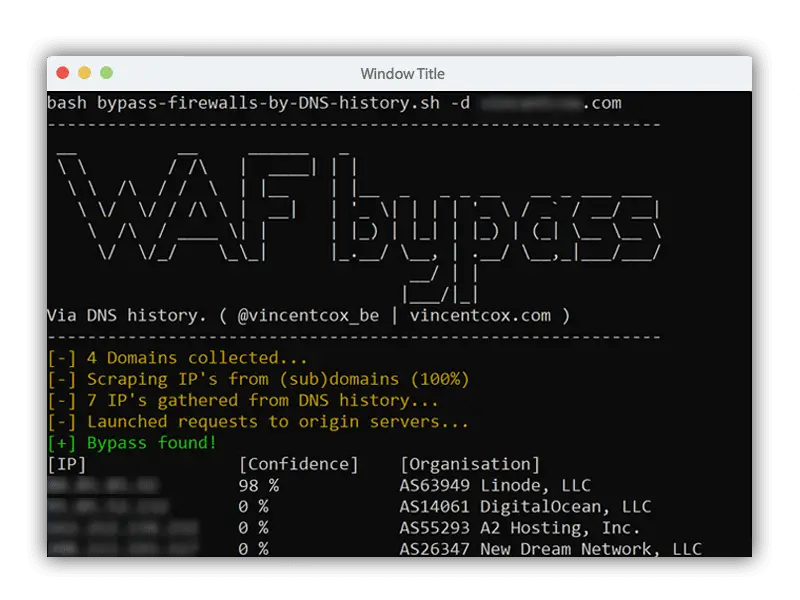
Firewall bypass script based on DNS history records
Bypass firewalls by abusing DNS history
This script will try to find:
- the direct IP address of a server behind a firewall like Cloudflare, Incapsula, SUCURI …
- an old server which still running the same (inactive and unmaintained) website, not receiving active traffic because the A DNS record is not pointing towards it. Because it’s an outdated and unmaintained website version of the currently active one, it is likely vulnerable to various exploits. It might be easier to find SQL injections and access the database of the old website and abuse this information to use on the current and active website.
This script (ab)uses DNS history records. This script will search for old DNS A records and check if the server replies for that domain. It also outputs a confidence level, based on the similarity in HTML response of the possible origin server and the firewall.
The script also fetches the IP’s of subdomains because my own experience learned me that subdomain IP’s sometimes point to the origin of the main domain.
Download
git clone https://github.com/vincentcox/bypass-firewalls-by-DNS-history.git
Usage
Make sure you made the script and the files in the sources folder executable:
sudo chmod +x dns-history-find-server.sh && sudo chmod +x sources/*
Use the script like this:
./dns-history-find-server.sh example.com
How to protect against this script?
- If you use a firewall, make sure to accept only traffic coming through the firewall. Deny all traffic coming directly from the internet. For example, Cloudflare has a list of IP’s which you can whitelist with iptables or UFW. Deny all other traffic.
- Make sure that no old servers are still accepting connections and not accessible in the first place
Copyright (c) 2017 Vincent Cox
Source: https://github.com/vincentcox/