Garud v4.0 releases: scans sub-domains, sub-domain takeover
Garud
An automation tool that scans sub-domains, sub-domain takeover, and then filters out xss, ssti, ssrf, and more injection point parameters.
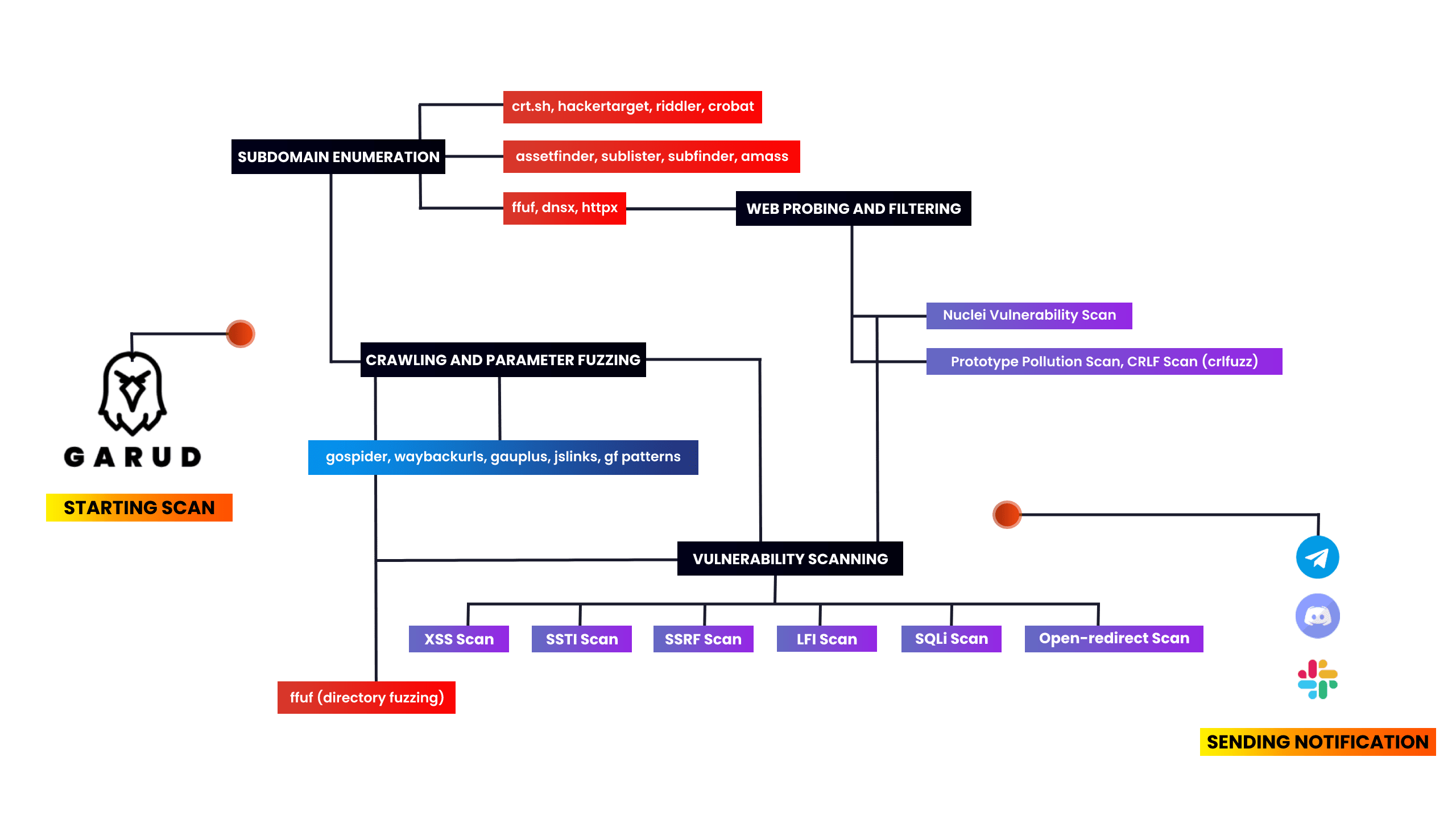
I made this tool to automate my recon and save my time. It really gives me a headache to always type such a command and then wait to complete one command and I type other commands. So I collected some of the tools which are widely used in the bugbounty field. In this script I used Assetfinder, subfinder, amass, httpx, sublister, gauplus, and gf patterns, and then it uses dirsearch, dalfox, nuclei, and kxss to find some low-hanging fruits.
The script first enumerates all the subdomains of the given target domain using assetfinder, sublister, subfinder, and amass then filters all live domains from the whole subdomain list then extract titles of the subdomains using httpx then it scans for subdomain takeover using nuclei. Then it uses gauplus to extract parameters of the given subdomains then it uses gf patterns to filters xss, ssti, ssrf, sqli params from that given subdomains, and then it scans for low hanging fruits as well. Then it’ll save all the output in a text file like target-xss.txt. Then it will send the notifications about the scan using notify.
Changelog v4.0
- Fixed minor-issues, updated install.sh file and added search from dorks in garud
Installation
Requirements: Go Language and Python 3.
System requirements: Recommended to run on vps with 1VCPU and 2GB ram.
Tools used – You must need to install these tools to use this script
subfinder • sublist3r • gf patterns • dnsx • assetfinder • httpx • kxss • qsreplace • nuclei • dalfox • anew • notify • aquatone • urldedupe • amass • gauplus • crlfuzz • ffuf • subjs • JSA • waybackurls
#Make sure you’re root before installing the tool
garud:~ sudo su
garud:~ apt install git
garud:~ git clone https://github.com/R0X4R/Garud.git && cd Garud/ && chmod +x garud install.sh && mv garud /usr/bin/ && ./install.sh
Copyright (c) 2020 Eshan Singh






