Hackers are exploiting CVE-2023-0558 and CVE-2023-0557 in WordPress plugin

The Wordfence Threat Intelligence team warned on Friday that WordPress sites are actively targeted with exploits targeting two zero-day vulnerabilities in the ContentStudio plugin.
ContentStudio is a powerful content marketing and social media management platform for publishers, brands, agencies, and, startups who want to share the best content consistently and increase their reach. And you can easily schedule posts and track the performance of your content on Facebook, Twitter, Linkedin, Pinterest, Instagram, Tumblr, and WordPress. The plugin has more than 33,034 downloads, its developer says.

“The ContentStudio plugin for WordPress is vulnerable to authorization bypass due to an unsecure token check that is susceptible to type juggling in versions up to, and including, 1.2.5. This makes it possible for unauthenticated attackers to execute functions intended for use by users with proper API keys,” WordPress security company Wordfence said in a report published.
This high authorization bypass security vulnerability, tracked as CVE-2023-0558, is rated 8.2 on the CVSS scale.
Another flaw tracked as CVE-2023-0557 (CVSS score of 7.5) is described as a sensitive information exposure that “could allow unauthenticated attackers to obtain a nonce needed for the creation of posts.”
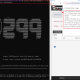
“Wordfence blocked 77 attacks targeting this vulnerability in the past 24 hours,” Wordfence senior threat analyst said.
Both CVE-2023-0558 and CVE-2023-0557 security flaws impact versions 1.2.5 and below of ContentStudio and were fully resolved with version 1.2.6.
While Wordfence disclosed active exploitation of these security bugs in the wild, it didn’t release additional information regarding these attacks and details regarding the vulnerability.