LogRM: uses windows event logs to gather information about internal network
LogRM
LogRM is a post-exploitation powershell script which it uses windows event logs to gather information about the internal network in a penetration testing engagement. It is not only useful for blue teams but also for red teams because some of its functionalities can be used for lateral movement. You will be able to use LogRM not only on a localhost machine but also in a remote machine using WinRM protocol which is by default enabled in a new Windows versions.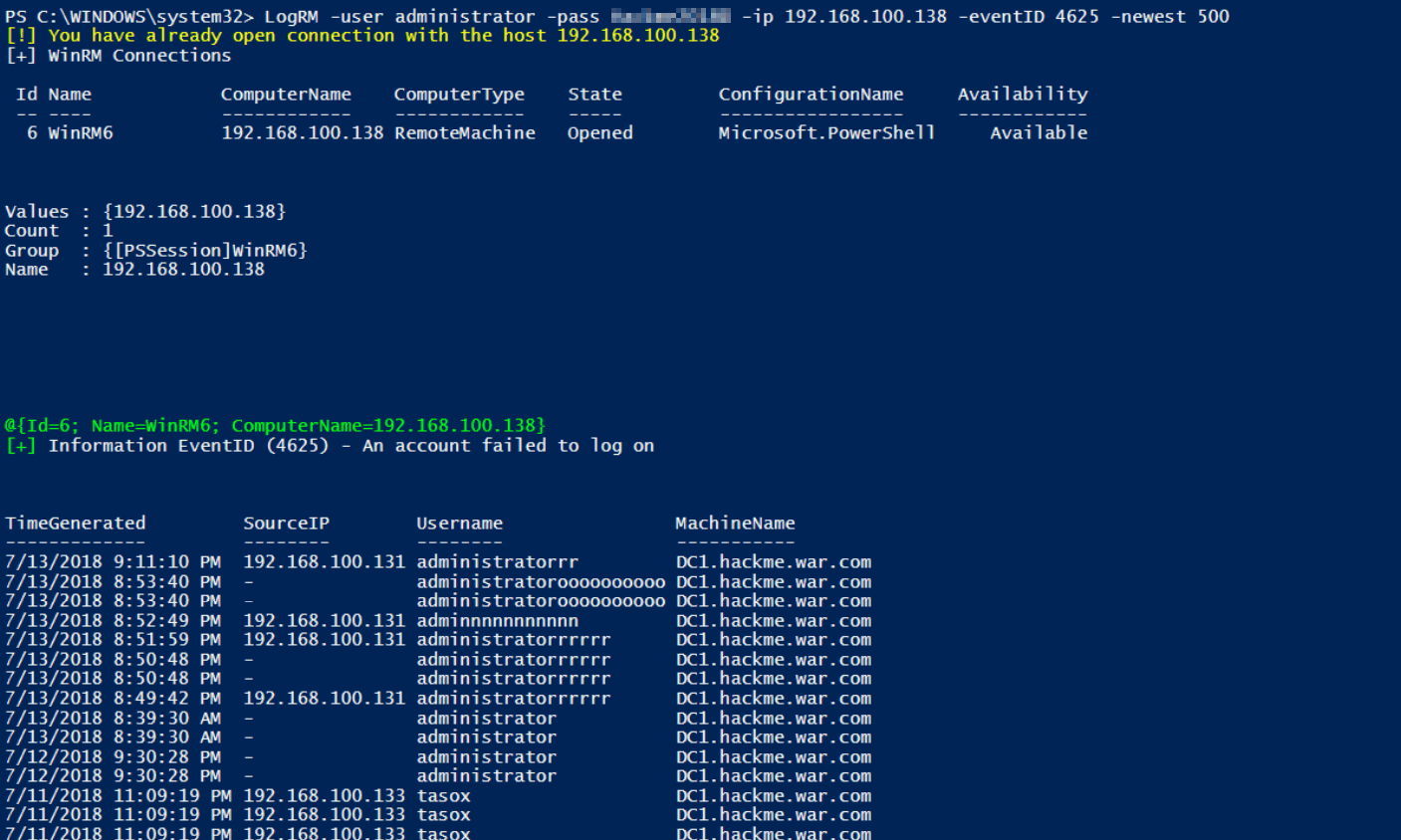
Download
git clone https://github.com/tasox/LogRM.git
Configuration
In some cases maybe you need to configure WinRM protocol to be functional
On the client side (attacker):
On the server side (victim):
Usage
Use can use the following event types:
- Information EventID (4624) – An account was successfully logged on
- Information EventID (4625) – An account failed to log on
- Information EventID (4728) – A member was added to a security-enabled global group
- Information EventID (4732) – A member was added to a security-enabled local group
- Information EventID (4733) – A member was removed from a security-enabled local group
- Information EventID (4738) – A user account was changed
- Information EventID (4647) – User initiated logoff
- Information EventID (4688) – A new process has been created
- Information EventID (4776) – The domain controller attempted to validate the credentials for an account
Author: tasox






