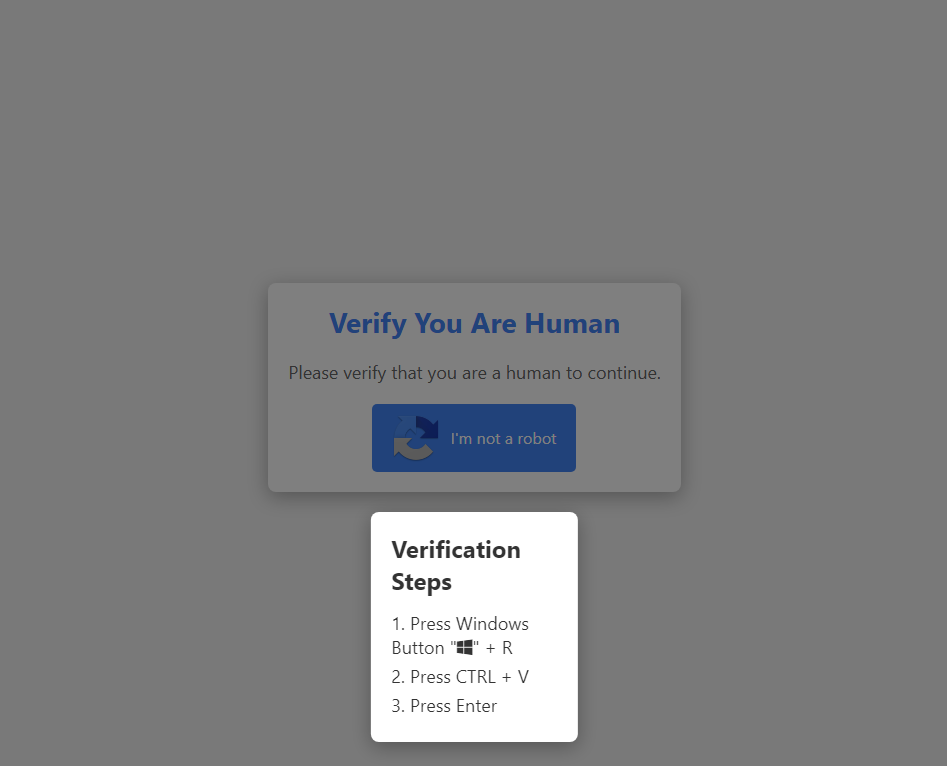
A fake CAPTCHA verification page | Source: ASEC
Cybersecurity researchers at AhnLab Security Intelligence Center (ASEC) have unveiled a sophisticated distribution tactic for the LummaC2 malware. This malicious campaign cleverly employs a fake CAPTCHA verification page to trick unsuspecting victims into executing harmful scripts.
The distribution begins with a seemingly innocent authentication screen. Visitors encounter a familiar “I’m not a robot” button. However, this button is anything but ordinary. Once clicked, it silently copies a malicious command to the user’s clipboard. As ASEC explains, “The threat actor explains a fake authentication step to trick users into executing the command copied to the clipboard using shortcut keys.” This command connects to a remote server and initiates a series of malware deployment steps.
The initial malicious payload, disguised as an HTA file named web44.mp4, leverages the mshta.exe process for execution. Despite its misleading file extension, this file is obfuscated, making detection challenging. Upon decryption, the payload launches an AES-encrypted PowerShell script that fetches and runs additional scripts to install LummaC2.
LummaC2 infostealer, the malware at the main of this campaign, targets sensitive data such as browser credentials and cryptocurrency wallets. The malware also features a module called ClipBanker, which alters clipboard data to replace copied cryptocurrency wallet addresses with those belonging to the attacker. This tactic ensures cryptocurrency transfers are redirected to the threat actor’s wallet without user awareness.
The campaign’s primary targets are users visiting crack program download pages or falling for phishing emails. ASEC emphasizes, “LummaC2 distributed through fake CAPTCHA pages is mainly spread via crack program download pages or phishing emails. Users should be especially cautious when dealing with emails or websites of unclear origin.”
Related Posts:
- Beware the Drive-By Download: LummaC2 Stealer and Malicious Chrome Extension Wreak Havoc
- LummaC2 Malware Uses Gaming Platform as C2 Server
- Threat Actor Deploys LummaC2 and Rhadamanthys Stealers in Attacks on Taiwanese Facebook Accounts
- ClearFake Campaign Employs Novel Social Engineering Tactic to Deliver LummaC2 Infostealer
- Beware! Fake Notion Installer Spreads Data-Stealing Malware