mihari v7.2 releases: framework for continuous OSINT based threat hunting
mihari
Mihari is a helper to run queries & manage results continuously. Mihari can be used for C2, landing pages, and phishing hunting.
How it works
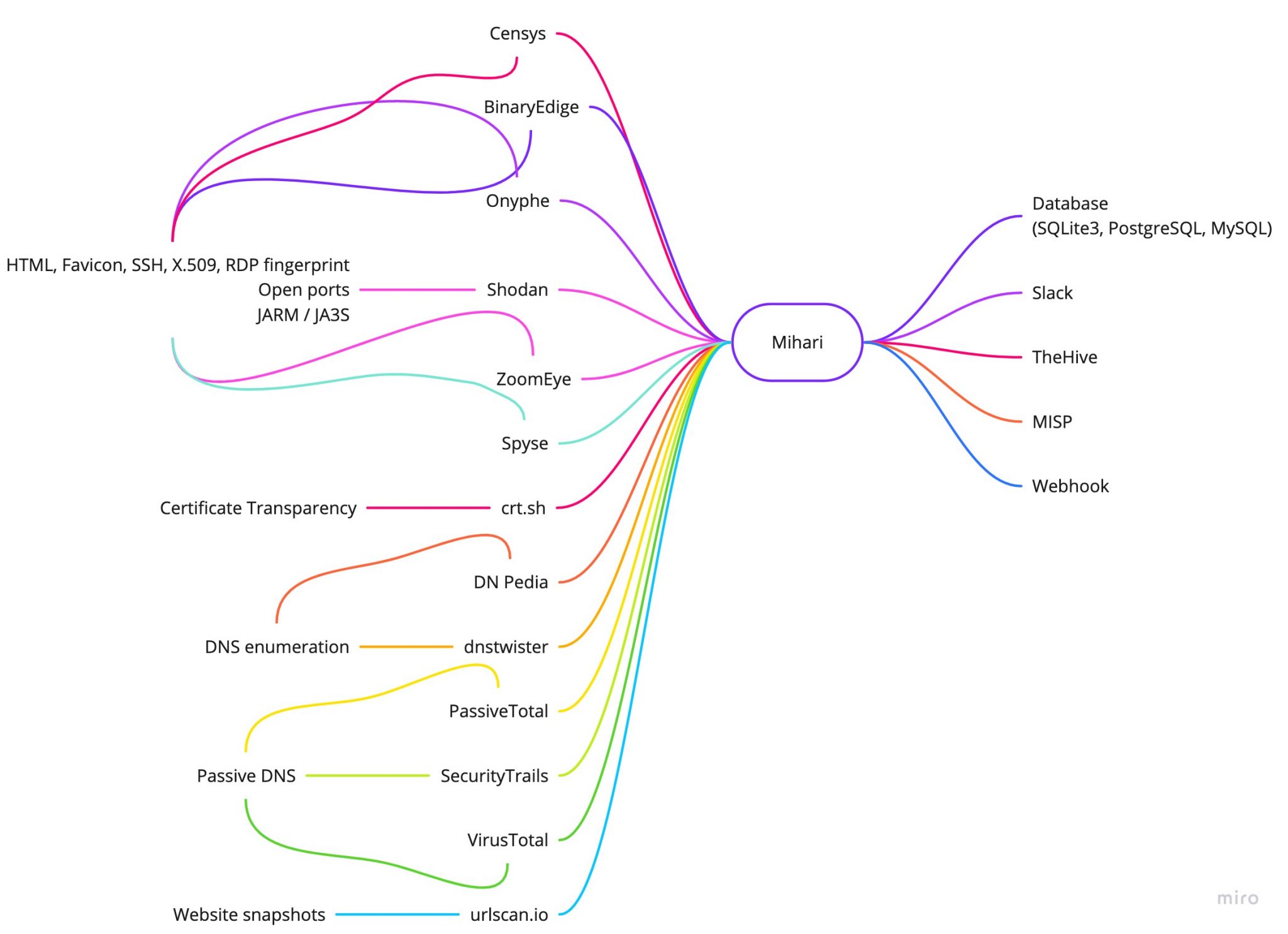
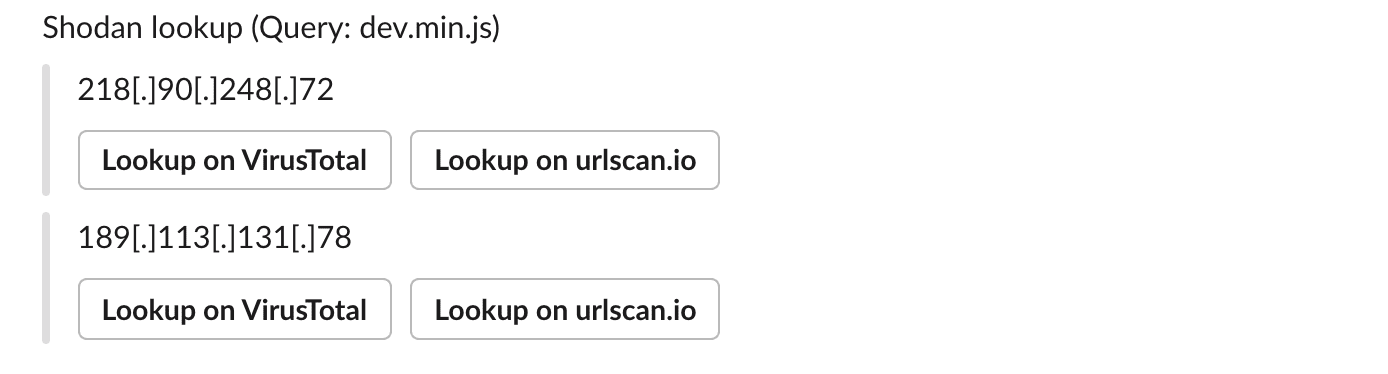
- Mihari makes a query against Shodan, Censys, VirusTotal, SecurityTrails, etc., and extracts artifacts (IP addresses, domains, URLs, or hashes).
- Mihari checks whether the database (SQLite3, PostgreSQL, or MySQL) contains the artifacts or not.
- If it doesn’t contain the artifacts:
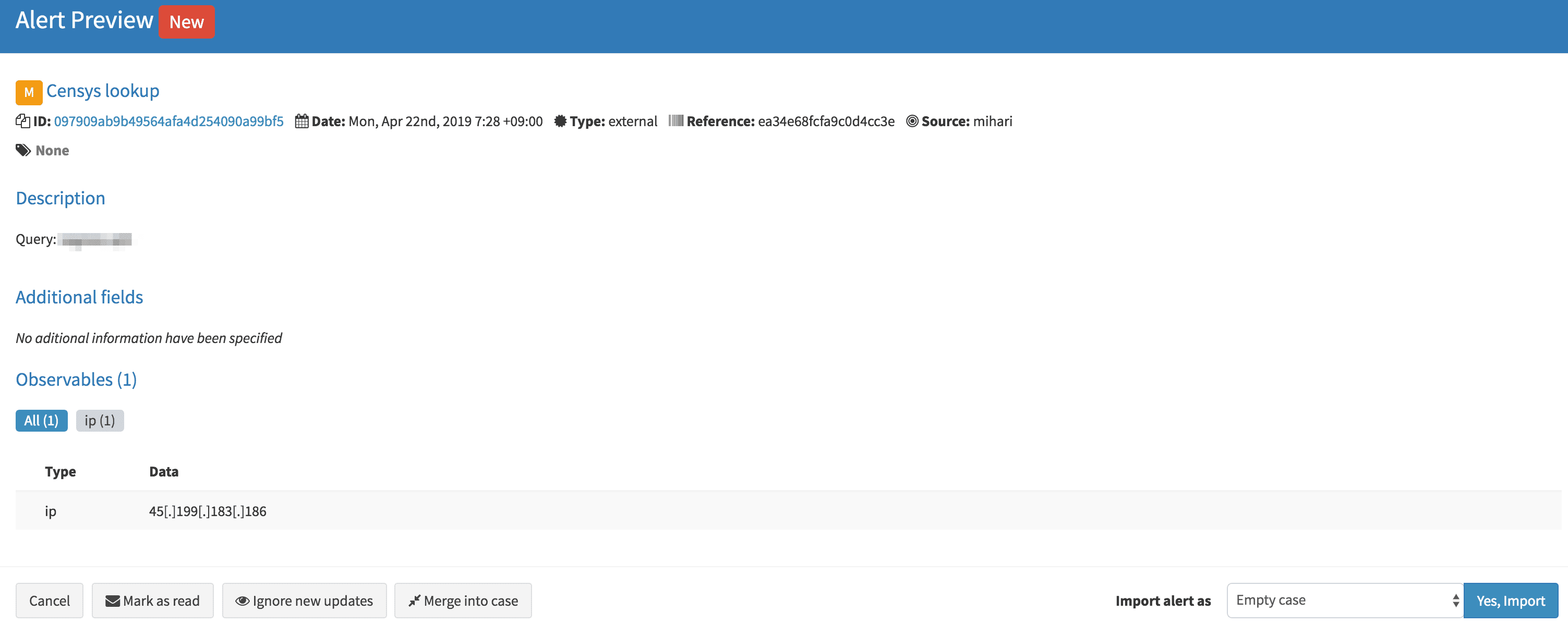
- Mihari saves artifacts in the database.
- Mihari creates an alert on TheHive.
- Mihari sends a notification to Slack.
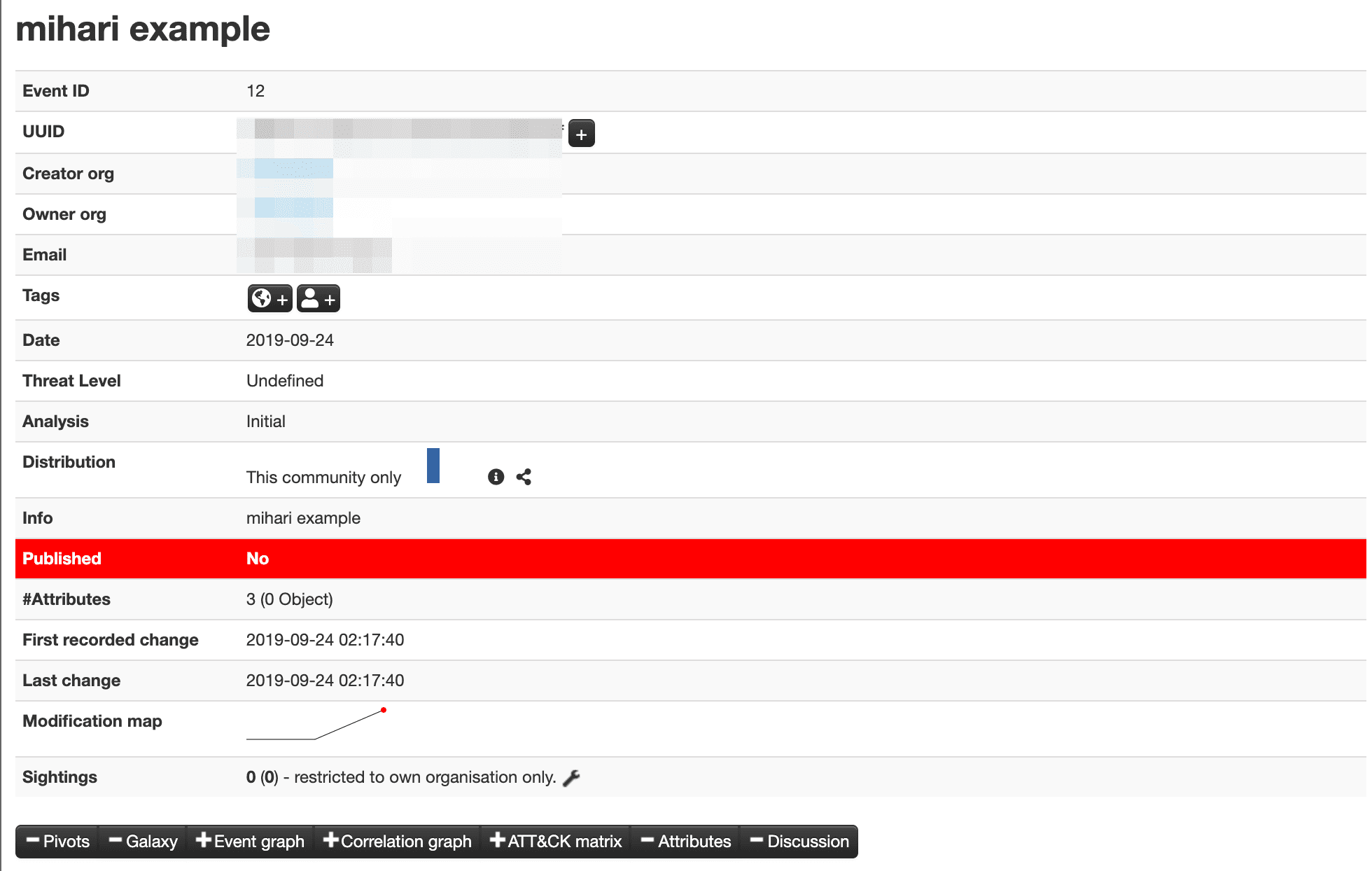
- Mihari creates an event on MISP.
- If it doesn’t contain the artifacts:
Mihari supports the following services by default.
- BinaryEdge
- Censys
- CIRCL passive DNS / passive SSL
- crt.sh
- DN Pedia
- dnstwister
- Onyphe
- OTX
- PassiveTotal
- Pulsedive
- SecurityTrails
- Shodan
- Spyse
- urlscan.io
- VirusTotal
- ZoomEye
Example
Changelog v7.2
Breaking Changes
- There are changes on the database schemas. Please do
mihari db migrateto migrate.
What’s Changed
- Renew ci by @ninoseki in #1012
- feat: add vulnerabilities table by @ninoseki in #1013
- refactor: improve factory_bot usage by @ninoseki in #1014
- feat: set q links by @ninoseki in #1015
- fix: fix typo by @ninoseki in #1016
- refactor: improve type check by @ninoseki in #1017
- refactor: unify tags behavior by @ninoseki in #1018
- feat: delete orphaned alert by @ninoseki in #1019
- refactor: remove $SAFE by @ninoseki in #1021
- feat: ensure emitters have “database” at least by @ninoseki in #1023
- refactor: split falsepositve concern by @ninoseki in #1024
- chore: change Puma’s default max threads [skip ci] by @ninoseki in #1025
- Refactoring by @ninoseki in #1026
- feat: introduce UnenrichableError by @ninoseki in #1027
- refactor: set convention for .configuration_keys by @ninoseki in #1028
- V7.2.0 by @ninoseki in #1029
Install & Use
Copyright (c) 2019 Manabu Niseki