
On October 29, 2024, Cloudflare revealed details of a DDoS attack orchestrated using a Mirai botnet comprising 13,000 compromised devices. Exploiting the UDP protocol, the attackers unleashed an overwhelming flood of data, aiming to cripple the operations of a major internet service provider (ISP) in East Asia.
Remarkably, the attack, which lasted a mere 80 seconds, caused no disruptions or service interruptions for the targeted ISP. This flawless defense was attributed to a fully automated system for detection and mitigation. From the moment the attack began, Cloudflare promptly identified the anomalous traffic and activated scrubbing protocols. Malicious data was intercepted and neutralized at Cloudflare’s edge nodes, ensuring it never reached the ISP’s infrastructure. Absent such defenses, the colossal scale of the assault would have inevitably overwhelmed the servers, leading to their collapse.
Cloudflare has not disclosed the name of the targeted ISP, but the attackers’ motive remains puzzling. Even if the ISP’s services had been incapacitated, the impact would have been limited to its customers, providing little to no tangible benefit to the hackers unless they were hired to carry out the attack.
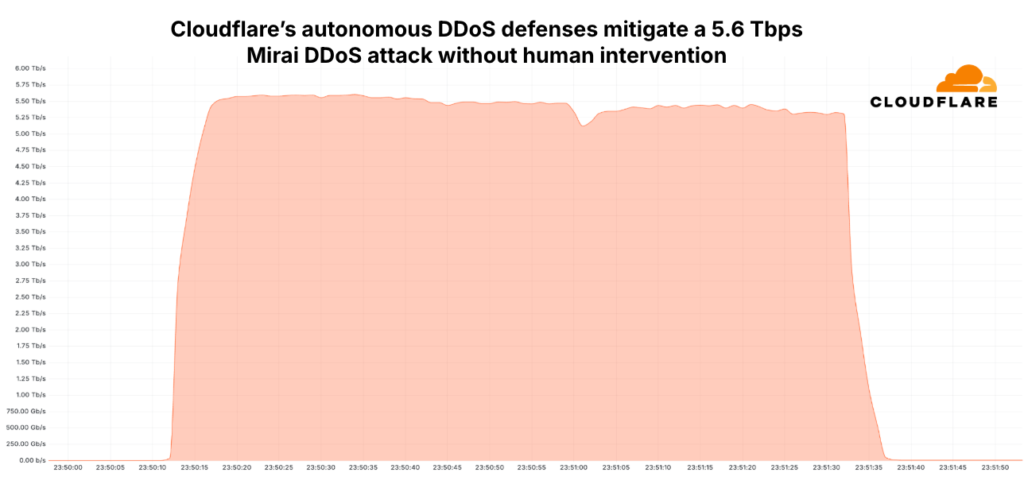
Among the 13,000 devices deployed in the botnet, each IP address generated an average traffic of approximately 4 Gbps. This event marked the highest peak traffic for a DDoS attack recorded to date, demonstrating an astonishing capability to generate such massive volumes with only 13,000 devices.
The Mirai botnet, a notorious IoT worm that rose to prominence in 2016, primarily targets networked cameras. It is highly likely that this attack also involved compromised IoT cameras. The attackers may have employed advanced techniques to amplify traffic, enabling each botnet device to send exceptionally high volumes of data.
The ISP under attack was shielded by Cloudflare Magic Transit, a service with a network capacity of 321 Tbps. As a result, the 5.6 Tbps DDoS attack was handled effortlessly, showcasing the robust resilience of Cloudflare’s infrastructure.