
A recent report by Infoblox Threat Intel uncovers the extensive and intricate use of spoofed domains in modern spam operations. Authored by Stelios Chatzistogias, Laura da Rocha, and Renée Burton, the report dives deep into campaigns leveraging neglected domains to bypass security measures and deliver malicious payloads. This investigation provides critical insights into how spammers exploit domain spoofing to evade detection and victimize users globally.
Domain spoofing, a tactic where threat actors falsify the sender’s email address to appear legitimate, plays a pivotal role in these campaigns. As the report highlights, “Threat actors can fake (spoof) the sender address of an email. They do this to make the email appear more legitimate.” Neglected domains, often those without proper DNS records like Sender Policy Framework (SPF), are prime targets due to their ability to bypass security checks.
One of the study’s key findings is the persistence of spoofed domains in circumventing existing spam filters. Despite advancements in email security, these tactics remain financially lucrative for cybercriminals. The authors note, “Most surprising is just how pervasive domain spoofing is in spam.”
The report categorizes malspam campaigns into distinct “catches” that demonstrate various tactics employed by threat actors: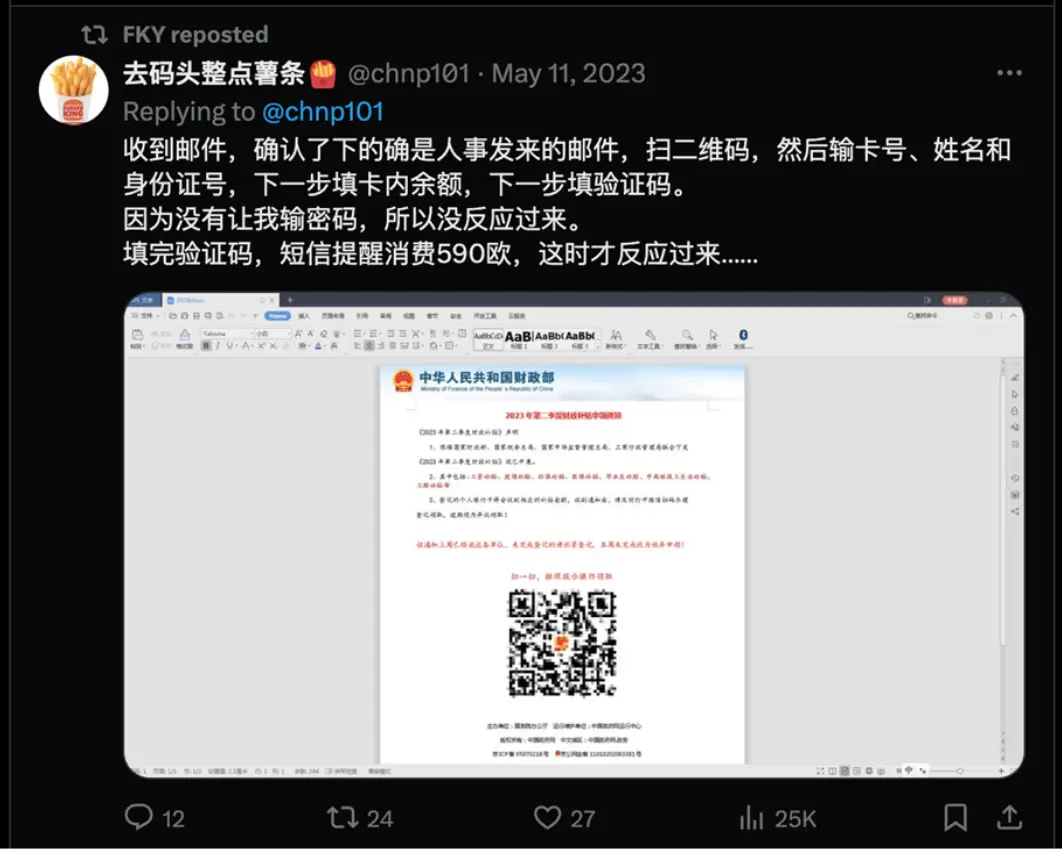
- QR Code Phishing Campaigns: Targeting residents of greater China, these campaigns use PDF attachments containing QR codes that redirect victims to phishing sites. By bypassing traditional security measures, these emails exploit encrypted chat apps like WeChat to steal financial details. Infoblox’s analysis revealed that “These campaigns use sender email addresses that had a structure matching what we observed in Muddling Meerkat DNS queries. .”
- Japanese Phishing Campaigns: Utilizing trusted brand names like Amazon, SMBC, and Mastercard, these campaigns redirect victims to fake login pages designed to harvest credentials. The report explains, “The emails urge the user to authenticate with the service due to a security concern or other problem.”
- Familiar Extortion Campaigns: These spam emails threaten recipients with fake claims of malware infections and demand cryptocurrency payments. Using spoofed sender addresses, often mimicking the recipient’s email, attackers instill fear and urgency. Infoblox observed, “The victims are asked to pay US$1800.”
- Mysterious Malspam: Some campaigns defy typical malicious patterns, featuring seemingly innocuous email attachments like freight rate spreadsheets or mutual fund values. The purpose of these campaigns remains unclear, adding a layer of mystery to the investigation.
A recurring theme in these campaigns is their potential link to Muddling Meerkat, a threat actor known for puzzling DNS operations and abuse of neglected domains. As the report states, “We extended the number of known Muddling Meerkat target domains from approximately 20 by March 2024 to over 650 today.” While not all campaigns can be definitively tied to this actor, the observed patterns align closely with their known activities.
The authors conclude, “We weren’t able to determine what Muddling Meerkat is up to, but our investigation was ultimately successful: we learned a great deal about how actors use spoofed domains in malspam.”