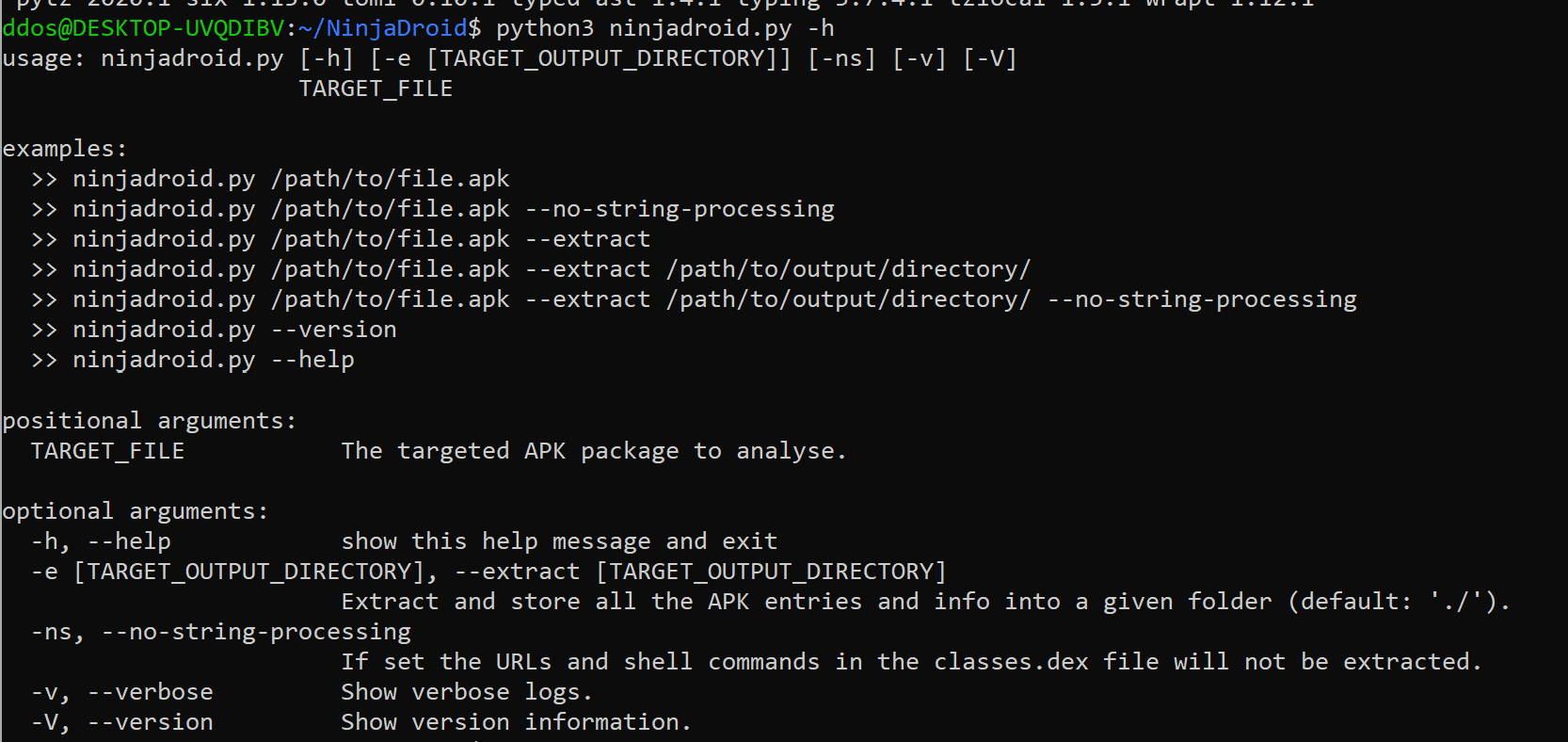
NinjaDroid v4.5 releases: reverse engineering Android APK packages
NinjaDroid
NinjaDroid is a simple tool to reverse engineering Android APK packages.
Overview:
NinjaDroid uses a modified version of the Androguard AXMLParser (by Anthony Desnos) together with a series of other Python scripts (by Paolo Rovelli) based on aapt, keytool, string, and such to extract a series of information from a given APK package, such as:
- APK file info (i.e. file size, MD5, SHA-1, SHA-256 and SHA-512);
- App info (e.g. app name, package name, version, lists of permissions, list of Activities/Services/BroadcastReceivers, etc…);
- Digital certificate info (e.g. validity, serial number, fingerprint MD5, SHA-1, SHA-256, and signature), including certificate issuer/owner info (e.g. name, email, company, country, etc…);
- All the strings hard-coded into the classes.dex file;
- The URLs and shell command hard-coded into the classes.dex file;
- AndroidManifest file info (i.e. file size, MD5, SHA-1, SHA-256 and SHA-512);
- classes.dex file info (i.e. file size, MD5, SHA-1, SHA-256 and SHA-512);
- CERT.RSA/DSA file info (i.e. file size, MD5, SHA-1, SHA-256 and SHA-512);
- List of file entries (i.e. file name, file size, MD5, SHA-1, SHA-256, and SHA-512) in the APK package.
Furthermore, NinjaDroid uses apktool and dex2jar, together with other Python scripts in order to extract from an APK package:
- classes.dex file;
- translated .jar file (thanks to dex2jar);
- disassembled smali files (thanks to apktool);
- AndroidManifest.xml file (thanks to apktool);
- CERT.RSA file;
- assets/ and res/ folders together with their content (thanks to apktool );
- JSON and HTML report files, which contains all the extracted APK metadata.
Installation:
$ git clone https://github.com/rovellipaolo/NinjaDroid
$ cd NinjaDroid
$ pip3 -r requirements.txt
Use
Copyright (C) 2020 rovellipaolo
Source: https://github.com/rovellipaolo/