Researchers release PoC exploit for ManageEngine RCE (CVE-2022-47966)
Horizon3.ai red-teamer James Horseman released a proof-of-concept (PoC) exploit and technical analysis for authentication remote code execution vulnerability in Zoho’s ManageEngine products (CVE-2022-47966) and warns organizations to brace for “spray and pray” attacks across the internet.
Multiple ManageEngine products could allow a remote attacker to execute arbitrary code on the system, caused by the usage of an outdated third-party dependency, Apache Santuario. If SAML single sign-on is currently or has been previously enabled on those products, an attacker could send a SAML request with an invalid signature to execute arbitrary code on the system.
“This vulnerability allows an unauthenticated adversary to execute arbitrary code,” Zoho warned in an advisory.
CVE-2022-47966 affects the following ManageEngine products:
- Access Manager Plus
- Active Directory 360
- ADAudit Plus
- ADManager Plus
- ADSelfService Plus
- Analytics Plus
- Application Control Plus
- Asset Explorer
- Browser Security Plus
- Device Control Plus
- Endpoint Central
- Endpoint Central MSP
- Endpoint DLP
- Key Manager Plus
- OS Deployer
- PAM 360
- Password Manager Pro
- Patch Manager Plus
- Remote Access Plus
- Remote Monitoring and Management (RMM)
- ServiceDesk Plus
- ServiceDesk Plus MSP
- SupportCenter Plus
- Vulnerability Manager Plus
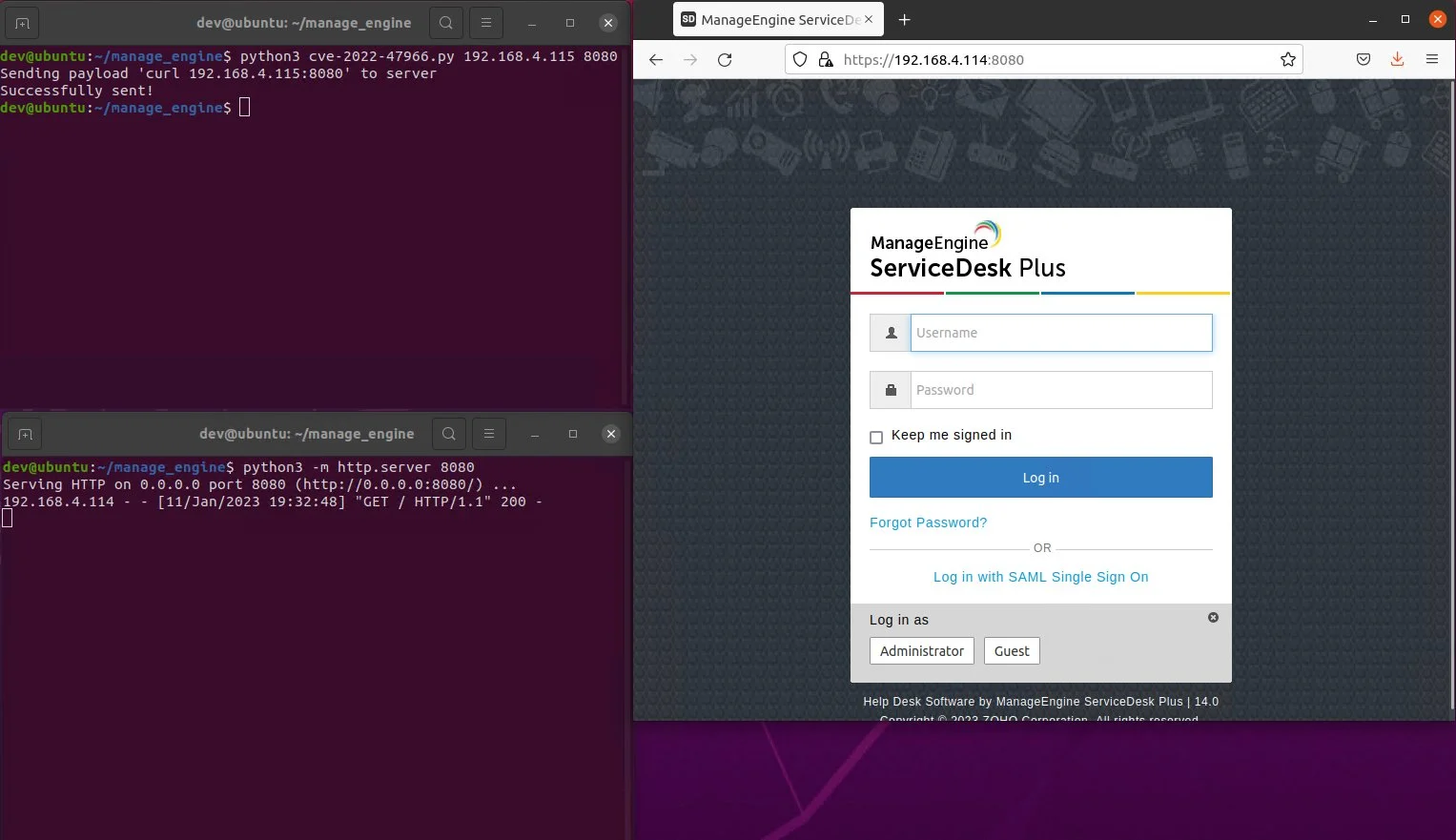
James Horseman released Indicators of Compromise (IOCs) associated with the flaw before and today proof-of-concept (PoC) exploit code is now available for CVE-2022-47966. “Shodan data shows that there are likely more than a thousand instances of ManageEngine products exposed to the internet with SAML currently enabled,” Horseman said.
“The vulnerability allows an attacker to gain remote code execution by issuing a HTTP POST request containing a malicious SAML response,” the researchers wrote.
“This POC abuses the pre-authentication remote code execution vulnerability to run a command with Java’s Runtime.exec method.”
The POC only works on products utilizing Apache Santuario (xmlsec) <= 1.4.1 such as ServiceDesk Plus, Endpoint Central, ADManager Plus, and ADSelfService Plus.
Zoho issued patches late last year and urged customers to patch this critical-severity security flaw.






