RomCom Exploits Zero-Days in Firefox (CVE-2024-9680) & Windows (CVE-2024-49039) with No User Interaction
In a recent cybersecurity report, ESET researchers have unveiled a coordinated attack by the Russia-aligned threat actor RomCom, exploiting zero-day vulnerabilities in both Mozilla Firefox and Microsoft Windows. These vulnerabilities—previously unknown and exploited in the wild—enable attackers to execute malicious code without user interaction, demonstrating a high level of sophistication.
ESET detailed how RomCom utilized a combination of two critical vulnerabilities:
- CVE-2024-9680: A use-after-free bug in Firefox’s animation timeline feature with a CVSS score of 9.8. According to ESET, the flaw “allows vulnerable versions of Firefox, Thunderbird, and the Tor Browser to execute code in the restricted context of the browser.” Mozilla quickly addressed this vulnerability on October 9, 2024, within just 25 hours of receiving the report, a turnaround praised as “very impressive in comparison to industry standards.”
- CVE-2024-49039: A privilege escalation flaw in Windows’ Task Scheduler service, rated 8.8 on the CVSS scale. This vulnerability allowed RomCom to bypass Firefox’s sandbox and escalate privileges. Exploitation of this flaw was confirmed by Microsoft, which released a patch on November 12, 2024.
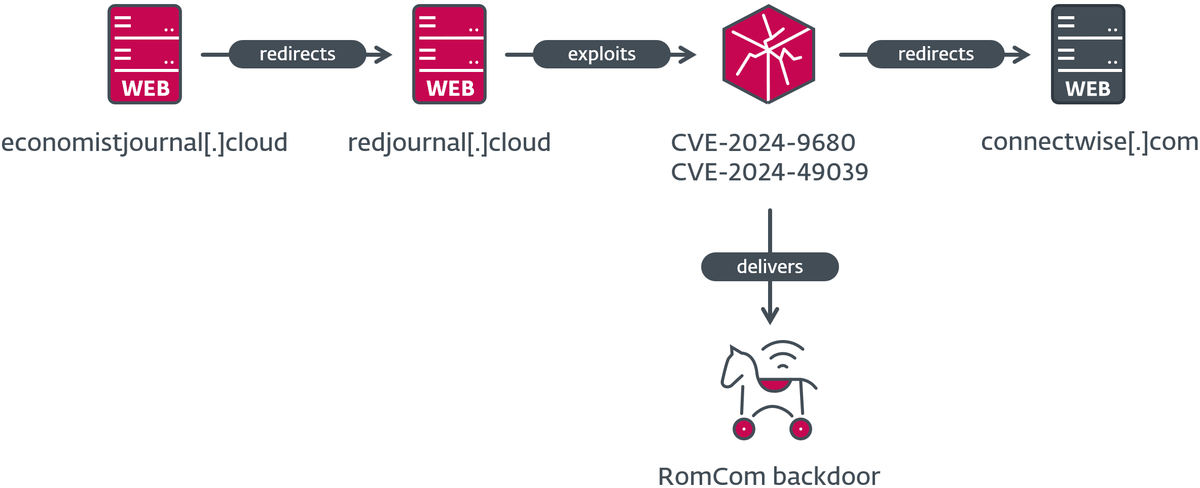
When combined, these vulnerabilities enabled zero-click exploitation, where victims only needed to visit a malicious webpage for the attack to succeed. As described by ESET, “an adversary can run arbitrary code – without any user interaction required – which in this case led to the installation of RomCom’s eponymous backdoor on the victim’s computer.”
RomCom, also referred to as Storm-0978 or Tropical Scorpius, is known for its dual focus on cybercrime and espionage. In this campaign, the group used the exploits to deliver their RomCom backdoor, a tool capable of executing commands and downloading additional malicious payloads. ESET’s telemetry revealed widespread targeting, with victims primarily located in Europe and North America.
The group employed fake domains mimicking legitimate websites to redirect victims to exploit-hosting servers. For example:
redircorrectiv[.]commimicked the nonprofit newsroom Correctiv.devolredir[.]comimpersonated Devolutions, a provider of remote access solutions.
This tactic allowed RomCom to blend malicious activity with legitimate web traffic, reducing the likelihood of detection.
The Firefox exploit leveraged heap spraying and animation object manipulation to trigger the use-after-free vulnerability, ultimately enabling attackers to execute shellcode. In contrast, the Windows flaw exploited an undocumented RPC interface in the Task Scheduler service, allowing privilege escalation and sandbox escape.
ESET noted that the malicious Windows library, named PocLowIL, used weak security descriptors that permitted unauthorized access to the RPC interface. The updated patch restricts access, effectively neutralizing the attack vector.
ESET credited the swift collaboration with Mozilla and Microsoft in mitigating these vulnerabilities. Following ESET’s initial discovery on October 8, 2024, Mozilla released patches for Firefox, Thunderbird, and the Tor Browser within a day. Microsoft required additional time to address the sandbox escape issue, deploying a comprehensive fix through KB5046612 on November 12, 2024.
The RomCom exploit campaign highlights the increasing sophistication of nation-state-aligned threat actors and the critical importance of rapid vulnerability disclosure and patching. As ESET emphasized: “Chaining together two zero-day vulnerabilities armed RomCom with an exploit that requires no user interaction. This level of sophistication shows the threat actor’s will and means to obtain or develop stealthy capabilities.”
Organizations using affected versions of Firefox, Thunderbird, or Windows are urged to apply the latest updates immediately to safeguard against such advanced threats.
For more information, read the full report by ESET.
Related Posts:
- Firefox Zero-Day Vulnerability: Urgent Update Needed to Patch CVE-2024-9680
- RomCom Group’s Underground Ransomware Exploits Microsoft Zero-Day Flaw
- New RomCom Variant “SnipBot” Unveiled: A Sophisticated Malware Targeting Enterprise Networks
- UAT-5647 Unleashes RomCom Malware in Attacks on Ukraine and Poland