SharpSploit v1.6 releases: a .NET post-exploitation for red teamers
SharpSploit is a .NET post-exploitation library written in C# that aims to highlight the attack surface of .NET and make the use of offensive .NET easier for red teamers.
SharpSploit is named, in part, as a homage to the PowerSploit project, a personal favorite of mine! While SharpSploit does port over some functionality from PowerSploit, my intention is not at all to create a direct port of PowerSploit. SharpSploit will be its own project, albeit with similar goals to PowerSploit.
SharpSploit.Credentials
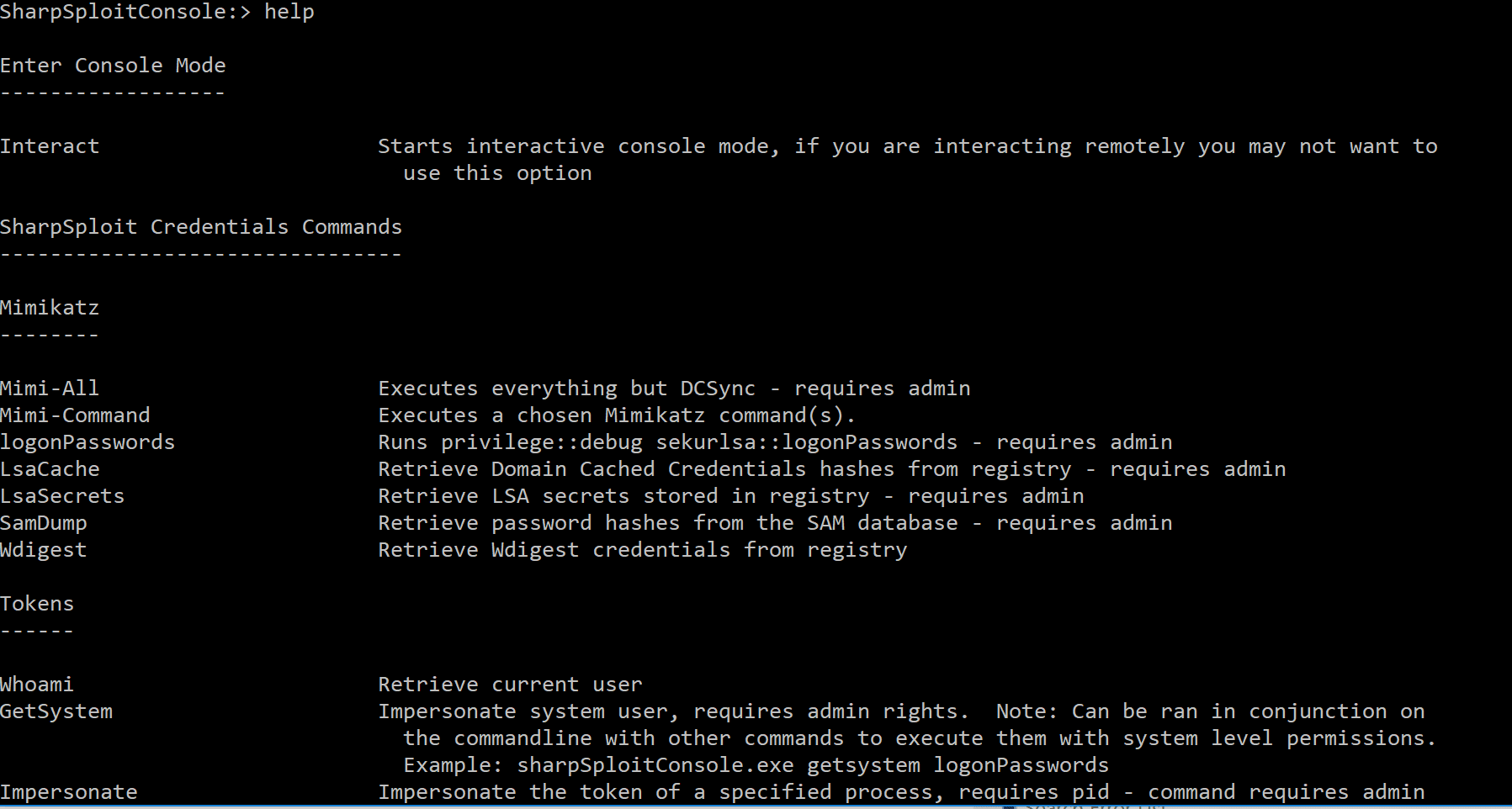
SharpSploit.Credentials.Mimikatz
Command()– Loads the Mimikatz PE withPE.Load()and executes a chosen Mimikatz command.LogonPasswords()– Loads the Mimikatz PE withPE.Load()and executes the Mimikatz command to retrieve plaintext passwords from LSASS. Equates toCommand("privilege::debug sekurlsa::logonPasswords"). (Requires Admin)SamDump()– Loads the Mimikatz PE withPE.Load()and executes the Mimikatz command to retrieve password hashes from the SAM database. Equates toCommand("privilege::debug lsadump::sam"). (Requires Admin)LsaSecrets()– Loads the Mimikatz PE withPE.Load()and executes the Mimikatz command to retrieve LSA secrets stored in registry. Equates toCommand("privilege::debug lsadump::secrets"). (Requires Admin)LsaCache()– Loads the Mimikatz PE withPE.Load()and executes the Mimikatz command to retrieve Domain Cached Credentials hashes from registry. Equates toCommand("privilege::debug lsadump::cache"). (Requires Admin)Wdigest()– Loads the Mimikatz PE withPE.Load()and executes the Mimikatz command to retrieve Wdigest credentials from registry. Equates toCommand("sekurlsa::wdigest").All()– Loads the Mimikatz PE withPE.Load()and executes each of the above builtin, local credential dumping commands. (Requires Admin)DCSync()– Loads the Mimikatz PE withPE.Load()and executes the “dcsync” module to retrieve the NTLM hash of a specified (or all) Domain user. (Requires Domain Admin (or equivalent rights))PassTheHash()– Loads the Mimikatz PE withPE.Load()and executes the “pth” module to start a new process as a user using an NTLM password hash for authentication. (Requires Admin)
Changelog v1.6
Added
- Added ManualMapping functions (credit @b33f, @TheWover)
- Added ModuleOverloading functions (credit @b33f)
- Added Syscall stub function (credit @b33f)
- Added SharpSploit.Execution.Injection namespace (credit @TheWover)
- Added SharpSploit.Pivoting namespace, reverse port forwarding (credit @rasta-mouse)
Download && Use
Copyright 2018, Ryan Cobb (@cobbr_io)






