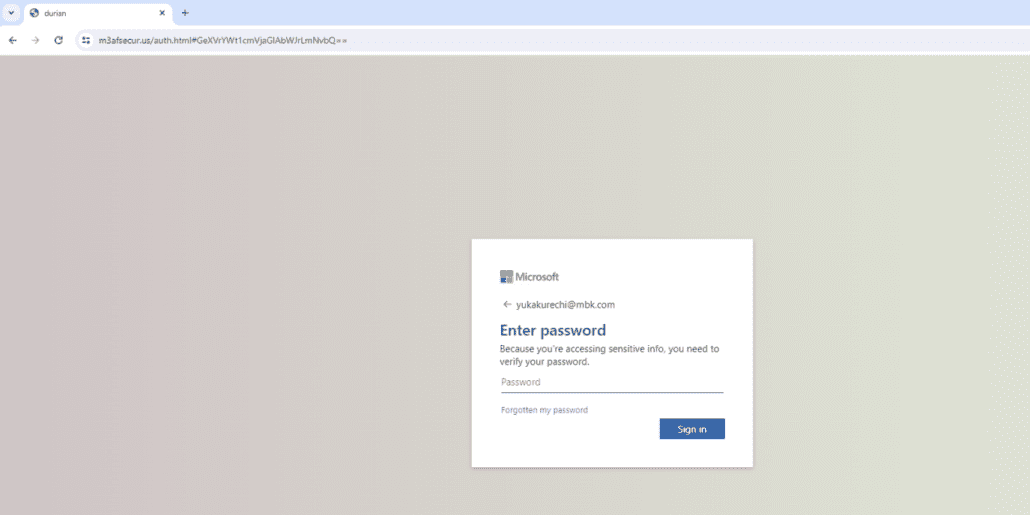
Microsoft Phishing Page with prefilled username
SEKOIA’s Threat Detection & Research (TDR) team has exposed a new Adversary-in-the-Middle (AiTM) phishing kit, dubbed “Sneaky 2FA.” This sophisticated tool, marketed as Phishing-as-a-Service (PhaaS), is designed to exploit Microsoft 365 accounts by bypassing Multi-Factor Authentication (MFA).
First identified in December 2024, the Sneaky 2FA phishing kit is sold by a cybercrime service known as “Sneaky Log.” This service operates through a fully-featured Telegram bot, providing cybercriminals access to the kit for $200 per month. As SEKOIA reported, “Customers reportedly receive access to a licensed obfuscated version of the source code and deploy it independently.”
The phishing pages primarily target Microsoft 365 users and leverage compromised infrastructure, such as WordPress websites, to host their campaigns. One hallmark of Sneaky 2FA’s tactics is the use of an “autograb” functionality. By embedding the victim’s email address directly into phishing URLs, the kit pre-fills fake Microsoft login pages, creating a seamless but fraudulent experience for victims.
Sneaky 2FA incorporates various features to evade detection, including:
- Obfuscation: HTML and JavaScript code is obfuscated, embedding junk data and using base64-encoded images.
- Anti-analysis Techniques: The phishing kit employs anti-debugging methods to thwart security tools.
- Traffic Filtering: The kit redirects non-target traffic to benign sites, such as Wikipedia pages, using the href.li redirection service.
The phishing flow mimics legitimate Microsoft authentication processes, fooling users into providing login credentials and completing MFA steps. SEKOIA noted, this emerging phishing kit “aims to harvest Microsoft 365 session cookies to bypass the MFA process during subsequent authentication.”
Despite its sophistication, Sneaky 2FA exhibits certain patterns that offer detection opportunities. These include:
- Impossible Device Shift: The phishing kit uses hardcoded User-Agent strings for different authentication steps, which deviate from typical user behavior.
- Unique URL Patterns: The phishing pages feature 150-character URLs with paths like
/index,/verify, and/validate, allowing for tracking. - Cloudflare Turnstile Challenges: The kit uses these challenges to filter bots from genuine victims.
SEKOIA has already identified approximately 100 domains hosting Sneaky 2FA phishing pages, including both compromised sites and those registered by the phishing service’s customers.

The Sneaky Log service, which advertises the phishing kit on Telegram, exemplifies the professionalization of cybercrime. Its bot automates subscription management, support, and even cryptocurrency payments, employing advanced transaction obfuscation techniques.