SQL injection: bypass WAF using tamper script on SQLmap
WAF (web application firewall) has become one of the standard security solutions. It is because of it, many companies do not care even have a web application vulnerabilities. Unfortunately, not all are non-waf bypass! This article will tell you how to use the tamper script on SQLMap bypass WAFs/IDSs.
Tamper script will modify request to evade detection WAF rules. Many times, you need to use more than one tamper scripts.
E.x: If you use “space2hash.py” and “space2morehash.py” tamper scripts, these script will automatically convert all spaces to random comments, and expand version of this script (space2morehash.py) will help you come to “disrupt” functions to bypass WAF.
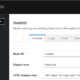
Input: 1 AND 1234=1234
Output: 1%23PTTmJopxdWJ%0AAND%23cWfcVRPV%0A1234=1234
To use tamper script on sqlmap, you use –tamper flag.
To test mysql, you can use all tamper below:
To test mssql, you can use all tamper below:
Below is tamper list that support both mssql and mysql
You can view this demo video
https://www.youtube.com/watch?v=e9w_jhkVYFI