Storm-0940 and CovertNetwork-1658: Insights into Chinese Cyberattack Infrastructure
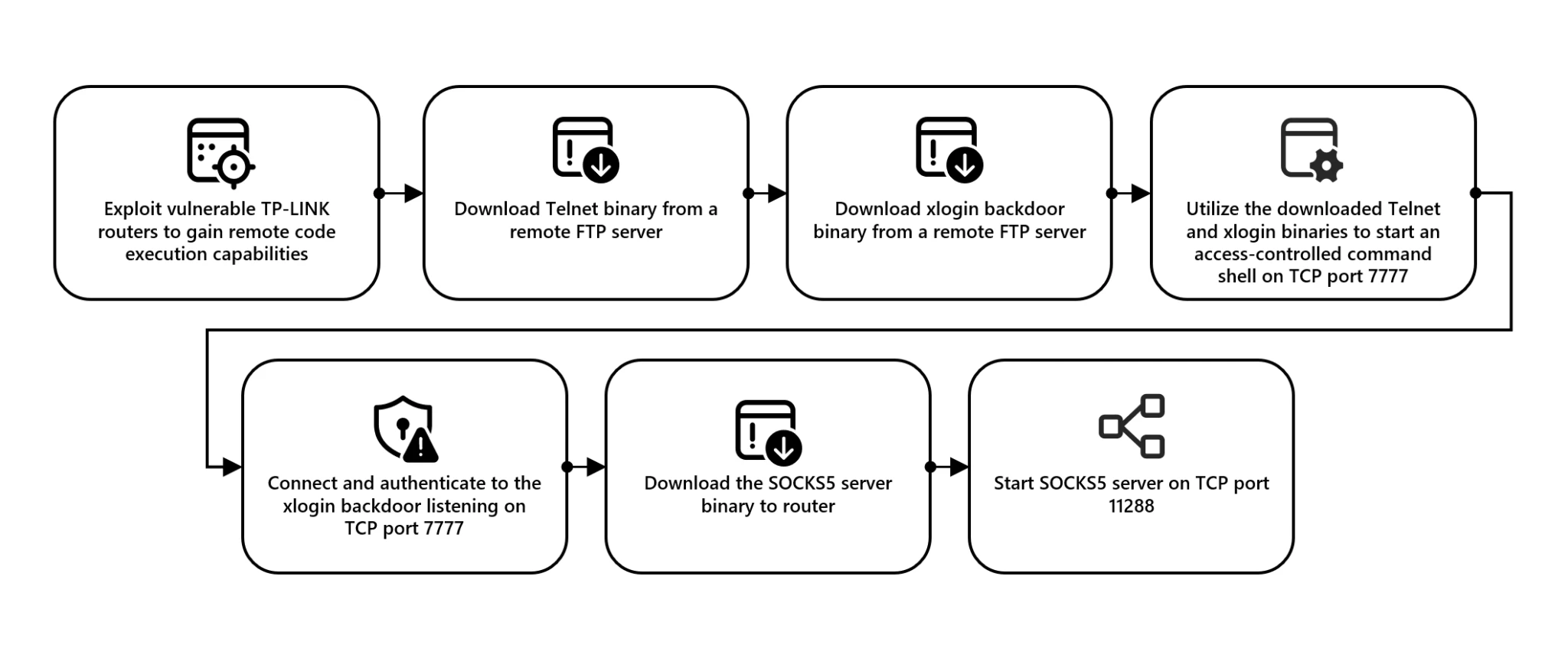
In recent findings, Microsoft Threat Intelligence has identified a concerning escalation in the activity of a Chinese state-affiliated threat actor, Storm-0940. This group, active since at least 2021, has been exploiting compromised credentials obtained from covert password spray attacks facilitated by an extensive network of compromised devices, referred to as CovertNetwork-1658, also known as “xlogin” or the “7777 network.”
Since August 2023, Microsoft has observed a sharp increase in “highly evasive password spray attacks” originating from CovertNetwork-1658, which consists of compromised small office and home office (SOHO) routers, mostly manufactured by TP-Link. These attacks target organizations in North America and Europe, focusing on high-value entities, including think tanks, government agencies, and defense firms. “Microsoft has linked the source of these password spray attacks to a network of compromised devices we track as CovertNetwork-1658,” Microsoft reported.
One notable actor using CovertNetwork-1658’s credentials is the Chinese threat group Storm-0940. Known for its relentless attacks on organizations across North America and Europe, Storm-0940 employs a mix of brute-force techniques, password spraying, and network-edge exploits to gain unauthorized access. Their targets include think tanks, government organizations, NGOs, law firms, and defense entities, illustrating a broad spectrum of interest and impact. Microsoft’s report highlights the close connection between the operators of CovertNetwork-1658 and Storm-0940, suggesting a well-coordinated effort: “Storm-0940 was observed using compromised credentials that were obtained from CovertNetwork-1658 infrastructure on the same day,” indicating a quick operational turnover in compromised credentials.
What makes CovertNetwork-1658’s approach especially challenging to detect is its low-volume attack method. Rather than bombarding accounts with multiple attempts, the network initiates only one sign-in attempt per account per day in 80% of cases. This minimalistic approach keeps it under the radar of most security measures, making it difficult to identify as a coordinated attack. “Monitoring for multiple failed sign-in attempts from one IP address or to one account will not detect this activity,” Microsoft’s report points out, underlining the challenge for cybersecurity teams.
Despite exposure from security reports, including those from Sekoia and Team Cymru, which led to a decline in CovertNetwork-1658’s usage, recent Microsoft observations suggest the network is evolving. There is evidence of CovertNetwork-1658 acquiring new infrastructure, likely with modified digital fingerprints to avoid detection. This development signals that CovertNetwork-1658 is far from inactive, as threat actors constantly adapt to maintain operational continuity.