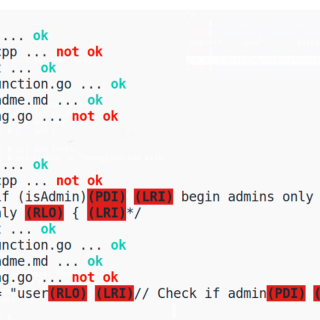
TrojanSourceFinder v1.1.4 releases: detect “Trojan Source” vulnerability in source code
TrojanSourceFinder TrojanSourceFinder helps developers detect “Trojan Source” vulnerability in source code. Trojan Source vulnerability allows an attacker to make malicious code appear innocent. In general, the attacker tries to lure by passing his code...