Using Nessus and Metasploit Together
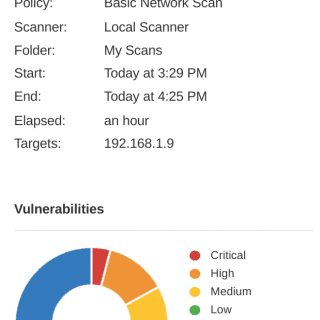
Introduction to Nessus Nessus is a vulnerability scanning and analysis software from tenable, a leading information security services company, known as “the world’s most popular vulnerability scanner, used by more than 75,000 organizations worldwide.”...