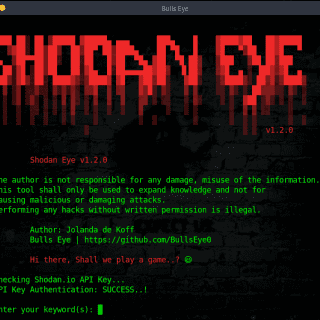
shodan eye: collects all information about all devices that are directly connected to the internet
Shodan Eye This tool collects all information about all devices that are directly connected to the internet with the specified keywords that you enter. This way you get a complete overview. The types of...