Tokenizer: Kernel Mode Driver for Elevating Process Privileges
Tokenizer
Tokenizer is a kernel mode driver project that allows the replacement of a process token in EPROCESS with a system token, effectively elevating the privileges of the process. The driver is designed to be used with a user-mode application that sends a process ID to the driver through an IOCTL.
Technical details
-
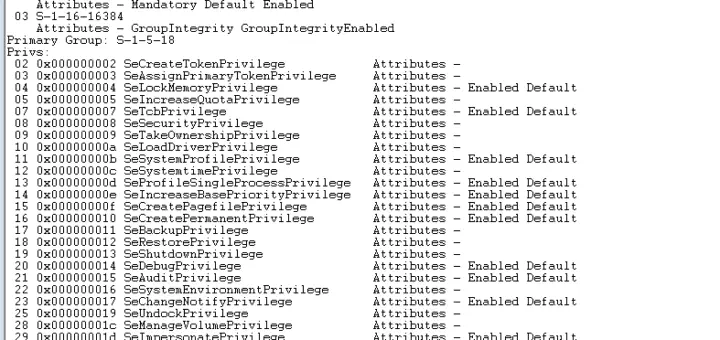
When a process is created, it inherits the token of the user who created it, The token is used by the system to determine what actions the process can perform. The token contains information about the user’s security identifier (SID), group memberships, and privileges.
-
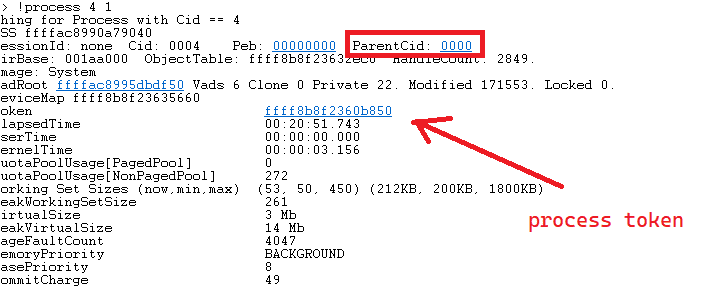
The Token member resides at offset
0x4b8in the_EPROCESSstructure, which is a data structure that represents a process object. The Token member is defined in_EX_FAST_REFstructure, which is a union type that can store either a pointer to a kernel object or a reference count, depending on the size of the pointer, The offset of the_EX_FAST_REFstructure within_EPROCESSdepends on the specific version of Windows being used, but it is typically located at an offset of0x4b8in recent versions of Windows. -
Windows Build Number token Offsets for x64 and x86 Architectures
x64 offsets x86 offsets 0x0160 (late 5.2) 0x0150 (3.10) 0x0168 (6.0) 0x0108 (3.50 to 4.0) 0x0208 (6.1) 0x012C (5.0) 0x0348 (6.2 to 6.3) 0xC8 (5.1 to early 5.2) 0x0358 (10.0 to 1809) 0xD8 (late 5.2) 0x0360 (1903) 0xE0 (6.0) 0x04B8 0xF8 (6.1) 0xEC (6.2 to 6.3) 0xF4 (10.0 to 1607) 0xFC (1703 to 1903) 0x012C 
-
The
_EX_FAST_REFstructure in Windows contains three members:ObjectandRefCountandValue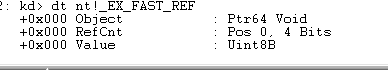
-
To display the process token in
_EX_FAST_REF,We pass the address of the_EX_FAST_REFstructure that contains the token, which is typically located at an offset of0x4b8in the_EPROCESSstructure.”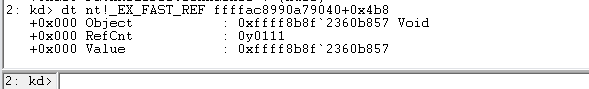
Usage
-
You can either spawn a privileged process or elevate an already existing process ID.
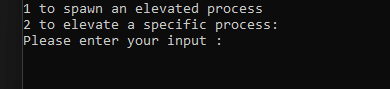
-
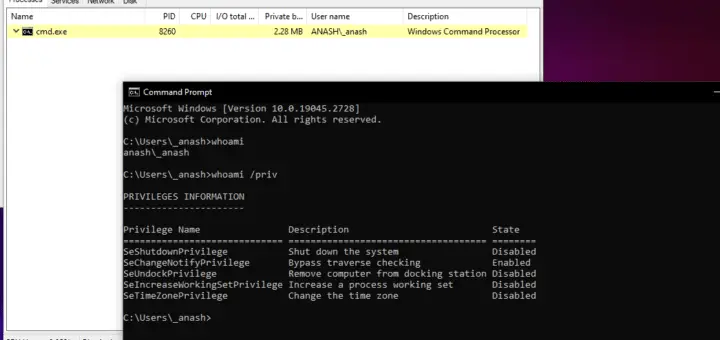
For the sake of this explanation, we will focus on the second option and use CMD as an example
-
inherited Token
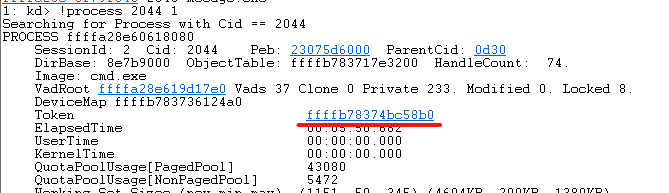
-
send the Process ID to the driver through an IOCTL
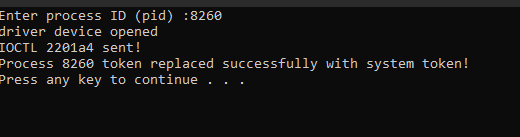
-
After receiving the PID from the user mode application, the driver uses it to obtain a pointer to the
_EPROCESSstructure for the target process. The driver then accesses the Token member of the_EPROCESSstructure to obtain a pointer to the process token, which it replaces with the system token, effectively changing the security context of the process to that of the system. However, if the driver does not correctly locate the Token member within the_EPROCESSstructure or if the offset of the Token is other than0x4b8, the driver may crash the system or the target process ,this problem will be fixed in the next updates .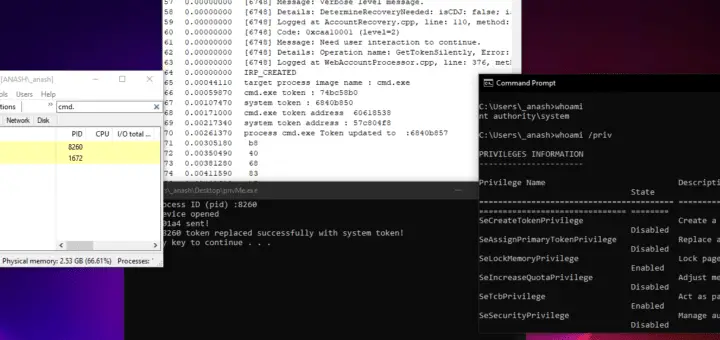
-
cmd token after
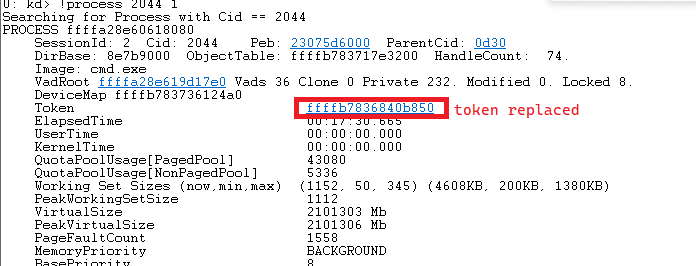
-
the process privileges, groups, rights