clair v4.7.2 releases: Vulnerability Static Analysis for Containers
Clair
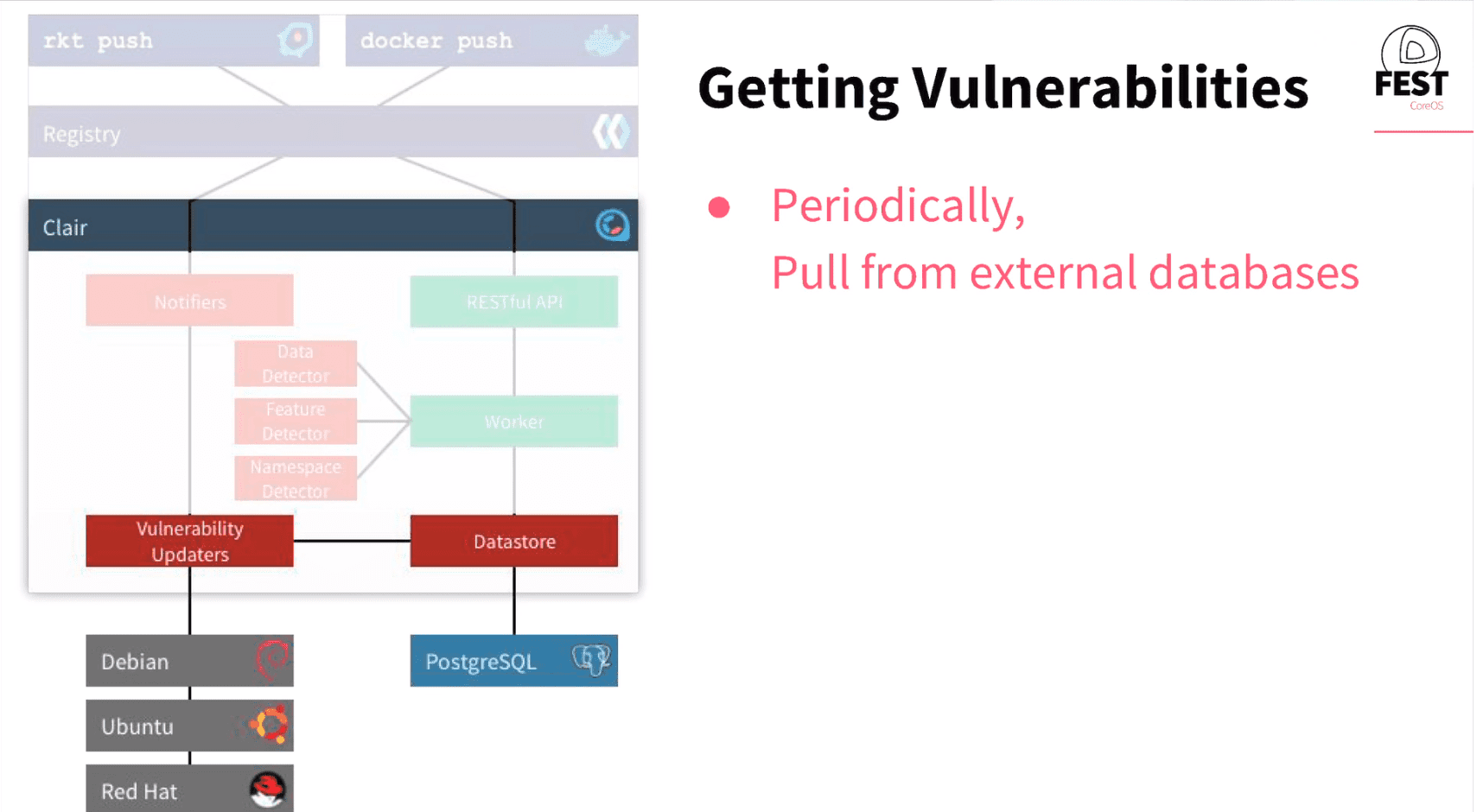
Clair is an open-source project for the static analysis of vulnerabilities in application containers (currently including appc and docker).
- In regular intervals, Clair ingests vulnerability metadata from a configured set of sources and stores it in the database.
- Clients use the Clair API to index their container images; this creates a list of features present in the image and stores them in the database.
- Clients use the Clair API to query the database for vulnerabilities of a particular image; correlating vulnerabilities and features is done for each request, avoiding the need to rescan images.
- When updates to vulnerability metadata occur, a notification can be sent to alert systems that a change has occurred.
Our goal is to enable a more transparent view of the security of the container-based infrastructure. Thus, the project was named Clair after the French term which translates to clear, bright, transparent.
Terminology
Container
- Container – the execution of an image
- Image – a set of tarballs that contain the filesystem contents and run-time metadata of a container
- Layer – one of the tarballs used in the composition of an image, often expressed as a filesystem delta from another layer
Specific to Clair
- Ancestry – the Clair-internal representation of an Image
- Feature – anything that when present in a filesystem could be an indication of a vulnerability (e.g. the presence of a file or an installed software package)
- Feature Namespace (featurens) – a context around features and vulnerabilities (e.g. an operating system or a programming language)
- Vulnerability Source (vulnsrc) – the component of Clair that tracks upstream vulnerability data and imports them into Clair’s database
- Vulnerability Metadata Source (vulnmdsrc) – the component of Clair that tracks upstream vulnerability metadata and associates them with vulnerabilities in Clair’s database
Changelog v4.7.2
Claircore
- chore: update claircore to v1.5.19
- crda: remove crda support
- chore: update toolkit to latest version v1.1.1
Clair
- admin: add pre v4.7.3 admin command to create index
- contrib: add grafana dashboards for deletion metrics
- docs: add dropins to prose documentation
Install && Use
Copyright (C) 2015 coreos






