Weaponizing Windows Defender: New Attack Bypasses EDR
Researchers Jonathan Beierle and Logan Goins have uncovered a novel offensive tactic leveraging Microsoft’s Windows Defender Application Control (WDAC). Their research highlights how adversaries can weaponize WDAC to disable Endpoint Detection and Response (EDR) systems, undermining traditional cybersecurity defenses.
WDAC, a powerful feature introduced in Windows 10 and Windows Server 2016, offers organizations granular control over executable code permitted on their systems. While typically a defensive tool, Beierle and Goins expose its potential for offensive use, emphasizing that “WDAC can also be utilized offensively… to block telemetry sources and security solutions such as Endpoint Detection and Response (EDR) sensors.”
Adversaries can exploit WDAC to apply restrictive policies that prevent EDR software from running, effectively neutralizing the very tools meant to protect systems. With administrative access, attackers can remotely deploy malicious WDAC policies to disable security measures across endpoints, providing them with an unmonitored environment to carry out further malicious activities.
The research outlines a three-phase approach to weaponizing WDAC:
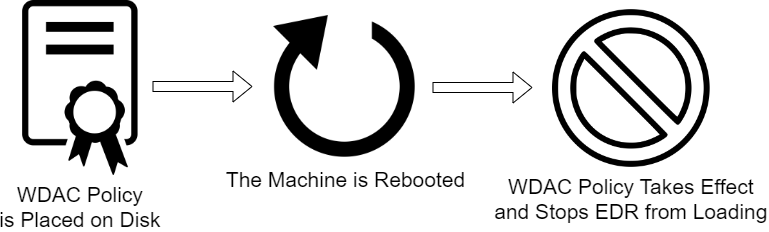
Attack Technique | Source: Jonathan Beierle
- Deploy the Policy: An attacker places a crafted WDAC policy in the C:\Windows\System32\CodeIntegrity directory.
- Reboot the System: The policy takes effect upon reboot, blocking EDR drivers and applications from running.
- Exploit the Environment: With EDR disabled, the adversary gains freedom to execute additional tools and move laterally within the network.
For broader impact, attackers with administrative access to Active Directory domains can distribute malicious policies via Group Policy Objects (GPOs), enabling a systematic takedown of security defenses across all endpoints.
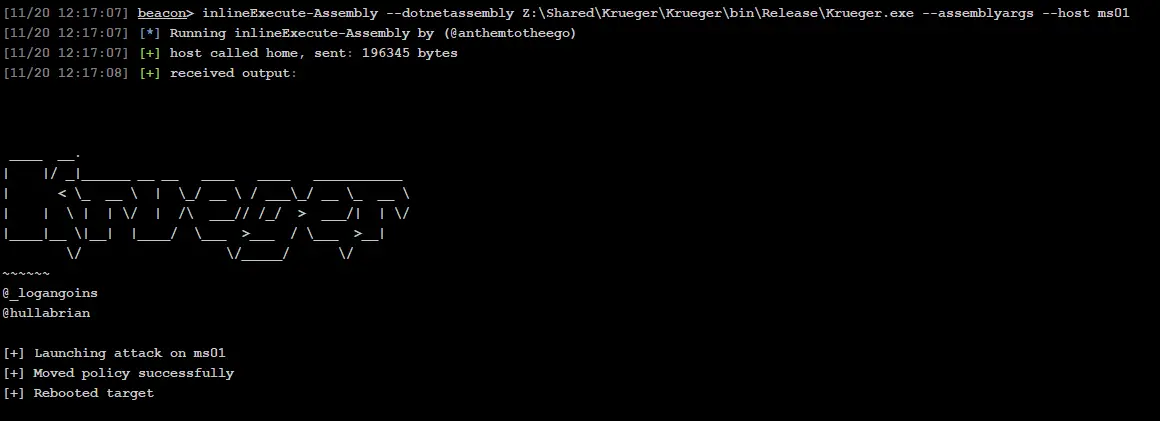
To streamline this process, Goins developed Krueger, a .NET-based post-exploitation tool designed for disabling EDR remotely. According to the research, Krueger can deploy malicious WDAC policies directly into the target’s CodeIntegrity folder and initiate a system reboot. The researchers caution that “every EDR sensor on every endpoint could be stopped within a relatively short period of time by simply applying a WDAC policy and rebooting the machines.”
Detecting this attack is challenging due to the speed and simplicity of the execution. The researchers stress the importance of mitigation strategies, recommending organizations enforce robust WDAC policies through GPOs. By locking down permissions to sensitive directories and adhering to the principle of least privilege, organizations can significantly reduce the risk of such attacks.
Furthermore, defenders are encouraged to proactively scan and verify WDAC policies for malicious configurations. However, as the researchers warn, “detecting specific blocking rules based off of compiled WDAC policies is extraordinarily difficult given how WDAC policies are structured.”
Beierle and Goins conclude, “WDAC provides an excellent tool for defenders to block potential threats from execution on Windows endpoints, but WDAC can also be utilized offensively.”





