Windows Hardening v0.9.2 releases: Windows Hardening settings and configurations
HardeningKitty and Windows 10 Hardening
Introduction
This is a hardening checklist that can be used in private and business environments for hardening Windows 10. The checklist can be used for all Windows versions, but in Windows 10 Home the Group Policy Editor is not integrated and the adjustment must be done directly in the registry. For this, there is the HailMary mode from HardeningKitty.
The settings should be seen as a security and privacy recommendation and should be carefully checked whether they will affect the operation of your infrastructure or impact the usability of key functions. It is important to weigh security against usability.
The project started with the creation of a simple hardening checklist for Windows 10. The focus has shifted to the audit of various well-known frameworks/benchmarks with the development of HardeningKitty. Meanwhile, various CIS benchmarks and Microsoft Security Baselines are supported. With the development of the HailMary mode, it will also be possible to apply the settings of any Hardening Checklist on a Windows system.
Policy Analyzer (deprecated)
Policy Analyzer reads out and compares local registry and local policy values to a defined baseline. The PolicyRule file from aha-181 contains all rules which are needed to check Group Policy and Registry settings that are defined in the Windows 10 Hardening checklist.
Policy Analyzer supports the hardening checklist up to version 0.2.0, additional entries are not yet supported. Policy Analyzer is not able to query all values of the hardening checklist. With the development of HardeningKitty, the support of Policy Analyzer has become obsolete. There will no longer be a new version of the PolicyRule file.
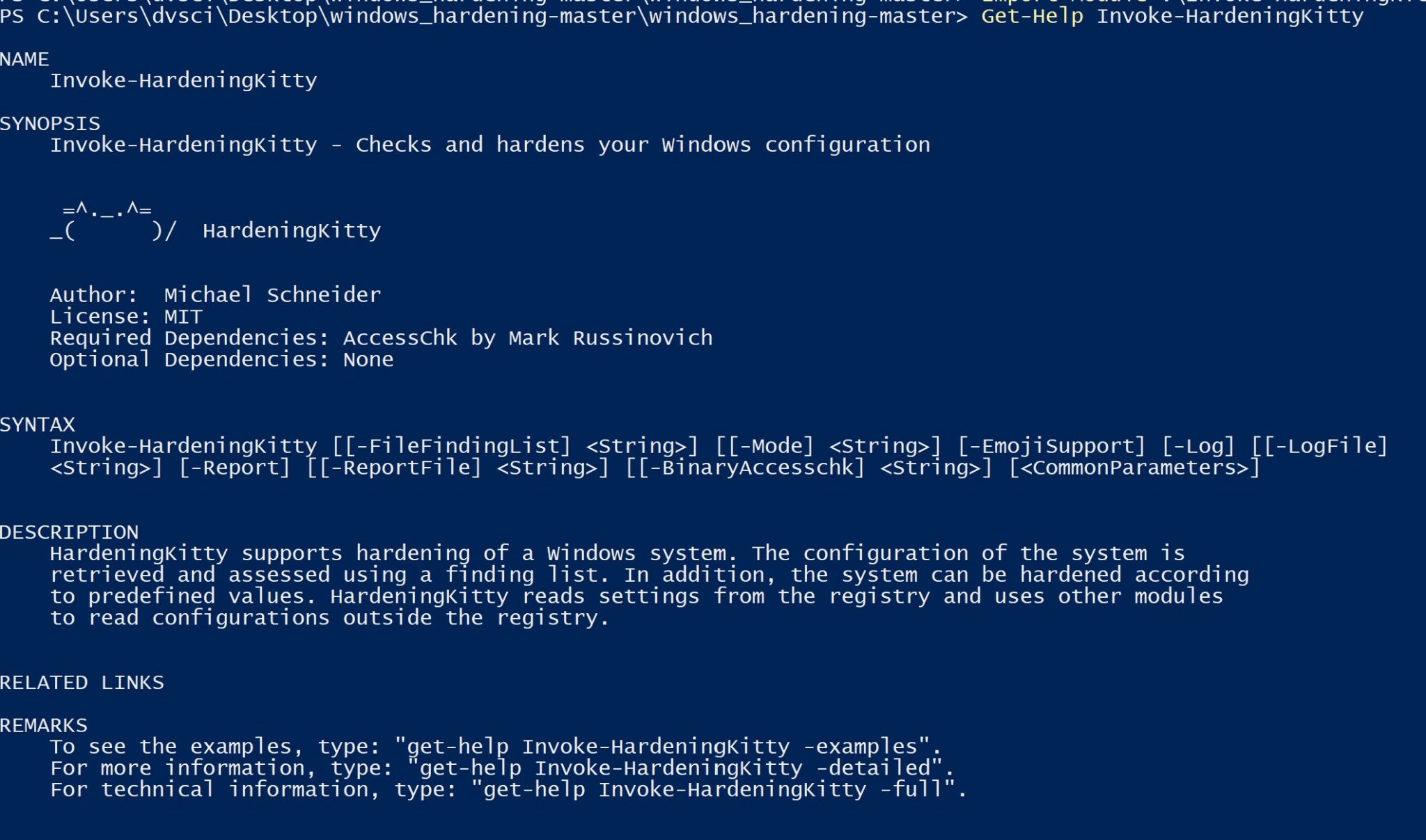
HardeningKitty
HardeningKitty supports the hardening of a Windows system. The configuration of the system is retrieved and assessed using a finding list. In addition, the system can be hardened according to predefined values. HardeningKitty reads settings from the registry and uses other modules to read configurations outside the registry.
Attention: HardeningKitty has a dependency on the tool AccessChk by Mark Russinovich. This must be present on the computer and defined in the script accordingly.
The script was developed for English systems. It is possible that in other languages the analysis is incorrect. Please create an issue if this occurs.
HardeningKitty can be used to audit systems against the following baselines/benchmarks:
| Name | System Version | Version |
|---|---|---|
| 0x6d69636b (Machine) | 2009 | |
| 0x6d69636b (User) | 2009 | |
| CIS Microsoft Windows 10 Enterprise (Machine) | 2004 | 1.9.1 |
| CIS Microsoft Windows 10 Enterprise (User) | 2004 | 1.9.1 |
| CIS Microsoft Windows Server 2019 (Machine) | 1809 | 1.1.0 |
| CIS Microsoft Windows Server 2019 (User) | 1809 | 1.1.0 |
| Microsoft Security baseline for Microsoft Edge | 87 | Final |
| Microsoft Security baseline for Windows 10 version 2004 | 2004 | Final |
| Microsoft Security baseline for Windows 10 version 2009 | 2009 | Final |
| Microsoft Security baseline for Windows Server version 2004 (DC) | 2004 | Final |
| Microsoft Security baseline for Windows Server version 2004 (Member) | 2004 | Final |
| Microsoft Security baseline for Windows Server 10 version 2009 (DC) | 2009 | Final |
| Microsoft Security baseline for Windows Server 10 version 2009 (Member) | 2009 | Final |
| Microsoft Security baseline for Office 365 ProPlus (Machine) | Sept 2019 | Final |
| Microsoft Security baseline for Office 365 ProPlus (User) | Sept 2019 | Final |
Changelog v0.9.2
Update HardeningKitty
[*] Add new finding lists and update existing
[*] Improve documentation
Download & Use
Copyright (c) 2017 Michael Schneider