evil-winrm v3.5 releases: Windows Remote Management shell for pentesting
Evil-WinRM
This shell is the ultimate WinRM shell for hacking/pentesting.
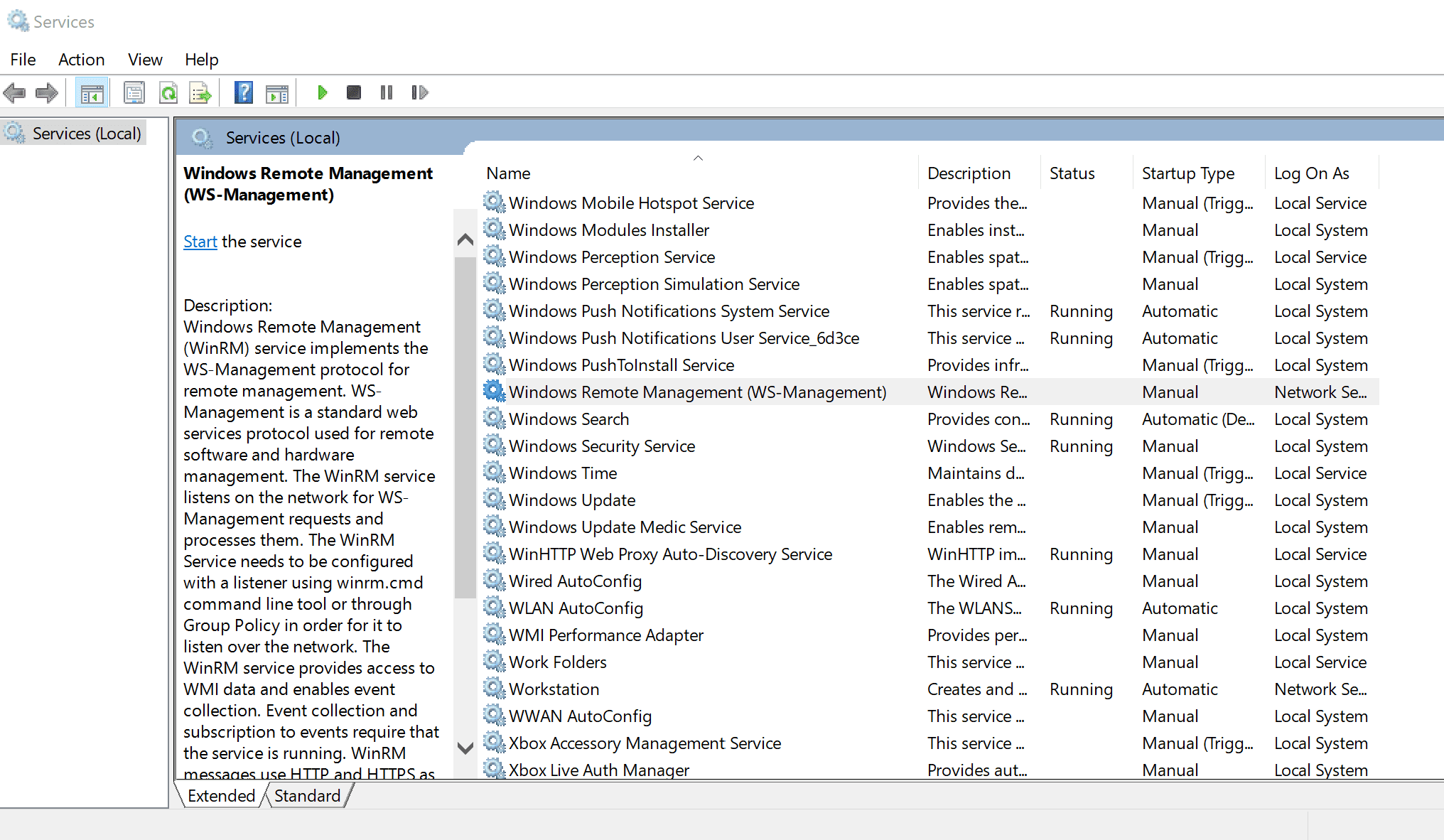
WinRM (Windows Remote Management) is the Microsoft implementation of the WS-Management Protocol. A standard SOAP-based protocol that allows hardware and operating systems from different vendors to interoperate. Microsoft included it in their Operating Systems in order to make life easier to system administrators.
This program can be used on any Microsoft Windows Servers with this feature enabled (usually at port 5985), of course only if you have credentials and permissions to use it. So we can say that it could be used in a post-exploitation hacking/pentesting phase. The purpose of this program is to provide nice and easy-to-use features for hacking. It can be used for legitimate purposes by system administrators as well but most of its features are focused on hacking/pentesting stuff.
It is based mainly in the WinRM Ruby library which changed its way to work since its version 2.0. Now instead of using WinRM protocol, it is using PSRP (Powershell Remoting Protocol) for initializing runspace pools as well as creating and processing pipelines.
Features
- Compatible to Linux and Windows client systems
- Load in memory Powershell scripts
- Load in memory dll files bypassing some AVs
- Load in memory C# (C Sharp) assemblies bypassing some AVs
- Load x64 payloads generated with awesome donut technique
- Dynamic AMSI Bypass to avoid AV signatures
- Pass-the-hash support
- Kerberos auth support
- SSL and certificates support
- Upload and download files showing progress bar
- List remote machine services without privileges
- Command History
- WinRM command completion
- Local files/directories completion
- Remote path (files/directories) completion (can be disabled optionally)
- Colorization on prompt and output messages (can be disabled optionally)
- Optional logging feature
- Docker support (prebuilt images available at Dockerhub)
- Trap capturing to avoid accidental shell exit on Ctrl+C
Changelog v3.5
- Improvements on powershell functions loading
- Improvements on gemspec file and in ruby code using Rubocop (Thanks noraj)
- Fixed issues with download and upload commands
- Added support for simple wildcard usage in upload and download commands
- Fixed non-controlled error on wrong certificates path when SSL enabled
- Docker image improved to support remote path completion
Install & Use
Source: https://github.com/Hackplayers/