wpscan v3.8.25 releases: black box WordPress vulnerability scanner
WPScan
WPScan is a free, for non-commercial use, black box WordPress security scanner written for security professionals and blog maintainers to test the security of their sites.
WPScan is written in the Ruby programming language. The first version of WPScan was released on the 16th of June 2011.
What can WPScan check for?
- The version of WordPress installed and any associated vulnerabilities
- What plugins are installed and any associated vulnerabilities
- What themes are installed and any associated vulnerabilities
- Username enumeration
- Users with weak passwords via password brute forcing
- Backed up and publicly accessible wp-config.php files
- Database dumps that may be publicly accessible
- If error logs are exposed by plugins
- Media file enumeration
- Vulnerable Timthumb files
- If the WordPress readme file is present
- If WP-Cron is enabled
- If user registration is enabled
- Full Path Disclose
- Upload directory listing
- And much more…
Install
Requirement
- Ruby >= 2.2.2 – Recommended: 2.3.3
- Curl >= 7.21 – Recommended: latest – FYI the 7.29 has a segfault
- RubyGems – Recommended: latest
From RubyGems:
gem install wpscan
From sources:
Prerequisites: Git
git clone https://github.com/wpscanteam/wpscan
cd wpscan/
bundle install && rake install
Usage
Open a terminal and type wpscan –help (if you built wpscan from the source, you should type the command outside of the git repo)
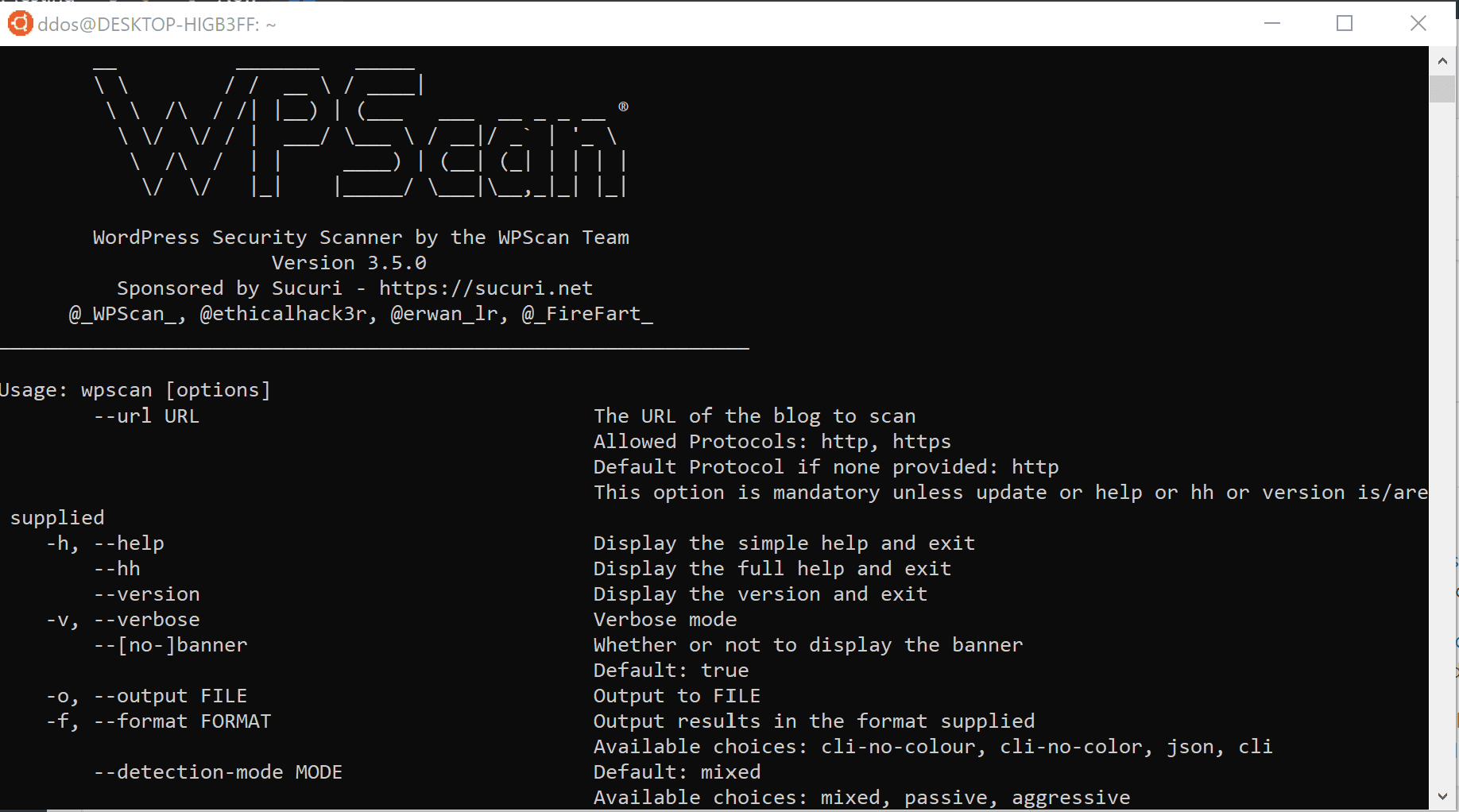
The DB is located at ~/.wpscan/db
WPScan can load all options (including the –url) from configuration files, the following locations are checked (order: first to last):
-
~/.wpscan/cli_options.json
-
~/.wpscan/cli_options.yml
-
pwd/.wpscan/cli_options.json
-
pwd/.wpscan/cli_options.yml
If those files exist, options from them will be loaded and overridden if found twice.
e.g:
~/.wpscan/cli_options.yml:
proxy: ‘http://127.0.0.1:8080’
verbose: true
pwd/.wpscan/cli_options.yml:
proxy: ‘socks5://127.0.0.1:9090’
url: ‘http://target.tld’
Running wpscan in the current directory (pwd), is the same as wpscan -v –proxy socks5://127.0.0.1:9090 –url http://target.tld
Copyright 2011-2018 WPScan Team.
Source: https://github.com/wpscanteam/