Your car spies on you: a malware against your privacy
The introduction of ICT systems in vehicles, such as the driving and parking assistant, Internet connectivity, and in general all the cyber-physical features installed in cars, could pose risks in terms of security and data privacy of the driver, comparable to those now known by personal computers.
One of the main issues is the ability to know personal information and vehicle data, such as fuel consumption, oil level, handbrake operation, and so on, made voluntarily and illegally public outside or stolen through computer attacks on vehicle communication systems.
In fact, by accessing the internal communication network of the car (Controller Area Network – Can bus) it is possible to read the data exchanged among the control units, modify them, replicate them and/or block them, thus causing various problems; from the slightest, how to provide the driver with incorrect information about some vehicle consumption data, to tamper with the car’s brakes by blocking the messages before they reach the control units.
CANDY: an attack on the Android Infotainment systems
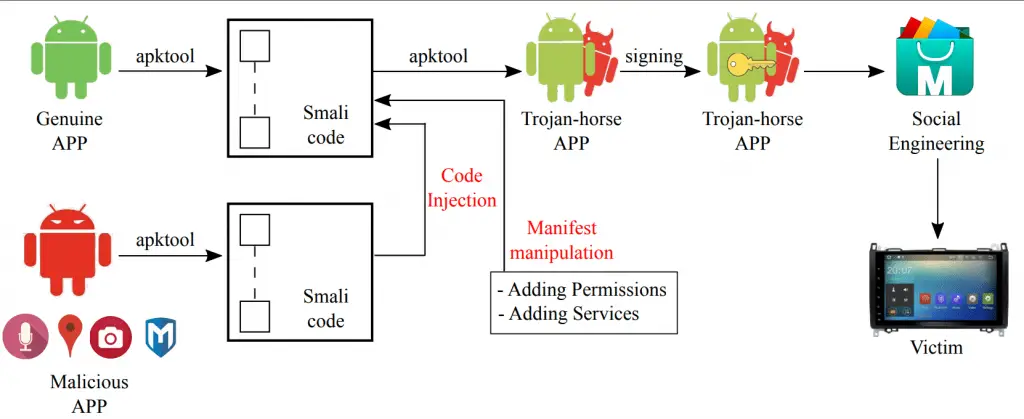
Vehicles that use the In-Vehicle Infotainment (IVI) based on the Android operating system and connected to the CAN bus, can provide access points to unauthorized users. So, installing applications from not official stores could hide malware that allows remote access to the infotainment device.
To study its effects, we developed a malware, which exploits a social-engineering diffusion mechanism, and once it is installed in the victim vehicle and accesses services, such as, car internal microphone, parking cameras, GPS positions, and CAN network, in an unauthorized way.
Our target system is an Android Radio with Android 4.4 KitKat. The radio is installed on a can that is connected to the CAN bus network through a CAN bus-decoder that allows the radio to show a set of vehicle’s information through apposite APPs. The radio is connected to the Internet through a 3G dongle. The permanent Internet connection guarantees a high-level of coverage and allows the driver to have features similar to those of smart-phones, such as messaging, e-mails, surfing the Web, installing APPs and so on.
We designed and developed an App Android that acts as a Trojan-horse in the Infotainment system. To use an appealing Trojan-horse APP for the victim, we chose an APP that shows gas stations close to the vehicle. To make the attack more sophisticated, we injected into the Trojan-horse APP additional code whose scope is to steal driver and vehicle information.

When the Trojan-horse App is executed, the back-door is opened and in parallel, the microphone of the infotainment system starts recording the conversation that occurs inside the vehicle. When the attacker wants to retrieve the recordings, the GPS coordinates, and the images, she uses a remote shell, embedded in the malware payload, to download the files.
In addition, the attacker, through the same shell, is able to interact with the Android system mining the privacy of the user by spoofing the information circulating on the CAN bus about vehicle attributes. In fact, this attack violates the confidentiality of the messages exchanged in the CAN bus network since these messages are not encrypted. The exchanged messages through ECUs contain information related to the vehicle, for instance, parking sensors, car doors opened, engine information and so on.

Conclusion
CANDY allows an attacker to violate the privacy of a user by stealing her private information stored on the infotainment system. In addition, the malicious APP is able to track the position of the vehicle and, consequently of all its passengers by using the remote shell.
More Info on this YouTube video
Contacts:
– Gianpiero Costantino – gianpiero.costantino@iit.cnr.it
– Ilaria Matteucci – ilaria.matteucci@iit.cnr.it
Istituto di Informatica e Telematica (IIT)- Consiglio Nazionale Delle Ricerche (CNR) – Pisa, Italy





