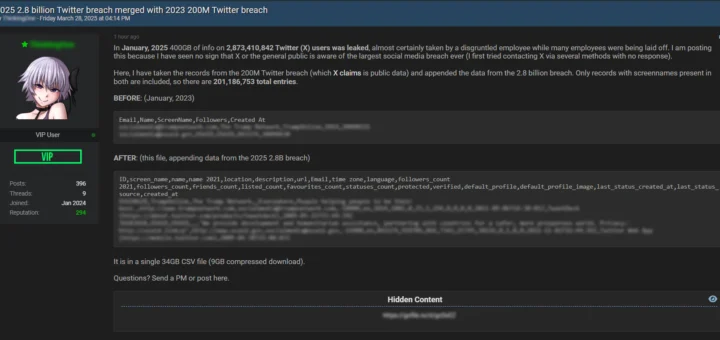
In a significant cybersecurity incident, several major Australian pension funds have confirmed they were targeted in a...
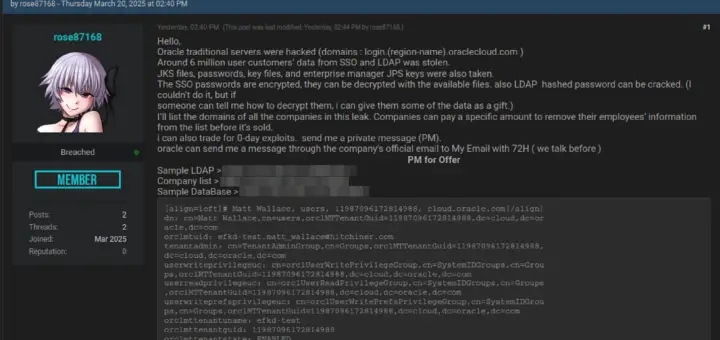
Oracle Corporation has recently disclosed a second cybersecurity breach within a month, involving unauthorized access to a...
The OpenVPN community has released a critical security update — OpenVPN 2.6.14 — to patch a server-side...
Apache Traffic Server (ATS), a widely adopted and high-performance HTTP proxy server, has been identified as vulnerable...
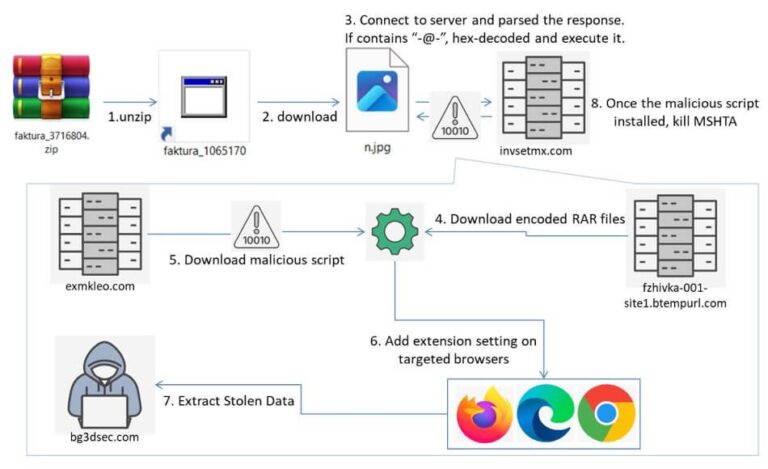
Web-based credit card skimming remains a persistent and evolving threat, and FortiGuard Labs has recently uncovered a...
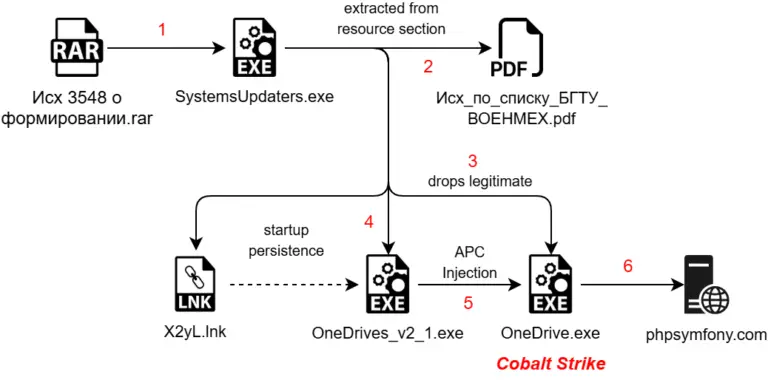
A recent report by SEQRITE Labs APT-Team has shed light on a sophisticated campaign, dubbed Operation HollowQuill,...
A recently discovered malicious Python package on the Python Package Index (PyPI) named “disgrasya” has been found...
A recent analysis by the AhnLab Security Intelligence Center (ASEC) has uncovered a particularly insidious campaign involving...
Cisco has released security advisories addressing vulnerabilities in its Enterprise Chat and Email (ECE) product and its...
Ivanti has recently disclosed a critical security vulnerability, identified as CVE-2025-22457, affecting several of its widely-used products....
A newly disclosed vulnerability in WinRAR, the world’s most widely used file compression tool with over 500...
The Wikimedia Commons project, an integral part of the Wikipedia ecosystem, is currently under siege by an...
Google’s password manager within the Android operating system now supports the use of passkeys—offering users a more...
As the deadline imposed by the Trump administration for TikTok’s U.S. operations to resolve their future approaches,...
A security vulnerability in the Verizon Call Filter iOS app allowed attackers to potentially leak the call...